User Access Management
User Access Management
Master user access with confidence and clarity.

Organisations are frequently exposed to security breaches and the loss of sensitive information due to unauthorised access. Managing an extensive number of access controls presents challenges in access management, complicates the tracking of user activity, and hampers efficient compliance maintenance. User access management solutions streamline and administer access controls while restricting access permissions to secure organisations from inefficient access management and security threats.
What is User Access Management?

User Access Management (UAM) is a security framework that leverages tools and pre-defined policies to protect access to an organisation’s systems, resources, and applications. Based on the roles, identity, location, working hours, devices, and access levels, UAM minimises the risk of unauthorised access to sensitive data, applications, and systems. It integrates key security mechanisms like authentication, authorisation, and monitoring to enforce secure access control.
Benefits of User Access Control
Safeguards your data
User Access control mitigates unauthorised users from editing, commenting, viewing, or manipulating your data and resources unless they obtain correct authorisation. By restricting access through the principle of least privilege (PoLP), user access control manages to provide approximately necessary access to perform the task, reducing misusage, potential breach, and insider threat.
Adherence to Compliances
Concerning data protection, the majority of industries are obligated to adhere to regulatory compliances like GDPR, HIPAA, PCI DSS, and SOX. UAC assists organisations in satisfying regulatory requirements for data protection and secure access, all while avoiding legal penalties.
Cost Efficiency
By reducing the likelihood of security incidents and streamlining the management of user accounts, organisations can reduce the costs associated with data breaches, reputational damage, data recovery, legal expenditures, and administrative overhead related to managing user permissions.
Streamlines process
Automation of tasks like identifying, verifying, and reviewing access from onboarding to offboarding of users streamlines IT operations, optimising time and reducing errors. Employees can access resources faster and safer with Single Sign-On (SSO), boosting productivity.
Secure Your Business with Our Effective User Access Control

With expertise over 10 years, SecurEnds has commanded excellence in every aspect of digital security. During this time, we have grown into a trusted provider of user access management and governance solutions, focusing on automating IAM processes, enhancing security, and ensuring compliance for organisations across various industries. Businesses can view the users of the data, set policies, and grant permissions to their resources to establish robust security and compliance.
Key Features of Our User Access Management Solutions
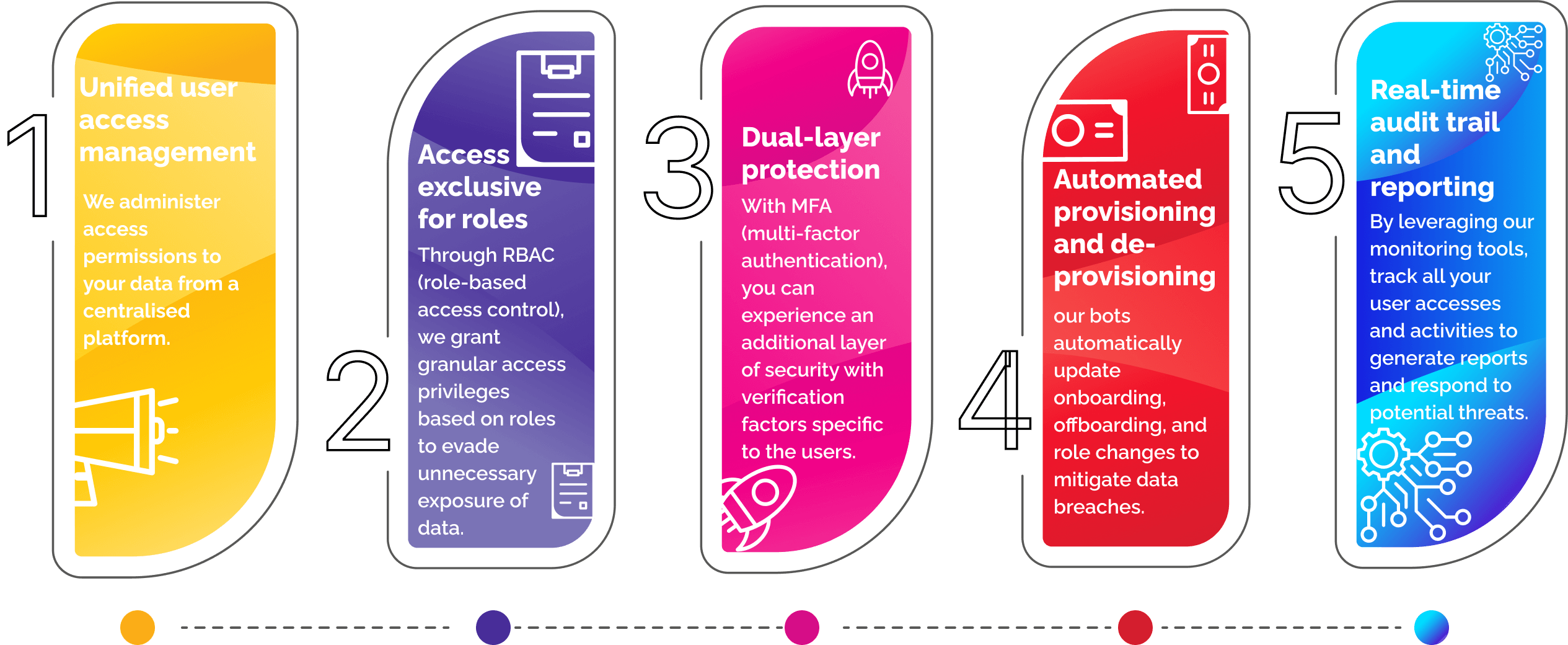
Why do organisations need a user identity management solution?
Leverage our User Identity Management solutions to manage user identities and access controls to guarantee security, compliance, and efficiency across their IT environment.
Prevents security breaches
Ensures compliance
Monitors user access and activities
Efficient IT operations
Reduces manual error
How Does Our User Access Review Help Your Organisation?

