Introduction to SCIM API: Simplifying Identity Management
Introduction to SCIM API: Simplifying Identity Management
As enterprises scale, managing user identities across multiple applications becomes increasingly complex. IT administrators need an efficient way to provision, update, and revoke access without manual intervention. This is where SCIM identity management plays a crucial role.
SCIM (System for Cross-domain Identity Management) is a standardized protocol that automates identity provisioning and de-provisioning. By leveraging SCIM provisioning, organizations can seamlessly manage user accounts across various platforms, ensuring compliance, security, and operational efficiency. This eliminates the burden of manual account management, reducing errors and enhancing overall security.
2. What is SCIM (System for Cross-domain Identity Management)?
SCIM is an application-level protocol that facilitates identity and access management across cloud-based applications and services. It operates using JSON and REST, along with various authentication methods, to automate user provisioning, de-provisioning, and attribute management.
The SCIM protocol enables IT administrators to efficiently manage user accounts by transferring necessary identity information from an identity provider (IdP) to an application. This ensures that users can sign in and out seamlessly across the applications they require, without manual intervention.
Additionally, the SCIM API eliminates the need for proprietary integrations, making it easier for SaaS providers to support enterprise clients. By adopting SCIM, businesses can achieve a standardized, scalable, and secure approach to identity Governance & administration.
3. Why SCIM is Essential for Enterprise Security
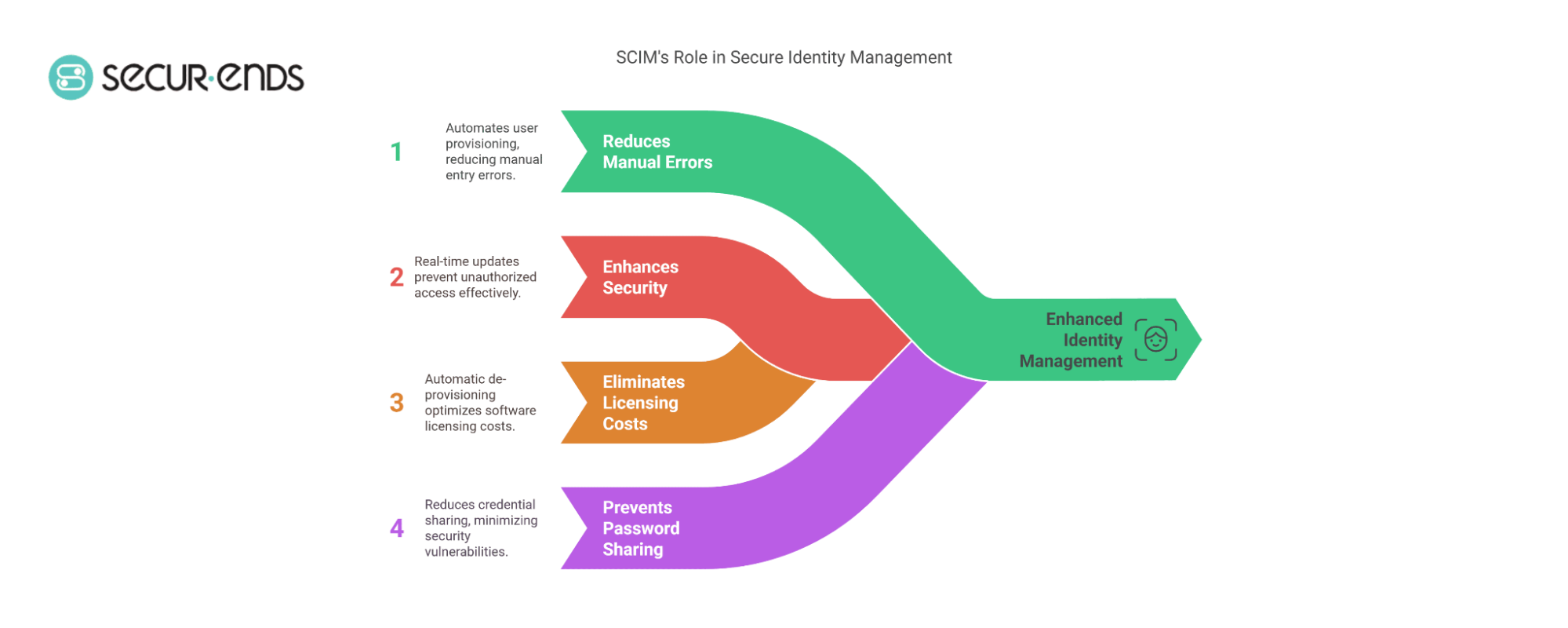
Managing user identities manually can be time-consuming and error-prone. Without automation, IT administrators must manually add, update, or remove user access, leading to inefficiencies and increased security risks. Here’s how SCIM provisioning enhances enterprise security:
- Reduces Manual Errors: By automating user provisioning and SCIM auto-provisioning, organizations eliminate mistakes caused by manual data entry, reducing the risk of unauthorized access.
