Understanding Role-Based Access Control (RBAC): A Comprehensive Guide
Understanding Role-Based Access Control (RBAC): A Comprehensive Guide

Introduction
In today’s digital landscape, organizations must manage user access securely and efficiently. Role-Based Access Control (RBAC) is a widely adopted security model that restricts system access based on predefined roles rather than assigning permissions individually. This approach reduces security risks, simplifies administration, and ensures compliance with regulations like GDPR and HIPAA.
Many businesses ask, “What is RBAC?” Simply put, RBAC is a system that controls access based on job responsibilities. The RBAC definition revolves around the idea of granting users only the permissions they need to perform their tasks. For example, in an e-commerce company, customer service representatives may have access to order details, while warehouse staff can only update inventory records. This ensures that employees can do their jobs efficiently without accessing sensitive data unnecessarily.
By implementing role-based access control, organizations improve access control in cybersecurity, mitigate insider threats, and efficiently manage user permissions. As businesses expand and integrate third-party access, RBAC becomes an essential strategy for safeguarding sensitive information.
2. The Importance of Access Control in Cybersecurity
Effective access control is essential for securing sensitive data and preventing unauthorized access. In today’s digital landscape, organizations face increasing cyber threats, making cybersecurity access control a crucial defense mechanism. Unauthorized access can lead to data breaches, financial losses, and regulatory non-compliance, putting both businesses and their customers at risk.
The importance of RBAC lies in its ability to enforce structured access rules, ensuring that users can only access the resources necessary for their roles. By implementing access management strategies like RBAC, businesses can strengthen security, reduce insider threats, and maintain compliance with regulations such as GDPR, HIPAA, and SOC 2.
Read more about how to conduct a security risk assessment to strengthen cybersecurity and ensure regulatory compliance.
3. History and Evolution of RBAC
The history of RBAC dates back to the 1970s when organizations began exploring structured methods to control system access. Over time, RBAC evolved from simple role-based permissions to more advanced access control models designed to handle large-scale enterprise systems.
By the 1990s, RBAC gained widespread recognition when the National Institute of Standards and Technology (NIST) formalized its framework. Since then, RBAC adoption has expanded across industries like healthcare, finance, and cloud computing, helping organizations enhance security and streamline access control.

4. How Role-Based Access Control Works
Understanding how RBAC works involves analyzing how permissions are assigned and enforced. At its core, RBAC access control functions by defining roles, associating them with specific permissions, and assigning those roles to users.
For example, in an IT department, a system administrator might have full access to modify settings, while a help desk technician can only reset passwords. This role-based access management approach ensures users have permission levels that align with their responsibilities, reducing security risks and administrative overhead.
5. Key Components of RBAC
Role-Based Access Control (RBAC) is a structured access control model that assigns permissions based on predefined roles rather than individual users. By implementing RBAC components, organizations can ensure secure and efficient access management. Below are the essential elements that make up an RBAC system:
1. Operations
Operations refer to the various activities performed within a computing environment, such as data input, processing, retrieval, modification, and deletion. Certain operations—like changing system configurations—are restricted to administrators or privileged users. Managing permissions in RBAC ensures that only authorized individuals can execute these actions, reducing security vulnerabilities.
2. Permissions
Permission management is a core aspect of RBAC systems, determining what actions a role can perform on specific resources. Instead of granting access directly to users, RBAC policies assign permissions to roles. For example, an HR manager might have permission to update employee records, while a general employee may only have viewing rights.
3. Resources (Objects)
Resources—also known as objects—are digital assets like files, databases, applications, and servers. RBAC components define which users can interact with these resources and in what capacity. A well-implemented RBAC policy also ensures that access logs are maintained, tracking who accessed a resource, what actions were taken, and when.
4. Roles
Roles in RBAC serve as collections of permissions that dictate what a user can do within a system. Rather than assigning permissions to individuals, RBAC systems allocate them based on roles linked to job functions or organizational hierarchy. A finance executive, for instance, may have access to financial reports, while an IT administrator manages system settings. Users can also hold multiple roles based on their responsibilities.
