After completing formal documents and having discussed desired outcomes with our team, it is onto the set up phase. Here is a list of actions taken during the set up of your new SecurEnds tool:
- Set up and understanding of instance
- Installation of SecurEnds agent *on premise only*
- Configure System of Record (SOR)
- Configure Applications
- Data Validation
Understanding your Instance
SecurEnds stands up organization specific instances. The domain will always be “companyname.securends.com” unless specified otherwise.
Your first interaction with SecurEnds will look like this:
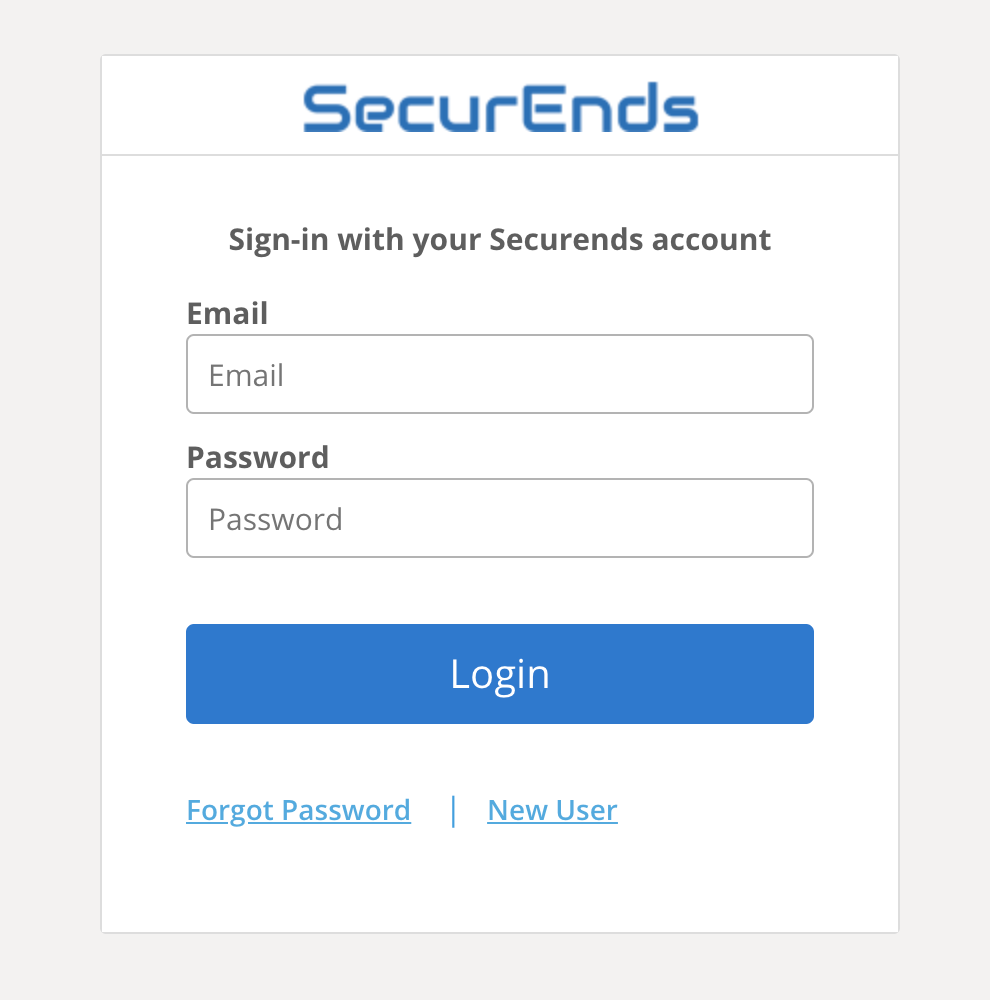
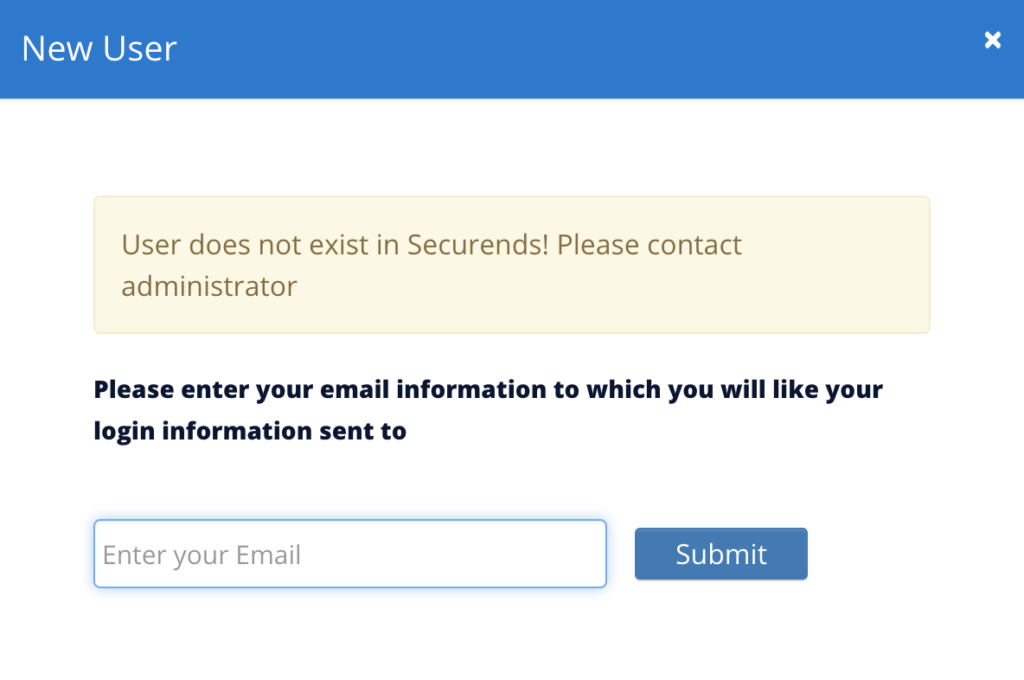
Selecting New User will prompt you to submit your email to which you will receive a link to set a password for your new account.
Note: New SecurEnds admins are to set up selected users and designated access to the user within the Peoples tab in the tool. Users can be provisioned SecurEnds access (ADMIN, APPLICATION, AUDIT, or ACCESS) within Configuration > Roles > Configure.
For more information regarding logging into your new instance please navigate to Login
Installation of SecurEnds Agent
In pre implementation, scope should be defined and decision to utilize and deploy our agent is determined. If deploying agent please see here for additional resources.
Configure System of Record (SOR)
Deciding the chosen SOR is key to successful reviews within SecurEnds. It can be a singular SOR or multiple as long as it is a comprehensive list of users within scope of upcoming reviews. Everything related to SOR information and set up is listed here.
Configure Applications
Applications in scope for review need to have their information brought into SecurEnds. This happens via connector, flex connector, or file upload. Documentation for each exists in this help center. During implementation, clients will need to designate application owners to own the notifications related to the application’s review.
Data Validation
We ask that you familiarize yourself with SecurEnds’ methods of data ingestion. We have a solution for ingesting information from all applications (on-prem, cloud / SaaS, homegrown, etc.) but each method is different. Know which application’s are going to be brought into SecurEnds and familiarize yourself with our variety of data ingestion methods.
Browse the list of SecurEnds connectors: here.
Data Validation Steps Performed by Client:
- Confirms imported data from CSVs and connectors are correct
- Performs data clean up if needed
- Matches unmatched records between application and SOR
- Excludes records not in scope
- Review any skipped records and remediate exceptions
Data Formatting
Data formatting is the foundation for bringing your data into SecurEnds, to do this efficiently, please follow the proper file upload formatting. We have a section dedicated to proper data formats and file types for proper upload into SecurEnds, in the event application data is best to be uploaded via .csv / excel file.
Many questions arise during implementations due to file formatting issues. We request you familiarize your team with SecurEnds file upload standards now so they can have greater success going forward.
Please see file formatting here.