User Access Reviews
Automate User Access Reviews
Automates user access reviews across all your applications, eliminating manual effort and spreadsheet fatigue.Gain real-time visibility, faster certifications, and continuous compliance with an automated review workflow.
Discover An Automated Alternative For User Access Reviews
SecurEnds’ holistic identity and infrastructure governance platform provides organizations with a single unified view across platforms, including cloud and on-premises. Our solutions reduce audit fatigue and security risk so organizations can document their answers to the critical questions of “who has access to what?” and “what is our security risk?”

Establish a clean set of user entitlement data to support risk and compliance efforts.
Increase compliance efficiency by streamlining certification.
Automate data and controls ingestion and approval workflows.
Interactive, identity-centric view across IT risks, applications, and entitlements.
Out-of-the-box application support and IT controls.
SaaS-based platform for rapid delivery for quick time-to-value.
Still doing User Access/Entitlement Reviews Manually?
User Access Reviews are an important control activity required for internal and external IT security audits. Done monthly or annually manual User Access and Entitlement Reviews can be tedious and cumbersome.
SecurEnds automates User Access reviews, putting CISOs and Security department in control of users’ entitlements across a today’s hybrid IT system. Continuous access certification also enables continuous control.
Automate User Access And Entitlement Reviews
Key Features
Credential Entitlement Management (CEM) for User Access Reviews
SecurEnds Credential Entitlement Management (CEM) product addresses user access reviews that grants enforce, revokes and administers fine-grained access entitlements (also referred to as “authorizations,” “privileges,” “access rights,” “permissions” and/or “rules”). Its purpose is to review IT access policies to structured/unstructured data, devices and services from various endpoints including:
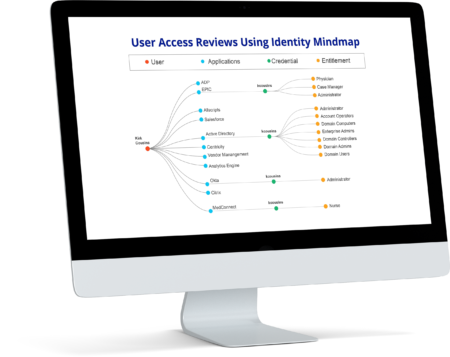
Know Who Has Access to What – With Absolute Clarity
Manual User Access Reviews are error prone and known to lead to audit findings on compliance standards such as SOX, HIPAA, FISMA, GLBA and PCI-DSS.
Key Problems
SecurEnds Solution
Using manual methods such as Excel for conducting user access reviews can lead to inefficiencies and errors.
Struggling to achieve a complete and accurate user access review
Lack of visibility into pending tasks and responsible individuals can hinder effective access management and timely compliance.
Identify the right reviewer for each access review to ensure accurate and compliant access management.
Overcome challenges in accessing and retrieving user data from endpoints such as Active Directory, Office 365, SharePoint, Windows, AWS, Azure, Google G Suite, Salesforce, SAP, and more.
SecurEnds CEM Fixes the Gap in Your Security Stack.
We offer on-premise and cloud offering of our products.
Our products will be configured to provide a solution for your organization
Automate user access rights with a simple workflow
Consolidate enterprise-wide user privileges in a central location
Make your access data more secure to meet compliance regulations
Monitor, track, analyze, and report unauthorized access attempts in real-time.
Generate cross-application rules for separation of duties that trigger real-time alerts
Issue proactive alerts to monitor for sensitive privileges, users, or applications

Accurate Review
Provides an easy solution with complete and accurate review of user access.
Controlled Securely
Ensure your organization is in compliance and user access is controlled securely.
Security Stack
Coordinate and execute user access reviews to fix the gap in your Security stack.

Schedule a Product Demo
Submit your details, and our technical representative will contact you to arrange a personalized demo of our product. Experience its features firsthand and see how it can benefit your business!
Frequently Asked Questions
User access Review(UAR) is an anchor of enterprise data and is like a regular checkup for your organization’s digital security. It is an effective process ensuring only the right and confidential people have access to the company’s data and systems.
The goal of this review process is to reduce the risk of unauthorized use and inappropriate privileges with access and to make sure that permission is granted to those who access the organization’s data, applications, and networks.
