Ultimate Guide to User Access Reviews: Process, Best Practices & Automation
Ultimate Guide to User Access Reviews: Process, Best Practices & Automation

In 2025, businesses handle massive amounts of sensitive data across multiple systems and applications. User Access Reviews (UARs) play a critical role in ensuring that only the right people have access to specific resources, reducing security risks and ensuring compliance with regulations.
Why Are User Access Reviews Important?
Unauthorized access is a leading cause of security breaches. According to Statista, 82% of security breaches involve human-related factors, including weak access controls and excessive user privileges.
Without regular user access reviews, organizations risk privilege creep, where users accumulate unnecessary permissions over time, increasing the potential for insider threats or data leaks.
A 2024 Gartner Board of Directors Survey highlights that 93% of boards recognize cyber-risk as a threat to stakeholder value, yet 67% admit their oversight structures are inadequate for managing evolving security risks.
Additionally, a 2024 Trends in Securing Digital Identities Report by the Identity Defined Security Alliance (IDSA) found that 90% of organizations experienced at least one identity-related incident in the past year, with 84% of those incidents leading to direct business impact.
Failing to implement effective identity and access management (IAM) practices and user access controls (UAC) significantly increases compliance risks, financial losses, and security breaches for businesses.
Also Read: User Access Review Process: What Is It?
The Business Impact of Not Conducting UARs
- Regulatory Fines: SOX User Access Review, HIPAA, and GDPR require businesses to perform regular access reviews. Failure to comply can result in fines ranging from $50,000 to millions of dollars, depending on the severity of the breach.
- Security Risks: Unreviewed access can lead to data breaches, unauthorized transactions, and fraudulent activities.
- Operational Inefficiencies: Organizations without automated user access review tools spend 40% more time conducting manual access audits, according to Okta’s Identity Governance Report.
What This Guide Covers
This guide provides a comprehensive breakdown of user access review best practices, step-by-step user access review procedures, the importance of automation, and how SecureEnds’ user access review software simplifies compliance.
Read: Best Ways to Conduct User Access Reviews: Strategies for Efficiency and Accuracy