- Enhances Security: SCIM ensures that user access permissions are updated in real-time. When an employee leaves the company, their accounts across all integrated applications can be instantly revoked, preventing unauthorized logins.
- Eliminates Licensing Costs: Automatic de-provisioning ensures that former employees no longer consume software licenses, helping organizations optimize costs.
- Prevents Password Sharing: With SCIM, users are provisioned with the necessary access from the start, reducing the need for sharing credentials and minimizing security vulnerabilities.
For enterprises managing a dynamic workforce, SCIM provisioning provides a standardized approach to identity management, ensuring compliance, security, and operational efficiency. As businesses continue to adopt cloud-based applications, implementing SCIM becomes a critical step in safeguarding digital resources.
4. How SCIM Auto-Provisioning Works
SCIM auto-provisioning streamlines the user onboarding and offboarding process by automating account creation, updates, and removal across multiple platforms. Instead of manually assigning and revoking access, SCIM API enables seamless identity synchronization between an identity provider (IdP) and various service providers, ensuring secure and efficient user management.
Steps in SCIM Auto-Provisioning:
- User Onboarding: When a new user is added to an organization’s HRMS or directory, the SCIM API ensures that their identity details are automatically provisioned across required applications (e.g., Slack, Jira, GitHub). This eliminates the need for IT administrators to manually create accounts on multiple platforms.
- Profile Synchronization: Any updates to a user’s attributes (e.g., department, role, email) are instantly synced across platforms. This ensures consistency, prevents outdated records, and reduces errors caused by manual updates.
- Role-Based Access Control (RBAC): SCIM auto-provisioning ensures that users are assigned appropriate permissions based on their role within the organization. For example, a newly promoted manager will automatically receive access to management-related applications without requiring manual intervention.
- User Offboarding: When a user leaves the organization, SCIM auto-provisioning revokes their access and removes their profiles from all connected services. This eliminates security risks, reduces licensing costs, and prevents unauthorized access to sensitive data.