User access reviews are vital for protecting sensitive data in today’s digital world. Regular checks ensure only authorized users have access, minimizing risks and enhancing security.
- Boosts Security: Regular checks make sure only the right people can access sensitive information, keeping your systems safe.
- Prevents Mistakes: By removing outdated access, you lower the chance of accidental or intentional data breaches.
- Keeps You Compliant: Ensures you’re following rules and regulations.
- Simplifies Access Control: Helps avoid confusion by making sure only those who need access have it.
User access review for AWS helps safeguard sensitive data by periodically checking the access rights of various users, including root users, IAM users, IAM Identity Center users, and federated identities, ensuring efficient and secure management of AWS accounts.
User access review for AWS ensures proper permissions by auditing IAM users, roles, and policies. Regular audits and assessments performed at regular intervals can identify overly permission users, mitigate potential security risks and maintain a secure and compliant AWS environment.
Various regulations guide user access reviews to ensure security and compliance. Key frameworks include:
- SOX (Sarbanes-Oxley Act): Requires access audits and segregation of duties to protect financial data.
- ISO 27001: Focuses on information security management and access control.
- PCI DSS (Payment Card Industry Data Security Standard): Mandates bi-annual access reviews for cardholder data protection.
- HIPAA (Health Insurance Portability and Accountability Act): Requires secure access to health information.
- HITRUST: Combines multiple security standards to secure healthcare and other sensitive data.
- FFIEC (Federal Financial Institutions Examination Council): Emphasizes access controls for financial institutions.
- Complex Systems: Large companies struggle with managing user access across diverse platforms and applications, creating review complexity.
- Operational Disruption: Balancing reviews with business continuity often creates delays and operational friction.
- Stakeholder Pushback: Department heads and users may resist changes, fearing reduced access or workflow interruptions.
- Inconsistent Access: Departments control different access levels, leading to fragmented processes and gaps.
Role Changes: Tracking role transitions and ensuring timely offboarding often leads to excessive permissions and orphaned accounts.
- Automate user access rights with a simple workflow
- Consolidate enterprise-wide user privileges in a central location
- Make your access data more secure to meet compliance regulations.
- Monitor, track, analyze, and report unauthorized access attempts in real time.
- Generate cross-application rules for separation of duties that trigger real-time alerts.
- Issue proactive alerts to monitor for sensitive privileges, users, or applications.
- Periodic user access: This user access is also called a scheduled access review. It is conducted at set intervals to evaluate and update user permissions, ensuring they align with their current roles.
- Continuous user access: This is known as ongoing access monitoring. This type of constant user access process ensures compliance and reduces the risk of unauthorized access, keeping your systems secure at all times.
- Clear with your objective
Who needs to access your organisation? Be clear on who can access your systems and data. Make a detailed list of stakeholders(employees, partners, vendors) and authorise the level of permission they have for what they can do with your enterprise data. - Set Clear Rules for Access
Identify who requires access and what actions they can perform. Some individuals may only need to view information, while others may need to modify data or initiate tasks. These permissions should be tailored to each person’s role and responsibilities within the organization. - Review Regularly
Sit down with managers and IT teams to verify if the access still makes sense. Check if anyone has access they don’t need anymore—like an old vendor or an ex-employee who’s been gone for months. Focus more frequently on high-risk areas, while others can be reviewed less often. - Educate Your Team on Access Risks
Teach your team why access control is important—highlight risks like data breaches and misuse. Use relatable examples or success stories to show how proper controls have made a difference. Tailor this training to their roles so it’s practical and not overwhelming. - Adopt “Need-to-Know” Access Practices
Give people only the access they truly need, based on their roles (Role-Based Access Control). Avoid granting broad permissions to “make things easier.” It’s safer to start with the least amount of access and add more if needed later. - Learn and Adjust After Each Review
After every review, analyze what worked and what didn’t. Did you find recurring mistakes, like granting too much access? Use these findings to fine-tune your processes. Keep improving so the next review is smoother and more efficient.
- Compliance with Regulations: User access reviews are vital for adhering to laws like SOX, HIPAA, PCI DSS, and GDPR, ensuring organizations meet security standards and protect sensitive data.
- Minimize Security Risks: Regular access reviews help identify and remove unnecessary permissions, reducing the risk of data breaches and unauthorized access.