2. What is a User Access Review?
A User Access Review (UAR) is a critical security and compliance process where organizations evaluate and validate employee, contractor, and third-party access to systems, applications, and data.
The goal is to ensure that only authorized individuals have the appropriate access levels needed for their roles, reducing security risks and compliance violations.
User Access Review vs. User Access Controls (UAC)
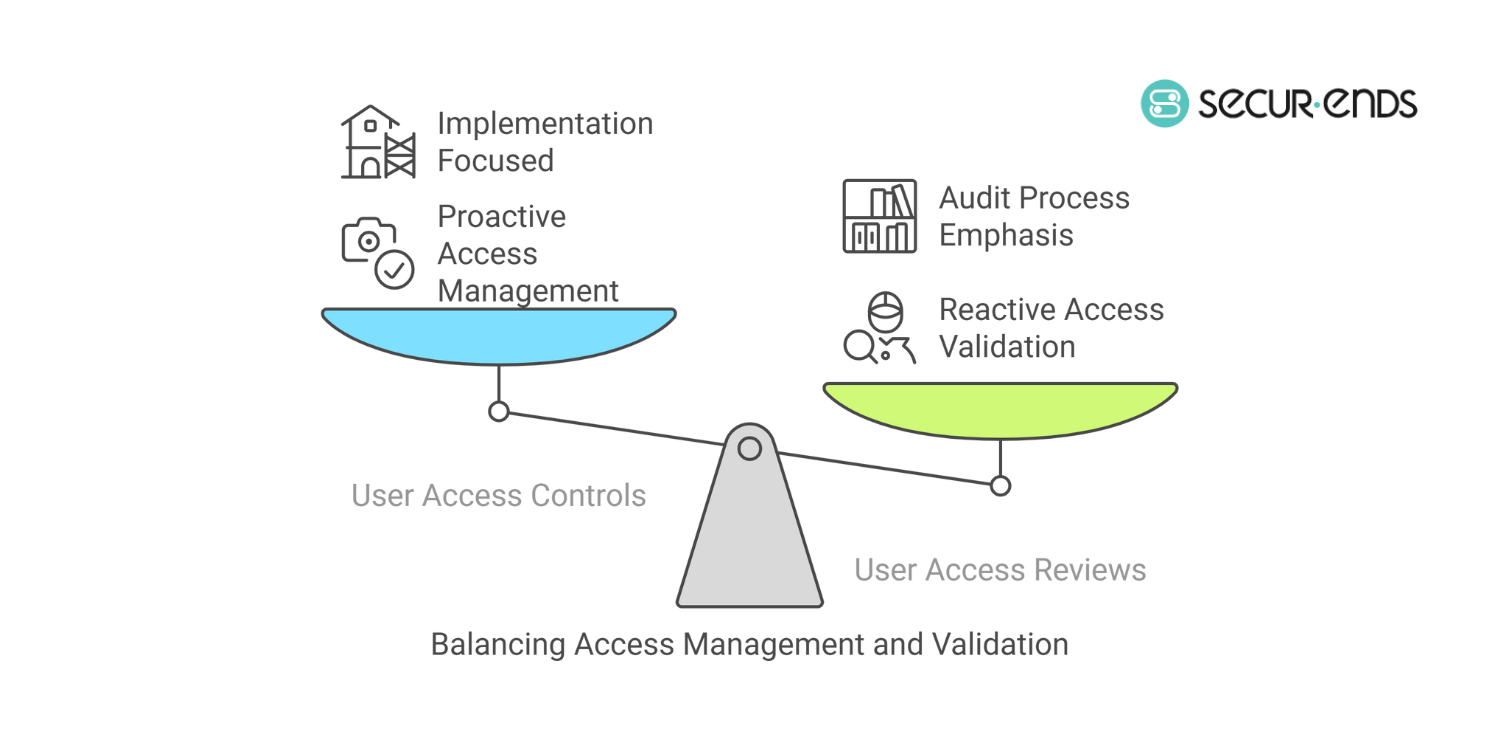
While both concepts relate to identity governance, they serve different purposes:
- User Access Controls (UAC): Defines and enforces who can access what within an organization’s IT environment. It includes policies like role-based access control (RBAC) and least privilege access.
- User Access Reviews (UAR): A periodic audit process to review and validate existing access permissions, ensuring they align with business needs and compliance requirements.
According to Gartner, over 70% of organizations fail to conduct effective access reviews, leading to orphaned accounts, excessive permissions, and increased cybersecurity risks. Without regular reviews, companies face the risk of privilege creep, where employees accumulate unnecessary access rights over time, increasing the likelihood of insider threats.
Why UARs Are Critical in User Access Management
- Prevent Unauthorized Access: A 2023 IBM Data Breach Report states that the average cost of a data breach caused by compromised credentials is $4.35 million. UARs help mitigate these risks.
- Ensure Compliance: Regulations such as SOX User Access Review, HIPAA, GDPR, and ISO 27001 mandate organizations to perform access reviews to ensure data security and accountability.
- Improve IT Governance: Regular user access entitlement reviews help organizations streamline identity and access management (IAM) by enforcing principle of least privilege (PoLP) and reducing security gaps.
By integrating automated user access review tools, businesses can eliminate manual errors, enhance security, and maintain regulatory compliance effortlessly.
3. Importance of User Access Reviews for Security & Compliance
User access reviews (UARs) are no longer optional—they are a necessity for organizations handling sensitive data. A 2023 Gartner report states that 75% of security failures will result from mismanaged identities and user access by 2025. Without periodic user access reviews, businesses risk unauthorized access, privilege creep, and compliance violations that can lead to financial and reputational damage.