By implementing SCIM auto-provisioning, businesses can improve security, reduce IT workload, and enhance operational efficiency by ensuring that user access remains up-to-date and aligned with company policies.
5. Understanding the SCIM Protocol and Architecture
At its core, the SCIM protocol defines how user identity information is shared between different systems, ensuring secure provisioning and synchronization of user data. It eliminates the need for proprietary APIs by offering a standardized method for managing user accounts, making identity management scalable and efficient.
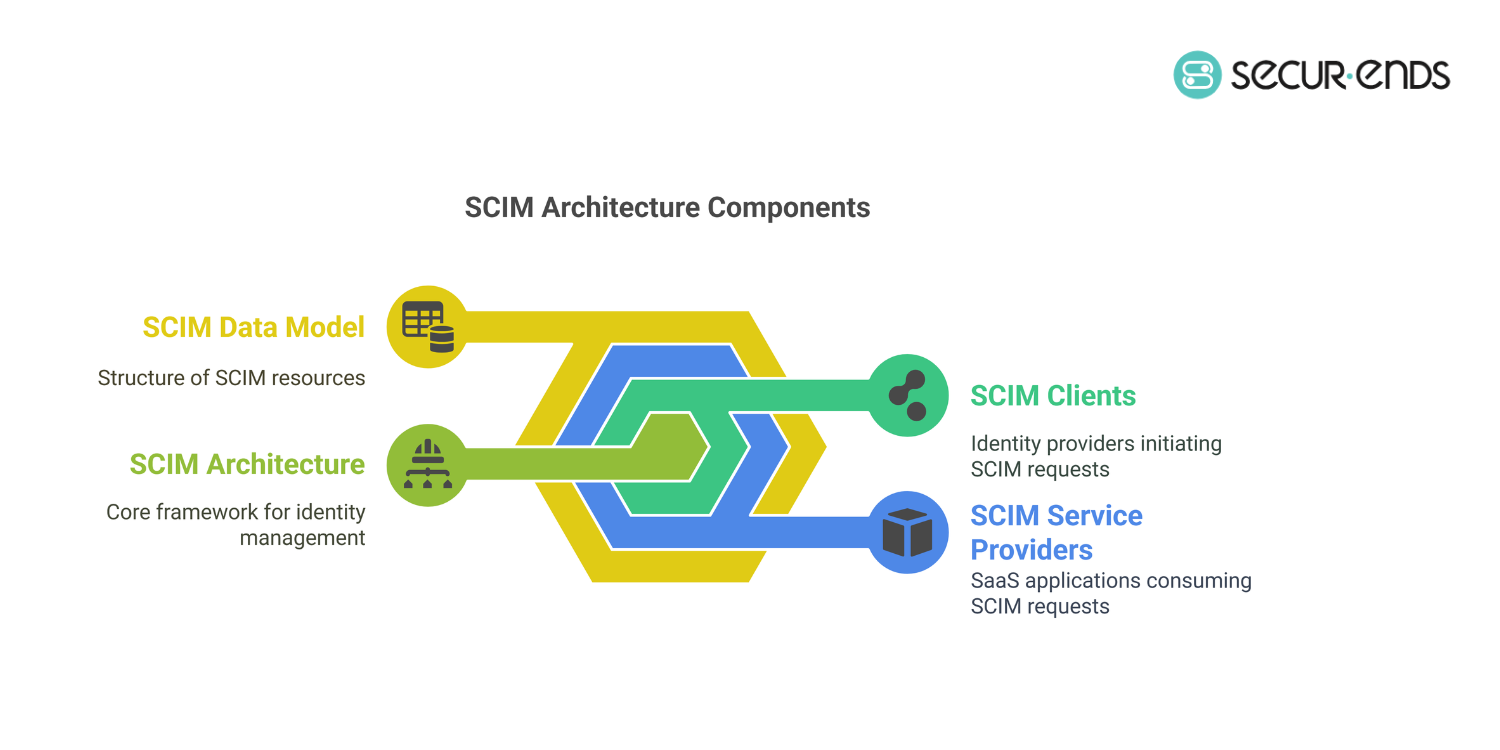
Core Components of SCIM Architecture:
- SCIM Clients (Identity Providers – IdPs): Platforms like Okta, Entra ID, and Google Workspace act as SCIM clients, managing user identities centrally and synchronizing them with service providers. They initiate requests to create, update, or remove users in downstream applications.
- SCIM Service Providers (SPs): SaaS applications such as Notion, GitHub, and Linear act as service providers, consuming SCIM requests to manage user accounts and permissions. These service providers ensure users have the correct level of access as defined by the identity provider.
- SCIM Data Model: SCIM resources are structured into two main types:
- User Resource: Represents an individual account with attributes such as username, email, role, and department. This ensures seamless identity mapping across platforms.
- Group Resource: Represents a collection of users with shared access privileges, simplifying permission management. Groups can be dynamically updated to add or remove users based on predefined conditions.
By leveraging SCIM identity management, enterprises can ensure real-time synchronization of user attributes across platforms, improving security, reducing IT administrative overhead, and maintaining compliance with regulatory standards.
6. SCIM API: CRUD Operations for Identity Synchronization
The SCIM API enables identity synchronization by performing CRUD (Create, Read, Update, Delete) operations across identity access management and applications. These operations ensure data consistency, enable real-time access management, and enhance security controls.