- Improve Operational Efficiency: Streamlined access controls enhance productivity by ensuring employees only have access to the resources they need.
- Audit Access: Start by mapping who has access to what resources across your organization.
- Least Privilege Principle: Ensure users only have access needed for their roles, minimizing unnecessary permissions.
- Automate Review Process: Use automation tools to streamline the review process and reduce errors.
- Regular Reviews: Establish a consistent schedule for reviewing user access, such as quarterly or annually.
- Employee Training: Educate employees on access management policies to promote compliance and security awareness.
- SecurEnds seamlessly integrates with cloud and on-premise applications, securely syncing users and roles via connectors or CSV file uploads.
- Creates a consolidated user identity database and automates user access reviews for all employees, contractors, and partners within your organization.
- SecurEnds simplifies integration by reducing complex development with built-in and custom connectors, allowing you to connect your applications quickly.
- Set up and manage recurring campaigns to perform access reviews, ensuring users always have the right access.
- Management dashboard enables reviewers and managers to perform access reviews across all applications efficiently.
- Easily update access review changes in applications with built-in connectors to ServiceNow, Jira, Email, and more.
- Easily manage campaign lifecycle with escalation to managers who haven’t performed reviews and delegate access reviews if a manager is unavailable.
- Provides audit reports and a dedicated auditor dashboard for access compliance attestation and certification.
- Accurate Review
Provides an easy solution with a complete and accurate review of user access. - Controlled Securely
Ensure your organization is in compliance and user access is controlled securely. - Security Stack
Coordinate and execute user access reviews to fix the gap in your Security stack. - Save Time and Money
Reducing manual processes saves your organization time and money.
- Compliance with Regulations: User access reviews are vital for adhering to laws like SOX, HIPAA, PCI DSS, and GDPR, ensuring organizations meet security standards and protect sensitive data.
- Minimize Security Risks: Regular access reviews help identify and remove unnecessary permissions, reducing the risk of data breaches and unauthorized access.
- Improve Operational Efficiency: Streamlined access controls enhance productivity by ensuring employees only have access to the resources they need.
What Is a User Access Review
A user access review process is a periodic assessment to verify that every employee, contractor, or system identity has the appropriate access rights for their current role.
The goal is to detect excessive, outdated, or orphaned permissions that could expose the organization to insider threats or compliance violations.
A mature user access review process typically includes:
- Defining the scope – which systems, roles, and user groups to review.
- Collecting access data – gathering entitlements across cloud, SaaS, and on-premises applications.