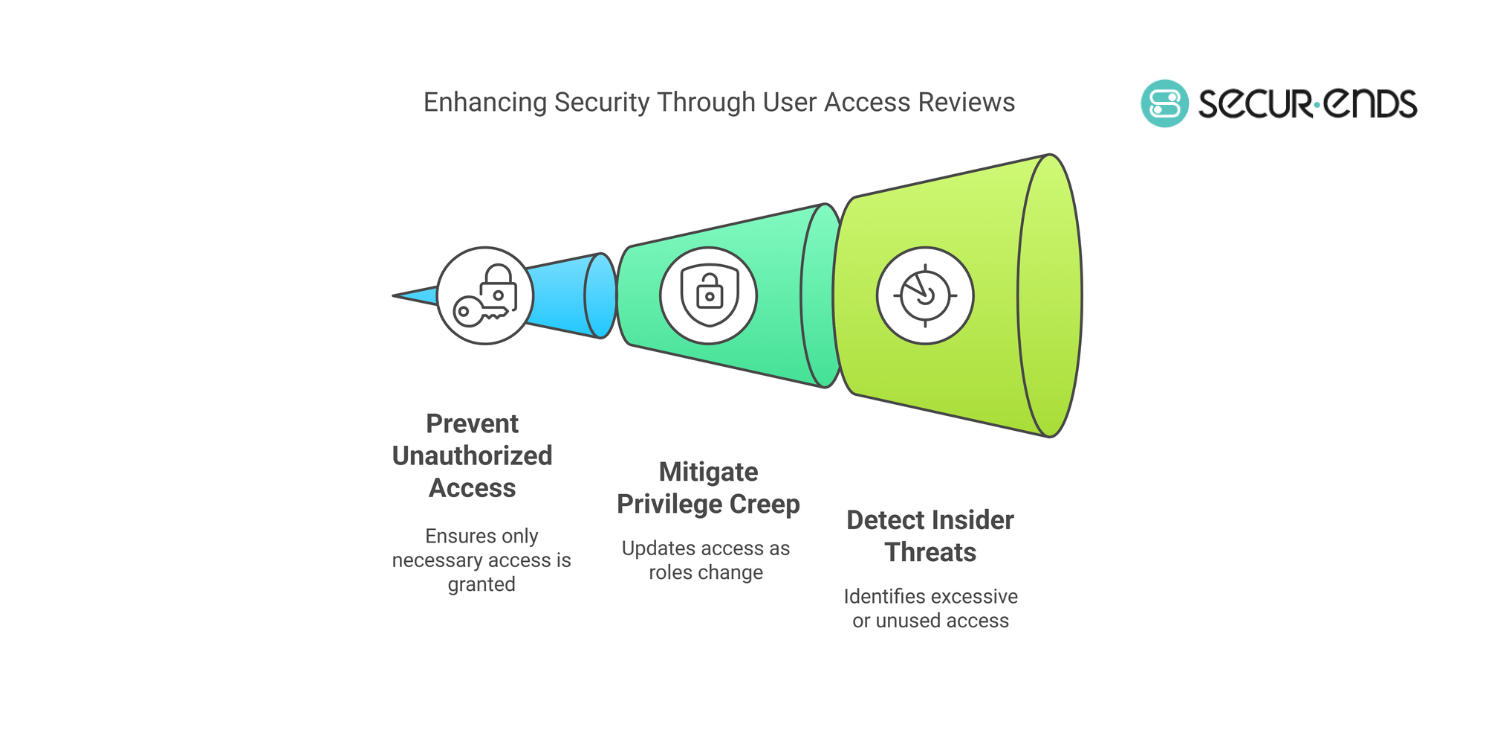
How User Access Reviews Enhance Security
- Prevents Unauthorized Access & Privilege Creep
- Over time, employees change roles or leave organizations, but their access often remains unchanged.
- A 2023 Verizon Data Breach Report found that 20% of data breaches involve former employees retaining access to company systems.
- Regular user entitlement reviews ensure only the right individuals have appropriate access privileges.
- Mitigates Insider Threats & Data Breaches
- According to IBM’s Cost of a Data Breach Report 2023, insider threats account for $11.45 million in average damages per incident.
- User access review audits help detect anomalies, such as excessive access rights or orphaned accounts that could be exploited.
Regulatory Compliance & User Access Reviews
Organizations must comply with strict data protection laws that mandate periodic access reviews. Non-compliance can lead to hefty fines and legal repercussions.
- SOX User Access Review (Sarbanes-Oxley Act): Requires companies to establish strong user access controls to protect financial records.