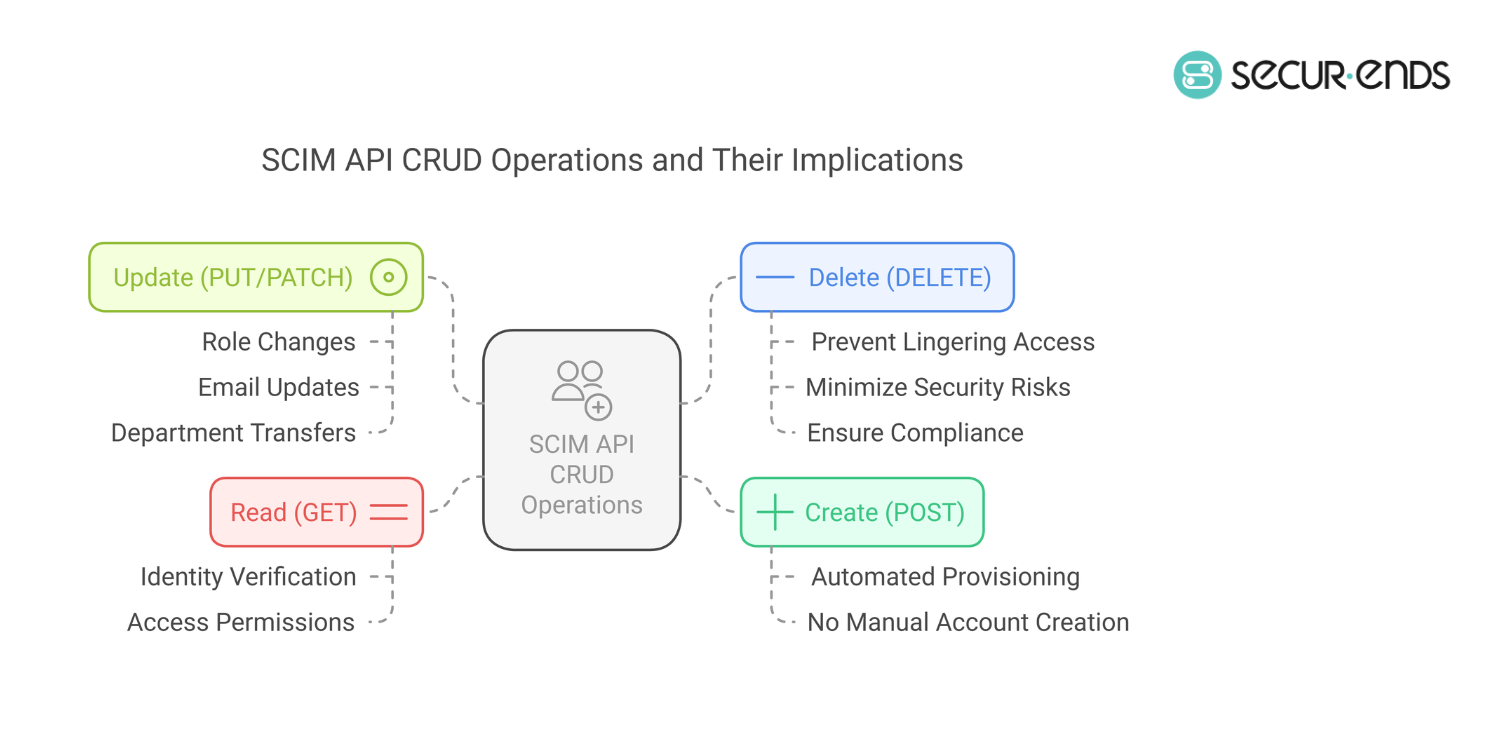
CRUD Operations in SCIM API:
- Create (POST): Automatically provisions a new user in the target application when added to the identity provider. This eliminates the need for IT teams to manually create accounts across multiple platforms.
- Read (GET): Fetches user or group details to verify identity and access permissions. This is useful for auditing, compliance, and real-time user verification.
- Update (PUT/PATCH): Modifies user attributes such as role changes, email updates, or department transfers. SCIM ensures that updates in the identity provider are reflected across all connected applications without delays or inconsistencies.
- Delete (DELETE): Deactivates or removes a user account when they leave the organization. This prevents lingering access, minimizes security risks, and ensures compliance with data retention policies.
By leveraging SCIM provisioning via API requests, organizations eliminate manual user management tasks, ensuring seamless identity synchronization while maintaining security and compliance. The automation of user provisioning and de-provisioning significantly reduces operational complexity, enhances efficiency, and ensures that only authorized users have access to critical business applications.
7. SCIM vs. SAML: Understanding the Differences
Security Assertion Markup Language (SAML) is an authentication protocol that enables users to securely access multiple applications using a single login. While SAML is essential for user authentication, it does not handle provisioning or managing user attributes across different systems. This is where SCIM provisioning comes in.
SCIM vs SAML:
- SCIM is used for identity provisioning—creating, updating, and deleting user accounts across multiple systems.
- SAML handles authentication by allowing users to sign in once and gain access to multiple services.
- SCIM ensures data consistency by synchronizing user attributes across platforms, while SAML grants access to those platforms based on authentication assertions.
