NIST Cybersecurity Assessment
NIST Cybersecurity Framework
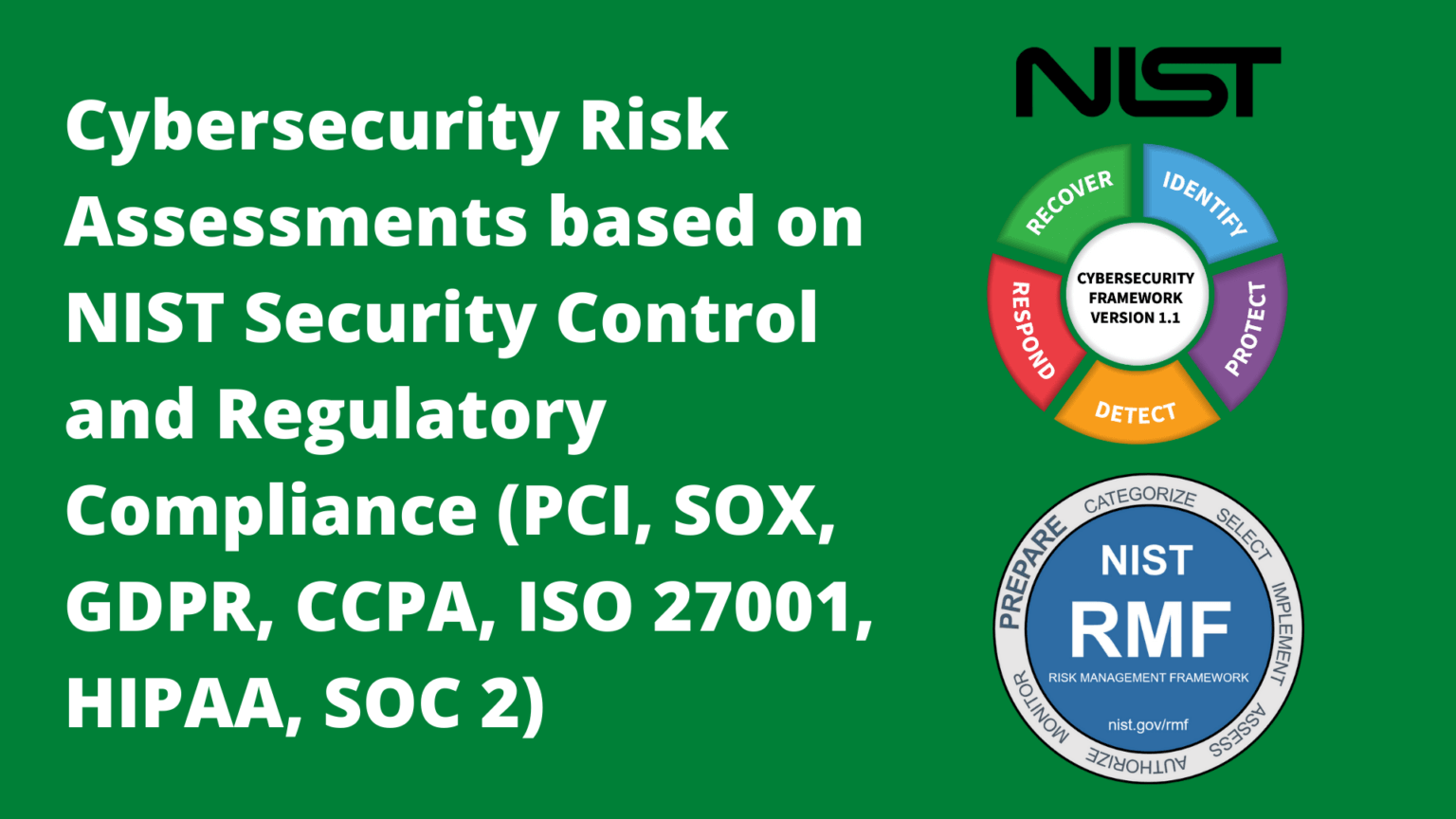
Integrated with the National Institute of Standards and Technology (NIST) Risk Management Framework (RMF) the NIST Cybersecurity Framework (CSF) includes widely accepted security and privacy controls. Many standard control sets, such as, NIST SP 800-53r5, ISO 27001, PCI DSS, HIPAA, CMMC, and others, are measured in the assessments and accurately mapped as informative references when viewed from the business perspective.
The NIST Cyber Security Framework focuses on controls addressed by five functions of security and lead the mapping for which all other control sets are messured for a concise Enterprise Security Posture.
SecurEnds GRC includes each component of the NIST CSF by incorporating the Framework Core, Tiers and Profiles. Mapping and measurement of the core controls and informative references allows a profile to be built to represent the current enterprise security profile. The outcome is a view of the cybersecurity risk management tier of the organization and the process to advance to a improved risk management capability.
To follow the NIST Cybersecurity Framework (CSF) standard, organizations have to enable a system of practices and processes that conform to the framework. This requires continuous assessment of system configuration changes, user access levels, and various IT activities. SecurEnds GRC pre-configured NIST CSF risk assessments allow insights into risks that threaten conformance with the NIST CSF. These assessments help engage all departments by automating the recurring tasks of collecting data and assigning risk. SecurEnds GRC maintains a detailed audit trail that enables organizations to capture all necessary information that arises out of an assessment. Out-of-the box ticketing integration with ServiceNow, Jira allows SecurEnds GRC close the loop in risk remediation.
Strategic Decisions
-
1Risk Program:
Implement an enterprise-wide risk assessment and remediation program -
2Proactive Risk Management:
Early warning metrics and analytics on technology and IT asset risks -
3Vendor Management:
A vendor risk management (VRM) or third-party risk management (TPRM) program.
Operational Decisions
-
1Risk Program:
Implement an enterprise-wide risk assessment and remediation program -
2Proactive Risk Management:
Early warning metrics and analytics on technology and IT asset risks -
3Vendor Management:
A vendor risk management (VRM) or third-party risk management (TPRM) program.
Tactical Decisions
-
1Risk Program:
Implement an enterprise-wide risk assessment and remediation program -
2Proactive Risk Management:
Early warning metrics and analytics on technology and IT asset risks -
3Vendor Management:
A vendor risk management (VRM) or third-party risk management (TPRM) program.

Schedule a Product Demo
In less than 30 minutes, you can see why customers and MSSPs are choosing our purpose build SaaS software to achieve assessments for SOC 2