- HIPAA (Health Insurance Portability and Accountability Act): Mandates healthcare organizations to conduct periodic user access audits to protect patient data.
- GDPR (General Data Protection Regulation): Requires organizations to limit access to personal data and perform regular access reviews to ensure compliance.
- ISO 27001: A global security standard that mandates continuous access review processes to mitigate cybersecurity risks.
A study by Statista found that 53% of businesses struggle to maintain compliance with data security regulations due to inefficient manual access reviews. Automated user access review software simplifies the process by ensuring real-time audit trails, risk detection, and compliance reporting.
The Role of User Access Review Audits in Risk Mitigation
- Conducting periodic access reviews reduces the risk of data breaches by up to 50%, according to Cybersecurity & Infrastructure Security Agency (CISA).
- Automating user access reviews with tools like SecureEnds improves efficiency, ensuring organizations stay compliant while reducing security risks.
By implementing a robust user access review policy, organizations can proactively manage identity and access risks, stay compliant with regulatory frameworks, and enhance overall cybersecurity posture.
Read Also: User Access Reviews: 10 Automation Use Cases to Strengthen Cybersecurity and Compliance
4. How Frequently Should User Access Reviews Be Conducted?
Determining the right user access review frequency is essential to maintaining security and compliance. Conducting access reviews too infrequently increases the risk of unauthorized access and compliance violations, while overly frequent reviews can overwhelm IT and security teams with unnecessary workload.
Factors Influencing User Access Review Frequency
Several factors determine how often user access reviews (UARs) should be conducted, including:
- Regulatory Compliance Requirements
- SOX User Access Review: Requires quarterly or annual user access audits for financial data protection.
- HIPAA Compliance: Healthcare organizations must conduct regular access reviews to safeguard patient records.
- GDPR & ISO 27001: Mandates continuous access reviews to minimize unauthorized data exposure.
- Industry & Risk Levels
- High-risk industries (Finance, Healthcare, Government): Require quarterly or even monthly access reviews.
- Lower-risk industries (Retail, Hospitality, Small Businesses): Can conduct semi-annual or annual reviews.
- Number of Users & Systems
- Large enterprises with complex IT ecosystems need frequent user access entitlement reviews to prevent segregation of duties (SoD) violations.
- Companies with smaller teams and fewer applications may conduct bi-annual or annual access reviews.
Best Practices for Scheduling User Access Reviews
To optimize security and compliance, organizations should follow a structured user access review process:
- Quarterly Reviews: Recommended for industries handling financial records, personal data, or intellectual property.
- Semi-Annual Reviews: Suitable for mid-sized businesses with moderate risk exposure.
- Annual Reviews: Acceptable for small businesses or companies with minimal data sensitivity.
According to Gartner, companies that conduct user access reviews at least quarterly experience 40% fewer security incidents than those conducting them annually. Moreover, Statista reports that 64% of businesses fail compliance audits due to inconsistent access review policies.
Leading organizations are shifting to AI-driven user access review software to reduce compliance risks while ensuring continuous access review cycles. With SecureEnds, businesses can schedule automated reviews, integrate compliance controls, and maintain 24/7 security visibility.