By combining SCIM provisioning with SAML authentication, organizations can streamline identity management while maintaining security and efficiency. SCIM ensures that user attributes remain up to date across multiple applications, while SAML simplifies access control through single sign-on. This integration reduces the administrative burden on IT teams and enhances security by automating identity updates and permissions.
8. SCIM and SSO: How They Work Together
Single sign-on (SSO) is an authentication method that allows users to log in once and gain access to multiple applications without re-entering credentials. However, SSO alone does not manage user provisioning—this is where SCIM auto-provisioning enhances SSO-based identity management.
How SCIM and SSO Complement Each Other:
- SCIM auto-provisioning ensures that new users are automatically created and updated in all necessary applications.
- SSO handles authentication, verifying user identities once and granting access to multiple services.
- When a user is removed from the identity provider, SCIM de-provisions their accounts, ensuring they can no longer access connected applications.
By integrating SCIM and SSO, businesses achieve seamless identity management, improved security, and reduced IT workload. SCIM ensures that users’ access remains aligned with their roles, while SSO enhances user convenience by reducing the need for multiple passwords. Together, they form a robust identity management framework that enhances security and operational efficiency.
9. SCIM Flow: How Identity Providers and Service Providers Interact
In a typical SCIM architecture, there are two main participants:
- SCIM Identity Providers (IdPs): Platforms such as Okta, Google Workspace, and Microsoft Entra ID, which store and manage user identities.
- SCIM Service Providers (SPs): Applications like Notion, Slack, and GitHub, which rely on SCIM data to create and manage user accounts.
How SCIM Connectors Facilitate Identity Sync:
- User Creation: When an admin creates a user in the IdP, SCIM automatically provisions an account in the necessary applications.
- Attribute Updates: Changes made to a user’s profile in the IdP are instantly synced with connected applications.
- Access Revocation: If a user is removed or deactivated in the IdP, SCIM de-provisions them from all connected applications.
SCIM connectors ensure that identity data is synchronized between different enterprise applications, reducing manual intervention and improving security. By maintaining a single source of truth for identity data, organizations can minimize access discrepancies and streamline user management across platforms.
10. The Benefits of SCIM for Enterprise SaaS Providers
For SaaS providers, implementing SCIM provisioning is crucial for scalability, security, and improved user experience.
Why SaaS Businesses Should Implement SCIM:
- Automated User Management: Eliminates manual account creation, reducing IT overhead.
- Security and Compliance: Ensures that only authorized users have access and maintains compliance with data protection regulations.
- Scalability: SCIM provisioning enables seamless onboarding and offboarding as businesses grow.
- Improved ROI: Reduces operational costs by eliminating manual identity management tasks.
By integrating SCIM API, SaaS providers enhance their platform’s appeal to enterprise customers by offering automated provisioning, seamless integration with identity providers, and improved security. This ultimately leads to better user experience, higher customer retention, and a competitive advantage in the market.
11. Implementing SCIM: In-House vs. Third-Party Solutions
When implementing SCIM provisioning, organizations face a choice: build an in-house solution or use a third-party SCIM connector. Each approach has its advantages and challenges.
Challenges of In-House SCIM Implementation
- Development Complexity: Building a SCIM-compliant API from scratch requires extensive engineering resources and expertise in identity management protocols.
- Maintenance and Compliance: Maintaining the SCIM integration means continuous updates, security patches, and compliance with evolving standards.
- Integration Hurdles: Ensuring compatibility with various identity providers (IdPs) and service providers requires ongoing testing and support.
Using a Third-Party SCIM Connector
A third-party SCIM connector (e.g., Stytch, OneLogin, or Okta) simplifies SCIM adoption by offering pre-built solutions with robust security and scalability.
- Faster Deployment: No need to develop SCIM from scratch—just configure the connector to sync with your IdP.
- Security & Compliance: Providers ensure encryption, authentication, and compliance with security regulations.
- Scalability: Easily manage identity synchronization across multiple SaaS applications without extensive coding.
Organizations looking for seamless SCIM implementation should consider using SCIM connectors to accelerate deployment and reduce maintenance efforts.
12. How SCIM Supports Role-Based Access Control (RBAC)
Role-Based Access Control (RBAC) is an essential security framework that assigns user permissions based on roles. SCIM provisioning plays a key role in automating RBAC across enterprise applications.
SCIM’s Role in RBAC
- Automated Role Assignments: When a new employee joins, SCIM API ensures their account is provisioned with predefined role-based permissions.
- Real-Time Updates: If an employee is promoted, SCIM automatically updates their access rights across all integrated systems.
