User Access Review Policy – A Complete Guide
User Access Review Policy – A Complete Guide

Introduction
Managing user access effectively is a fundamental aspect of enterprise security and regulatory compliance. As organizations expand, so do the complexities of managing permissions across multiple systems, applications, and cloud environments. Without a structured user access review policy, businesses risk unauthorized access, security breaches, and non-compliance with industry regulations.
A well-defined user access policy ensures that employees, contractors, and third-party users have appropriate access based on their roles and responsibilities. Regular user access reviews help organizations maintain strict oversight by identifying and revoking unnecessary permissions, minimizing risks associated with privilege creep and insider threats.
To streamline this process, many enterprises leverage user access review software as part of their Identity Governance and Administration (IGA) and Identity Access Management (IAM) strategies. These solutions automate access management reviews, reducing administrative overhead while enhancing security, efficiency, and compliance adherence.
By implementing a structured user access review policy, businesses can strengthen their security posture, ensure operational integrity, and meet regulatory requirements with confidence.
2. Benefits of User Access Review Policy
Implementing a robust user access review policy delivers significant advantages in security, compliance, and operational efficiency. As organizations scale, managing user permissions becomes increasingly complex. A structured approach to user entitlement review ensures that access is appropriately granted, monitored, and revoked when necessary, reducing security risks and enhancing compliance.
Ensuring Regulatory Compliance
For organizations subject to regulatory frameworks such as SOX user access review requirements, access management is a critical compliance factor. Regular audits help verify that only authorized individuals have access to financial systems and sensitive data, minimizing the risk of fraud and unauthorized modifications. Automating these reviews simplifies compliance reporting and reduces the risk of penalties for non-compliance.
Strengthening IAM Risk Management
Unmonitored access can lead to privilege creep, where users accumulate unnecessary permissions over time, increasing security vulnerabilities. An effective IAM risk management strategy mitigates these risks by enforcing strict access controls and ensuring that permissions align with job responsibilities. This reduces the likelihood of privilege misuse or abuse, protecting both internal and customer data.
Enhancing Security with IGA
A well-structured IGA security framework enables organizations to maintain a proactive stance on security. By integrating customer identity and access management (CIAM) solutions, businesses can ensure that external users, including customers and partners, have appropriate access while maintaining strict control over sensitive systems. This not only improves security but also enhances user experience and trust.
Optimizing IT Workflows and Reducing Workload
Manual access management can be resource-intensive and error-prone. Automating user entitlement review processes through IGA security solutions alleviates the workload on IT teams, allowing them to focus on strategic initiatives rather than repetitive administrative tasks. With improved visibility into access privileges, organizations can respond swiftly to security incidents and streamline audit processes.
By incorporating a comprehensive user access review policy, businesses can achieve a balanced approach to security, risk management, and regulatory compliance while fostering a more efficient and secure operational environment.
3. How Does a User Access Review Policy Work?
A user access review policy follows a systematic approach to ensure users have the appropriate access levels while preventing unauthorized privileges. By implementing a structured user access review process, organizations can minimize security risks, maintain compliance, and streamline access management.
Step 1: Initiating the Access Review Process
The first step is identifying and reviewing all users with access to critical systems, applications, and databases. This involves compiling a list of permissions assigned to employees, third-party vendors, and system accounts. Using user access review software, organizations can automate this process, reducing manual effort and enhancing accuracy.
Step 2: Setting Review Frequency
Determining how often access reviews should be conducted is crucial for maintaining security and compliance. The frequency depends on industry regulations, organizational size, and risk factors. Many businesses conduct quarterly or annual reviews to ensure that permissions remain aligned with job roles and security policies.
Step 3: Reviewing and Validating User Entitlements
Once the review is initiated, IT teams or managers assess user access rights to confirm whether they are necessary for current job functions. A user access review checklist helps verify if users have excessive or outdated permissions. Any unnecessary access is revoked immediately to minimize security threats.
Step 4: Ensuring Compliance Through Documentation
Thorough documentation of each review cycle is essential for demonstrating regulatory compliance. Organizations must record the review date, users assessed, changes made, and any identified risks. This documentation helps meet requirements such as SOX user access review standards and other security frameworks.
Step 5: Automating the Access Review Process
To enhance efficiency, organizations implement user access review software, which automates risk analysis, generates audit reports, and provides real-time access insights. Automation not only accelerates the access review process but also reduces human errors and improves policy enforcement.
Step 6: Leveraging Federated Identity & Access Management
For enterprises managing multiple authentication systems, Federated Identity & Access Management simplifies access control by enabling seamless authentication across platforms. This approach reduces administrative overhead while ensuring users access only the systems they are authorized to use.
By following a structured user access review policy, businesses can strengthen security, improve regulatory compliance, and optimize identity and access management practices.
