Identity Lifecycle Management
Manage Identities and Privileges effectively
in 3 Steps with SecurEnds
Request, approve, provision, and de-provision user access for on-prem or cloud applications to improve user onboarding, offboarding, and self-service.
3 easy steps
Step 1: Create Identity Profiles
Build attribute-based profiles using pre-built templates to streamline the management of identities throughout their lifecycle. SecurEnds Identity Lifecycle Management can create identity templates across workforce profiles (e.g., employees, contractors, RPA accounts, service accounts) based on attributes (e.g., title, location, department).
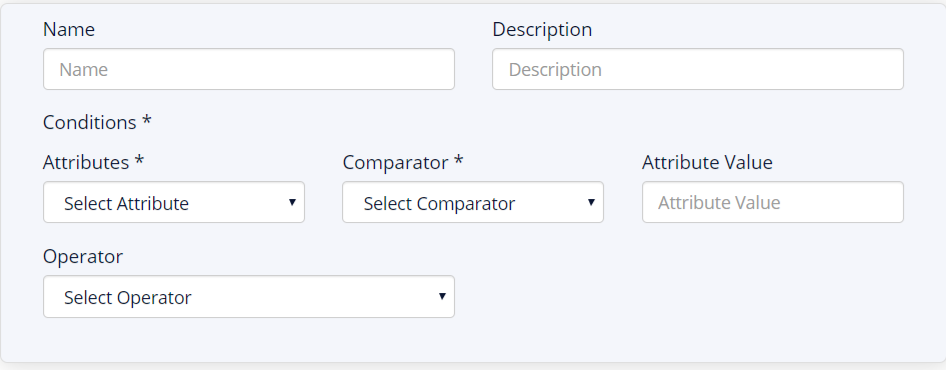
Step 2: Provision Access
Quickly create roles based on access requirements and permissions in the ILM application.
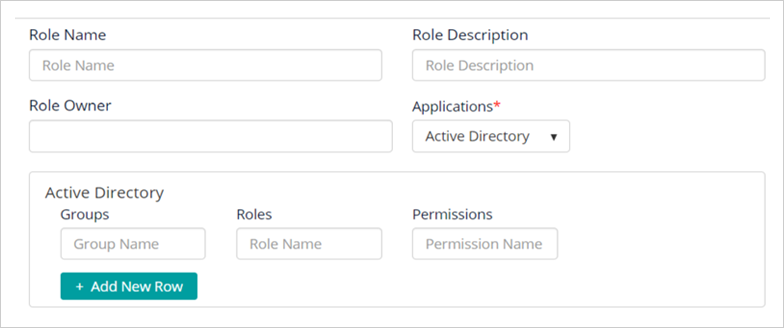
Step 3: Life Cycle Management
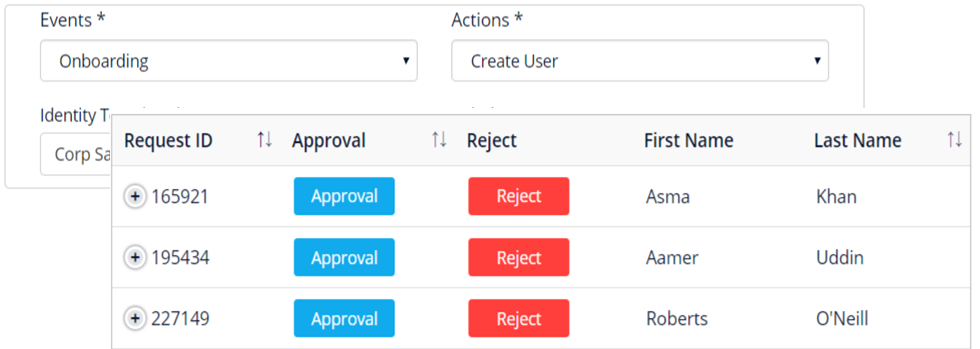
Automate user provisioning for lifecycle events such as on-boarding, off-boarding, and transfers. For provisioning and de-provisioning, identity roles will be associated with role profiles. End-users may also self-service requests while adhering to compliance policies.
Customer Success Story
Challenge
Epiq, a global leader in legal services with 80 offices and 7000 employees, had grown through multiple acquisitions. With 80+ active directories, there was a need for consolidation while ensuring auditors had access to evidence that employee controls were in place (e.g., ensuring accesses are disabled upon termination).
Testimonial
We were looking for a product that could help us manage a large amount of Access reviews after finishing a number of acquisitions. What we found was that SecurEnds could do much more than that. We've begun to use it for AD cleanup as well. We are now evaluating for Entitlement Management as well. SecurEnds was much less expensive than the other tools we evaluated on the market and had all of the functionality we were looking for. I'd recommend anyone in the market for Credential Entitlement Management take a look at SecurEnds.
Roger Hardgrove, Global CISO, Epiq Global.
Learn how SecurEnds CEM works.
Fill out the form below to get started.