5. Sessions
A session represents the time a user actively interacts with a resource or system. Tracking sessions is essential for security audits, as it records login/logout times, actions performed, and access locations. This ensures compliance with RBAC policies and helps detect unauthorized activities.
6. Users
In an RBAC system, a user is any entity granted access through a specific role. While typically individuals, users can also include applications, automated processes, or devices that need controlled access. Assigning roles in RBAC instead of granting individual access simplifies security management.
7. RBAC Permission Structure
A well-defined RBAC policy ensures that permissions follow roles, not users. Key considerations in permissions management include:
- Access Control: Determining which users can view or open specific files, applications, or databases.
- Modification Rights: Defining which users can edit, update, or delete resources and what approval processes are required.
- Sharing Permissions: Establishing rules for downloading, sharing, or distributing documents securely.
By implementing structured RBAC components, organizations can enhance security, streamline permissions management, and maintain compliance with industry regulations.
6. Types of Access Control: RBAC vs. Other Models
While RBAC is a widely used framework, it is not the only access control models available. Organizations often compare RBAC vs DAC (Discretionary Access Control) and RBAC vs ABAC (Attribute-Based Access Control) to determine the best approach.
- DAC allows users to control access to their resources, making it more flexible but prone to security risks.
- ABAC grants access based on attributes like location, time, or device type, providing dynamic access control.
RBAC, in contrast, offers a structured, role-based approach that simplifies access management frameworks for businesses.
7. Role-Based Access Control in Databases (RBAC in DBMS)
RBAC in DBMS is a crucial security mechanism that ensures structured and restricted access to database resources. By assigning specific roles to users, database access control helps prevent unauthorized modifications while maintaining efficient operations.
For example, a database administrator (DBA) role typically has full access to manage and modify all data, whereas a general user role may only have read access to selected tables. Similarly, a sales role might have permission to access customer records, while a finance role is restricted to financial data.
By implementing role-based database security, organizations can simplify permission management and enhance data protection. Access control in SQL ensures that only users with the appropriate roles can interact with specific tables, minimizing the risk of unauthorized data exposure.
8. RBAC Roles and Permissions
The structure of RBAC roles defines the level of access granted to users. Common role-based permissions include:
- Administrator – Full control over system settings and user management.
- Manager – Ability to modify team data and approve requests.
- User – Limited access to perform specific tasks.
- Guest – Restricted access with read-only permissions.
By implementing clear user roles in RBAC, organizations can efficiently manage access privileges and maintain security.
9. Role-Based Access Control in Cloud Security (RBAC in Azure, AWS, and SaaS)
Cloud platforms like Microsoft Azure, AWS, and SaaS applications use RBAC in cloud security to control user permissions.
- Azure RBAC allows administrators to assign fine-grained access to resources.
- RBAC in AWS provides role-based permissions for cloud services.
- Role-based access control in SaaS applications ensures secure multi-user collaboration.
With cloud adoption on the rise, implementing cloud security access control through RBAC is critical for preventing data breaches and ensuring compliance.
10. Benefits of Implementing RBAC
Implementing Role-Based Access Control (RBAC) helps organizations create a structured and secure access management system. By defining permissions based on roles rather than individual users, companies can enhance security, simplify administration, and meet regulatory standards.
- Simplified Administration – One of the key benefits of RBAC is its ability to reduce administrative workload. Instead of managing access for each user separately, permissions are assigned based on predefined roles, making it easier to onboard new employees or modify existing access rights.
- Stronger Security Measures – Restricting access to only necessary resources helps prevent unauthorized activities. RBAC advantages include ensuring that users operate within their designated permissions, which aligns with security best practices and reduces data breaches.