4. Key Components of an Effective User Access Review Policy
A well-structured user access review policy ensures that organizations maintain security, compliance, and operational efficiency by systematically reviewing and managing user permissions. Below are the essential components that make an access review policy effective.
4.1 Policy Objectives and Scope
The primary goal of a user access review policy is to ensure that users only have the necessary access to systems and data required for their roles. This minimizes security risks and helps organizations comply with regulatory standards.
The scope of the policy should define:
- Which systems and applications are subject to access management reviews
- The user groups included (employees, third-party vendors, temporary users)
- The integration of identity governance and administration solutions to automate and enforce policy adherence
Clearly defining the scope prevents privilege creep and ensures access permissions remain aligned with business needs.
4.2 Roles and Responsibilities
Effective access reviews require well-defined roles and responsibilities. The user entitlement review process involves multiple stakeholders, each playing a critical role in ensuring policy enforcement:
- System Administrators: Oversee access rights and maintain system security
- Managers and Department Heads: Review and validate team members’ access based on job functions
- Compliance Officers: Ensure that access reviews align with regulatory frameworks
- IT Security Teams: Identify risks and implement remediation measures
Holding Identity Access Management Certifications ensures that personnel conducting these reviews are well-versed in security protocols and compliance requirements.
4.3 Review Frequency and Triggers
Setting a proper review schedule is crucial for maintaining security and compliance. SOX user access review regulations require periodic evaluations of financial system access, ensuring only authorized individuals have permissions.
Best practices for scheduling access reviews include:
- Periodic Reviews: Conducting quarterly or annual evaluations using a user access review checklist
- Event-Triggered Reviews: Initiating reviews when employees change roles, leave the organization, or when security incidents occur
- Real-Time Monitoring: Using automated tools to detect and flag unusual access patterns
4.4 User Access Classification
(user access policy, customer identity and access management, Role-Based Access Control (RBAC))
A structured user access policy categorizes users based on their roles, reducing security risks and ensuring proper permission allocation. Role-Based Access Control (RBAC) is widely used to classify access:
- Standard Users: Employees with limited access based on job requirements
- Privileged Users: Administrators and executives with higher access levels
- Third-Party Users: Vendors and contractors with restricted, temporary access
Incorporating customer identity and access management (CIAM) ensures that external users, such as customers, have access to necessary systems while maintaining security controls.
4.5 Review Process
(user access reviews, access review process, user access review software, Scim API)
The access review process involves systematically evaluating and updating user permissions. The key steps include:
- Data Collection: Gathering user access reviews across all systems
- Analysis and Validation: Reviewing permissions to determine if they align with job functions
- Approval or Revocation: Managers confirm access rights, and unnecessary privileges are removed
- Audit Reporting: Generating compliance reports for future reference
User access review software streamlines this process by automating data retrieval, policy enforcement, and reporting. Additionally, SCIM API (System for Cross-domain Identity Management) facilitates the seamless integration of user identity management across platforms, enabling automated updates and reducing administrative overhead.
4.6 Escalation and Remediation
(access management reviews, user entitlement review, IAM Risk Management)
If policy violations or security threats are detected during access management reviews, organizations must have a clear remediation strategy. Key steps in handling issues include:
- Risk Assessment: Determining the severity of unauthorized access
- Immediate Revocation: Removing excessive permissions to prevent exploitation
- Incident Escalation: Notifying IT security teams and compliance officers for further investigation
- Policy Updates: Adjusting IAM Risk Management strategies to prevent future violations
By incorporating user entitlement review procedures, businesses can proactively mitigate risks and enhance access governance.
4.7 Documentation and Reporting
Maintaining accurate records is essential for compliance and auditing purposes. A standardized user access review template ensures that organizations document:
- Users and their assigned access levels
- Approval or denial of access requests
- Policy violations and remediation actions
Using identity governance and administration solutions, organizations can automate documentation processes, ensuring that audits are seamless and compliant with regulatory requirements.
4.8 Policy Review
A user access review policy should not remain static. Organizations must continuously evaluate and refine their policies to address evolving security challenges. Regular policy updates ensure compliance with IGA security best practices and industry regulations.
By leveraging identity governance and administration solutions, businesses can:
- Identify gaps in existing policies
- Implement adaptive security measures
- Ensure compliance with changing regulatory landscapes
A well-maintained user access review policy strengthens an organization’s security framework, reduces compliance risks, and enhances operational efficiency.
5. How Does SecurEnds Help You Implement UAR Policies?
Managing user access effectively is crucial for maintaining security, preventing unauthorized data exposure, and ensuring regulatory compliance. However, traditional automated user access reviews are often time-consuming, manual, and prone to errors. SecurEnds simplifies this process with its advanced user access review software, offering automation, compliance tracking, and seamless integration with existing security frameworks.