- Reviewing and attesting – managers, owners, or auditors validate whether access is justified.
- Remediation – removing or adjusting unnecessary privileges.
- Reporting and audit readiness – documenting review outcomes to prove compliance with SOX, ISO 27001, HIPAA, and GDPR.
When automated with SecurEnds User Access Review Software, these steps become continuous and error-free—eliminating manual spreadsheets and missed deadlines.
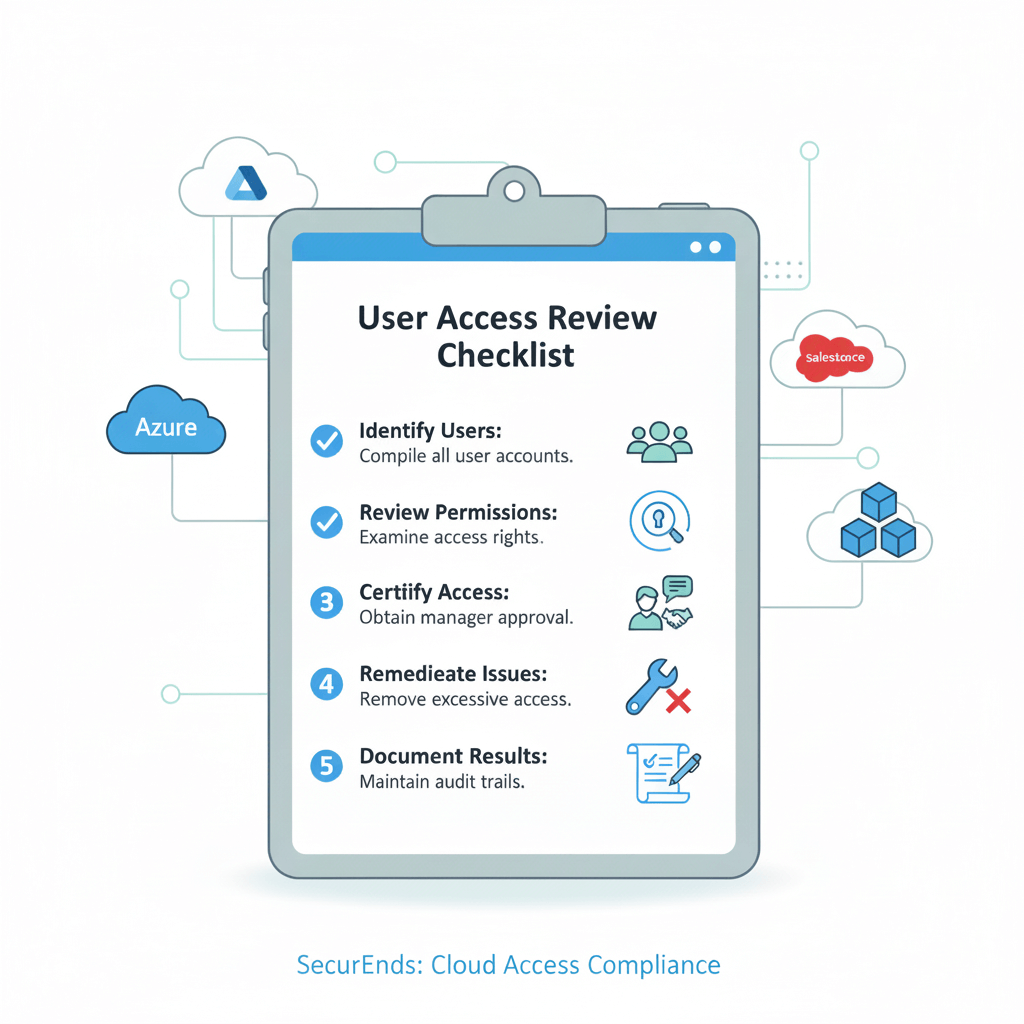
User Access Review Checklist for Compliance Teams
To maintain audit-ready compliance, organizations should conduct user access reviews using a repeatable and documented checklist.
Essential checklist items:
- Verify access lists for all applications, databases, and shared drives.
- Confirm managers or application owners are reviewing their own team’s access.
- Validate that privileged accounts are reviewed separately from standard users.
- Ensure terminated or transferred employees are fully deprovisioned.
- Cross-check SoD (Segregation of Duties) conflicts.
- Record approval or revocation actions within your review system.
- Generate final audit reports with timestamps and reviewer names.
With SecurEnds, compliance teams can complete this entire checklist automatically—cutting manual workload by 70% and improving review accuracy across AWS, Azure, and on-premise environments.
Common Challenges in Performing User Access Reviews
Even mature organizations struggle to execute timely and accurate access reviews. Common pain points include:
- Decentralized identity data: access information scattered across SaaS, on-prem, and Active Directory.
- Manual spreadsheets: collecting entitlement lists manually slows down cycles and invites human error.
- Lack of ownership: unclear responsibility between application owners, IT admins, and compliance teams.
- Audit fatigue: recurring quarterly reviews overwhelm managers, delaying certification.
- Inconsistent evidence: missing or incomplete review records risk compliance penalties.
SecurEnds addresses these challenges through centralized identity data collection, automated reminders, and real-time dashboards — ensuring every review is fast, accurate, and auditable.
Best Practices for Conducting User Access Reviews
To improve both security and audit outcomes, organizations should follow these user access review best practices:
- Adopt role-based access control (RBAC): limit entitlements based on job functions to simplify reviews.
- Use automated scheduling: set quarterly or semi-annual reviews with automatic notifications and follow-ups.
- Integrate HR systems: automatically update access based on employee join/move/leave events.
- Prioritize high-risk applications: focus review frequency on systems with sensitive or financial data.
- Maintain audit evidence: store certifications, revocations, and reviewer comments within your IGA tool.
- Close the loop: ensure revoked access is actually removed from connected systems.
Following these practices with SecurEnds’ automation engine helps enterprises not only meet compliance mandates but also maintain continuous least-privilege enforcement.