- Regulatory Compliance – Many industries require strict access control to meet regulations like GDPR, HIPAA, and SOC 2. Compliance with RBAC ensures that organizations maintain a well-documented and auditable access control system.
- Scalability and Flexibility – As businesses grow, their access control needs change. RBAC advantages allow for seamless role modifications, ensuring that access permissions remain aligned with evolving job responsibilities.
- Reduced Risk Exposure – By enforcing security best practices, RBAC limits insider threats and minimizes accidental or intentional misuse of sensitive data.
- Optimized User Experience – Employees only see the tools and data relevant to their roles, reducing confusion and making workflows more efficient.
By leveraging the benefits of RBAC, organizations can create a structured, scalable, and compliant access control system that strengthens security while improving operational efficiency.
11. Challenges in Implementing RBAC
While implementing RBAC improves security and access management, organizations often encounter several hurdles that can complicate the process.
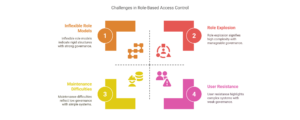
- Role Explosion Issue – One of the biggest RBAC challenges is creating too many roles, making access control as complex as managing individual users. A well-structured role model is essential to avoid unnecessary complexity.
- Inflexible Role Models – A poorly designed role structure can lead to inefficiencies. Organizations need a tailored approach rather than a one-size-fits-all model to prevent unnecessary restrictions.
- Maintenance Difficulties – Keeping roles and permissions updated as business needs evolve is an ongoing effort. If not managed properly, outdated role assignments can cause security gaps or operational slowdowns.
- User Resistance – Employees may struggle to adapt to new access control policies, especially if the changes seem restrictive or unclear. Clear communication and training can help ease the transition.
- Over-Reliance on Automated Role Generation – Some tools promise automatic role creation, but without manual oversight, the generated roles may not align with business needs, leading to inefficiencies.
- Lack of Identity Management Foundation – Without a solid identity governance framework, even the best RBAC setup can fail. Proper policies must be in place to control how administrators manage user access.
Understanding these RBAC challenges allows organizations to anticipate potential roadblocks and create a structured, scalable, and effective access control system.
Read Also: Identity Governance: Best Ways to Make Your Processes Easier & More Efficient
12. Best Practices for Implementing RBAC Effectively
To maximize security and efficiency, organizations should follow RBAC best practices:
- Use role hierarchies – Structure roles to avoid redundancy.
- Follow the least privilege principle – Assign only necessary permissions.
- Regularly review policies – Keep access control policies updated.
By implementing these role-based security strategies, businesses can enhance security and operational efficiency.
13. RBAC and Compliance: Meeting Regulatory Requirements
Many regulations require strict RBAC compliance for data protection. Organizations must ensure:
- GDPR and RBAC – User access aligns with data privacy laws.
- HIPAA access control – Protects healthcare records from unauthorized access.
- SOC 2 – Demonstrates security controls for cloud-based services.
By aligning RBAC with regulatory requirements, businesses can avoid penalties and maintain industry compliance.
14. Future Trends in Role-Based Access Control
The future of RBAC is evolving with advancements in next-gen access control technologies:
- AI in RBAC – Automates role assignment and security monitoring.
- Adaptive access control – Dynamically adjusts permissions based on user behavior.
- Zero-trust security – Ensures continuous authentication and access verification.
As cyber threats increase, businesses must adopt modern RBAC solutions to stay secure.
15. Conclusion: Is RBAC Right for Your Organization?
When it comes to choosing RBAC, organizations must carefully assess their unique security and operational needs to determine the most effective access control implementation. Factors such as security requirements, scalability, and compliance needs play a crucial role in deciding whether role-based security solutions are sufficient or if a hybrid approach is necessary. Businesses must consider whether RBAC can adapt to future growth while ensuring it aligns with their overall cybersecurity strategy. For most companies, RBAC offers a well-structured, secure, and efficient method of managing access, making it a valuable long-term investment in protecting sensitive data and maintaining compliance.