Automated User Access Reviews for Compliance
SecurEnds provides a centralized, automated platform to help organizations enforce a structured user access review policy while ensuring compliance with regulatory standards such as SOX, HIPAA, ISO27001, SOC1/2, and PCI. Instead of relying on error-prone manual reviews, SecurEnds automates the entire access review process, making it faster, more accurate, and more efficient.
Key Compliance Features:
- Recurring Campaigns: Organizations can schedule periodic access management reviews to continuously assess whether employees have the appropriate level of access.
- Automated User Entitlement Checks: The system automatically flags excessive permissions, unauthorized access, or orphaned accounts.
- Audit-Ready Reports: SecurEnds generates detailed access attestation reports, ensuring that compliance documentation is always up to date for internal audits and external regulatory reviews.
By automating these critical aspects of identity governance and administration solutions, SecurEnds reduces the risk of security breaches while helping businesses maintain regulatory compliance with minimal manual intervention.
Seamless Integration with Identity Governance and Administration Solutions
SecurEnds is built to work seamlessly with existing identity governance and administration solutions, making integration smooth and efficient. The platform provides multiple ways to import, review, and analyze user access data, ensuring that organizations have full visibility into their security posture.
Integration Features:
- CSV File Uploads: Allows security teams to securely import entitlement data from different applications for access reviews.
- Built-in Connectors: Easily integrates with both cloud-based and on-premise applications, reducing setup time.
- Access Attestation Dashboard: Provides a centralized interface for IT teams to monitor access certifications and track compliance.
By consolidating access data from multiple systems, SecurEnds helps organizations enforce a robust user access policy without disrupting existing workflows.
Enhanced Role-Based Access Control (RBAC) and Federated IAM
Effective access management isn’t just about reviewing permissions—it’s about assigning the right access levels based on user roles. SecurEnds leverages Role-Based Access Control (RBAC) to ensure that employees have the exact level of access they need—nothing more, nothing less.
RBAC Benefits:
- Minimizes Privilege Creep: Prevents users from accumulating unnecessary access over time.
- Automates Access Adjustments: When employees change roles, the system automatically revokes or modifies access based on predefined policies.
- Improves Security and Productivity: Employees get the access they need without compromising security.
SecurEnds also supports Federated Identity & Access Management, allowing users to authenticate across multiple systems with a single identity. This simplifies user authentication, enhances security, and improves user experience by eliminating the need for multiple login credentials.
SCIM API for Process Automation
SecurEnds further enhances access management through SCIM API integration. SCIM (System for Cross-domain Identity Management) enables organizations to automate the provisioning and deprovisioning of user accounts across various platforms, ensuring that access permissions remain current and secure.
SCIM API Benefits:
- Real-Time Synchronization: Automatically updates user entitlements across all connected systems.
- Eliminates Manual Work: Reduces administrative overhead by automating repetitive access management tasks.
- Prevents Security Gaps: Ensures that access is instantly revoked when employees leave or change roles.
By leveraging SCIM API, organizations can streamline their access review process, eliminating outdated permissions and reducing security risks.
How SecurEnds Compares to Competitors Like Zluri
While competitors like Zluri offer access management features, SecurEnds differentiates itself through its focus on automation, compliance, and seamless integration with IAM frameworks.
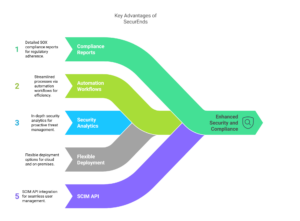
Key Advantages of SecurEnds:
- Comprehensive Compliance Management: Advanced audit-ready reporting and compliance tracking for SOX and other frameworks.
- Flexible Deployment Options: Available as a cloud-based SaaS or an on-premises solution, catering to businesses with different security requirements.
- Advanced Automation Features: SCIM API, user access review software, and federated IAM ensure a streamlined and efficient access review process.
- Enhanced Security Visibility: Organizations can quickly identify potential access risks and take proactive measures to mitigate them.
By integrating SecurEnds into their security framework, organizations can enhance compliance, streamline user access policy enforcement, and maintain complete visibility into user entitlements—all while reducing administrative burdens and security risks.
6. Conclusion
A strong user access reviews policy is essential for maintaining security, ensuring compliance, and preventing unauthorized access. Regular access management reviews help organizations stay ahead of threats, reduce risks, and meet industry regulations like SOX, HIPAA, and ISO27001.
However, manual user access reviews can be time-consuming and prone to errors. SecurEnds’ user access review software simplifies the process with automation, making it easier to manage access rights, track compliance, and generate audit reports. With features like Role-Based Access Control (RBAC), SCIM API, and Federated Identity & Access Management, SecurEnds helps organizations streamline user access management efficiently and accurately.
By choosing SecurEnds’ identity governance and administration solutions, businesses can enhance security, improve compliance, and reduce the complexity of managing user access across their IT environment.