- Access Revocation: When a user leaves or changes departments, SCIM de-provisions their account, preventing unauthorized access.
Ensuring Compliance with SCIM API Updates
- Consistent Policy Enforcement: SCIM maintains compliance by ensuring access policies are uniformly applied across applications.
- Audit Trails & Security Logs: Organizations can track changes in user roles and permissions for security audits.
- Integration with IAM Systems: SCIM seamlessly syncs with Identity and Access Management (IAM) solutions to ensure enforcement of RBAC policies.
By integrating SCIM provisioning with RBAC, enterprises can automate access control, improve security, and enhance compliance.
13. Best Practices for SCIM Implementation in Enterprises
Implementing SCIM effectively requires careful planning and adherence to best practices to ensure security, scalability, and compliance.
1. Choosing the Right SCIM Connector
- Select a SCIM connector that supports your identity provider (IdP) (e.g., Okta, Entra ID, Google Workspace).
- Ensure compatibility with enterprise applications requiring identity synchronization.
2. Ensuring Secure and Compliant SCIM Provisioning
- Use OAuth or API keys for secure authentication between IdPs and service providers.
- Implement encryption and access controls to protect user identity data.
- Monitor and audit SCIM logs to detect anomalies in user provisioning.
3. Standardizing SCIM API Integration
- Follow SCIM 2.0 specifications to ensure interoperability with multiple applications.
- Utilize RESTful SCIM APIs to simplify CRUD operations (Create, Read, Update, Delete).
By adhering to these best practices, enterprises can optimize SCIM provisioning and strengthen identity management frameworks.
14. Real-World SCIM Use Cases and Industry Applications
SCIM is widely used across industries to simplify identity management, enhance security, and reduce administrative overhead.
1. Enterprise SaaS Platforms
- Companies like Slack, GitHub, and Atlassian use SCIM API to automate user provisioning and de-provisioning across their cloud-based services.
- SCIM ensures that employees have the right permissions while reducing manual admin tasks.
2. Higher Education & Universities
- Universities use SCIM auto-provisioning to grant students and faculty access to learning management systems (LMS), email, and collaboration tools.
- When students graduate, SCIM revokes their access automatically.
3. Healthcare & Compliance-Driven Industries
- SCIM helps hospitals manage HIPAA compliant identity provisioning, ensuring only authorized personnel access sensitive patient data.
- Automates user lifecycle management for doctors, nurses, and administrative staff.
4. Financial Services & Banking
- Banks leverage SCIM API to integrate with IAM solutions, enforcing strict access policies for financial data security.
- Automates user provisioning for employees and external partners requiring temporary access.
By leveraging SCIM auto-provisioning, organizations across industries can enhance efficiency, security, and compliance.
Read Also: Introduction to Identity and Access Management (IAM) Certification
15. Importance of SCIM Provisioning
Managing identities manually is complex, error-prone, and inefficient. SCIM user provisioning addresses these challenges by automating identity lifecycle management.
Challenges of Manual Identity Management
- Human Errors: IT teams may assign incorrect permissions or forget to revoke access.
- Security Risks: Former employees or unauthorized users may retain access to sensitive systems.
- Administrative Overhead: Manually creating and updating accounts across multiple applications is time-consuming.
How SCIM User Provisioning Streamlines Identity Management
- Automated Account Creation & Updates: New employees receive immediate access, and their details remain synchronized across applications.
- Seamless Role-Based Access: SCIM assigns permissions based on predefined roles, ensuring secure access control.
- Instant De-Provisioning: When employees leave, SCIM revokes access to all connected systems, enhancing security.
By adopting SCIM user provisioning, organizations can automate provisioning, improve security, and enhance compliance.
16. Conclusion: Why SCIM is the Future of Identity Management
As organizations scale and adopt multiple SaaS applications, managing user identities efficiently becomes a necessity. SCIM provisioning provides a standardized, automated, and secure approach to identity lifecycle management, reducing IT overhead while enhancing security. By leveraging the SCIM protocol, businesses can seamlessly synchronize user attributes across platforms, ensuring real-time updates and role-based access control. Additionally, SCIM API integrations enable enterprises to automate provisioning and de-provisioning, eliminating manual errors and security risks. With its ability to streamline identity management, improve compliance, and integrate seamlessly with IAM and SSO solutions, SCIM is the future of efficient and scalable identity management for modern enterprises.