SecurEnds’ User Access Review feature automates the process of periodically reviewing and certifying user access, ensuring that permissions are aligned with current roles.
Reduces Security Risks
Identifies and mitigates potential security vulnerabilities by regularly reviewing and adjusting user access rights.
Improves Compliance
Assures compliance with relevant regulations and industry standards by maintaining accurate and up-to-date access controls.
Enhances Efficiency
Streamlines the user access review process, saving time and resources for IT teams.
Increases Visibility
Provides valuable insights into user access patterns and identifies any anomalies or suspicious activity.
Minimises Business Disruptions
Prevents service outages and data breaches by proactively addressing security gaps.
How Our User Access Management Solution Works in SecurEnds
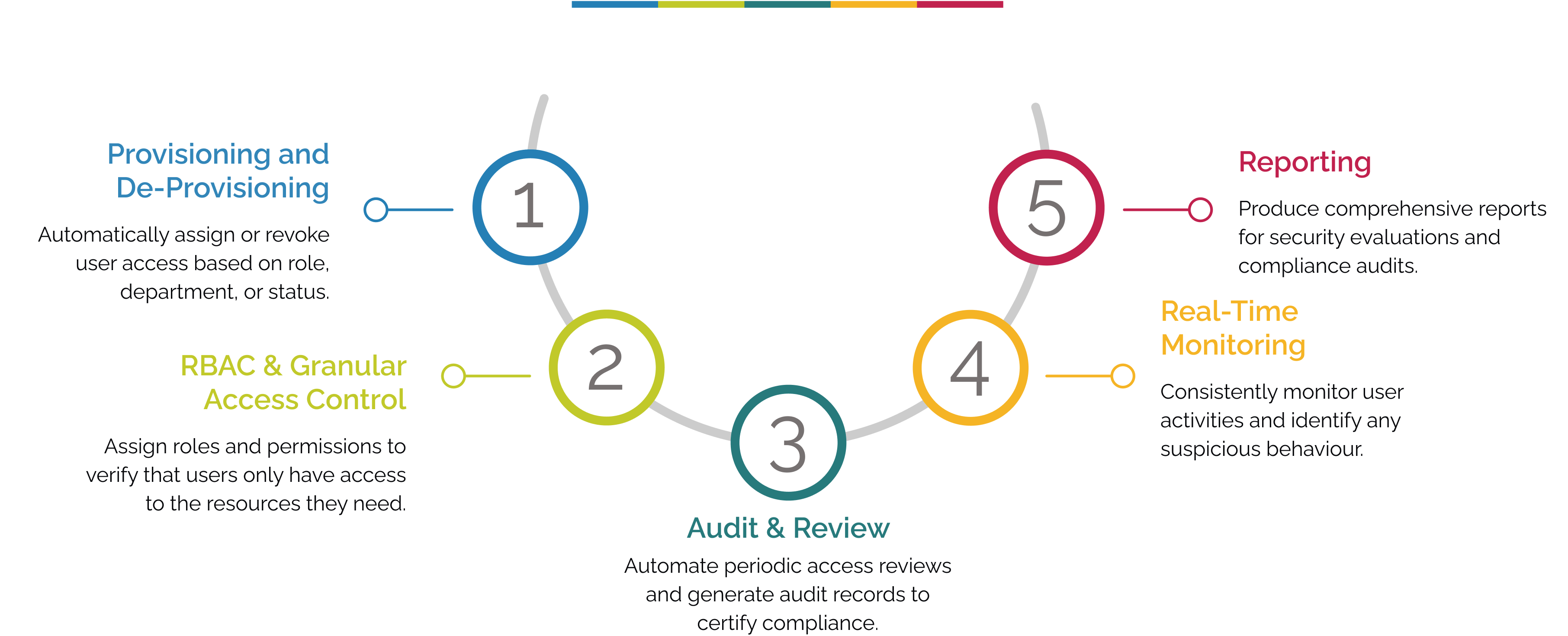
Why Choose Us?
Expertise and Experience
Our team of experts has years of experience in designing and implementing robust user access management solutions.
Customer-Centric Approach
We prioritise our customer’s needs and tailor our solutions to meet their specific requirements.
Groundbreaking Technology
We leverage the latest technologies to provide advanced security features and a seamless user experience.
Competitive Pricing
We offer competitive pricing and flexible subscription options to suit different budgets.
Excellent Support
Our dedicated support team provides prompt and effective assistance to enhance customer satisfaction.
Control Access with SecurEnds
Frequently Asked Questions
UAM is the process of managing and controlling user access to systems and data within an organisation, ensuring only authorised users can access critical resources.
RBAC ensures that users have access only to what they need for their role, reducing security risks and simplifying compliance management.
Our solution automates the process of reviewing and confirming user access rights regularly, ensuring they are aligned with user roles and compliant with regulations.
Our solution is suitable for organisations of all sizes and industries, particularly those that need to comply with strict regulatory standards like healthcare, finance, and government.
Usually, access rights should be reviewed at least annually, but more frequent reviews may be necessary for critical systems and high-risk users.