Generic Agent
If you will be connecting to an on-premise version of Active Directory, then you will need to install the SecurEnds Generic Agent on a server that can communicate with your instance of Active Directory. Please refer to the Generic Agent install document here on requirements and instructions to install.
The following information is needed to connect with Active Directory
Clients can leverage details within this link for LDAP Syntax Filters – https://social.technet.microsoft.com/wiki/contents/articles/5392.active-directory-ldap-syntax-filters.aspx
- Schedule Import
- Selecting “ON Demand” will allow you to only sync when you need a refresh of the data prior to an access review
- Global Catalog URL
- The LDAP service provider uses a URL to configure the connection to the directory server. To generate the LDAP connection URL, we must specify the LDAP host, port and root.
- LDAP protocol is used to communicate with Active Directory on port 389.
- Format Example: LDAP://192.168.1.76/DC=CGISE,DC=local
- The LDAP service provider uses a URL to configure the connection to the directory server. To generate the LDAP connection URL, we must specify the LDAP host, port and root.
- Directory URL
- The LDAP service provider uses a URL to configure the connection to the directory server. To generate the LDAP connection URL, we must specify the LDAP host, port and root.
- LDAP protocol is used to communicate with Active Directory on port 389.
- Format Example: LDAP://192.168.1.76/DC=CGISE,DC=local
- ADUsername and AD Password
- Provide an account username and password that has the necessary access to fetch users
- Note: Domain needs to be appended to the end of the username for successful authentication.
- Provide an account username and password that has the necessary access to fetch users
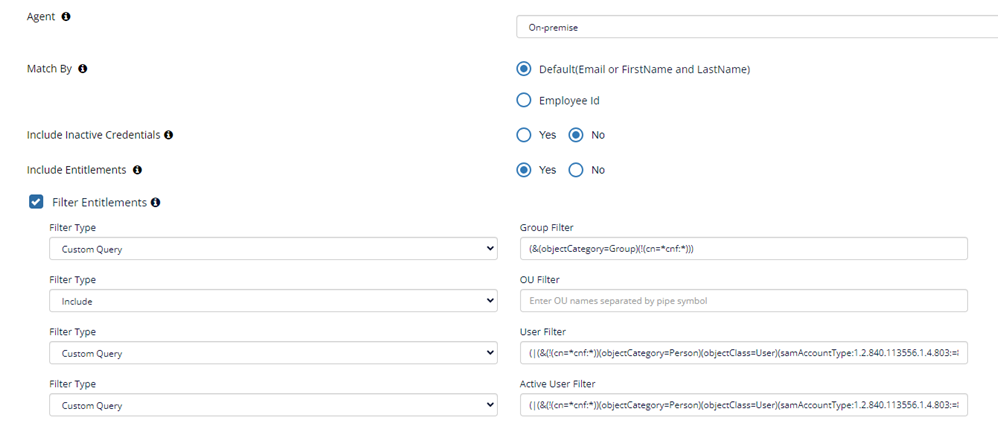
- UserFilter
- To fetch users or contacts we need to provide the user filter
- Format Example: (|(&(!(cn=*cnf:*))(objectCategory=Person)(objectClass=User)(samAccountType:1.2.840.113556.1.4.803:=805306368))(&(!(cn=*cnf:*))(objectCategory=Person)(objectClass=contact)))
- To fetch users or contacts we need to provide the user filter
- GroupFilter
- To fetch groups or roles we need to provide the Group Filter
- Format Example: (&(objectCategory=Group)(!(cn=*cnf:*)))
- To fetch groups or roles we need to provide the Group Filter
- Active Users Filter
- To fetch active users or contacts we need to provide the user filter
- Format Example: (|(&(!(cn=*cnf:*))(objectCategory=Person)(objectClass=User)(samAccountType:1.2.840.113556.1.4.803:=805306368)(!(userAccountControl:1.2.840.113556.1.4.803:=2)))(&(!(cn=*cnf:*))(objectCategory=Person)(objectClass=contact)))
- To fetch active users or contacts we need to provide the user filter
- Entitlement Owner Precedence ( Securends/Active Directory)
- This value is case sensitive
- Assignment of an Entitlement Owner for each entitlement will allow you to include the entitlement owner as a reviewer during a User Access Review campaign.
- You can leverage the SecurEnds tool to define this OR pull the actual owners from the Active Directory data.
- Enter Securends if you want to manually set the Entitlement Owner using the SecurEnds tool (do not use AD data).
- Enter Active Directory if you want to pull the Entitlement Owners from the Active Directory data during a sync.