5. User Access Review Process: Step-by-Step Guide
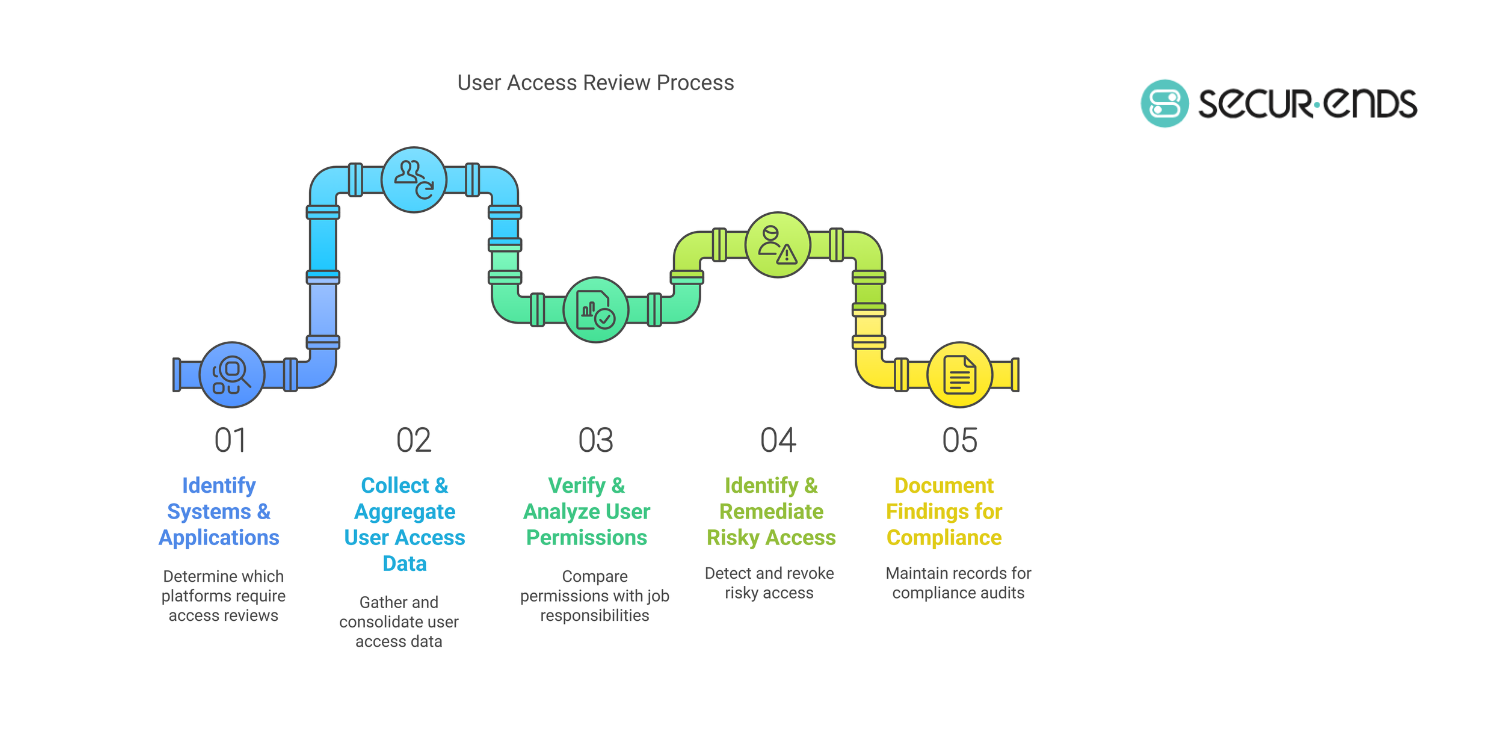
A well-structured user access review process ensures that only authorized users have appropriate access levels to systems and data. Without a standardized approach, businesses risk security breaches, compliance failures, and operational inefficiencies.
According to Okta’s 2024 Identity Governance Report, companies that implement a structured user access review process experience 80% fewer security incidents compared to those using ad-hoc methods. Below is a step-by-step guide to conducting efficient and compliant user access reviews.
Step 1: Identify Systems & Applications Requiring Access Reviews
- Determine which platforms, databases, and applications require regular user access reviews.
- Include identity and access management (IAM) systems, cloud storage platforms, HR databases, and financial applications.
- Ensure compliance with regulations like SOX User Access Review, HIPAA, and GDPR, which require regular access audits.
Step 2: Collect & Aggregate User Access Data
- Gather data on user accounts, roles, permissions, and last activity across all systems.
- Use user access review tools to automate data collection and consolidate access logs from various applications.
- Identify inactive accounts, excessive privileges, and unauthorized access.
Step 3: Verify & Analyze User Permissions
- Compare user roles and permissions with their current job responsibilities to detect any misalignments.
- Flag privilege creep where users have accumulated unnecessary access rights over time.
- Ensure segregation of duties (SoD) is maintained to prevent fraud and conflicts of interest.
Step 4: Identify & Remediate Risky Access
- Detect and revoke access for inactive accounts, former employees, and unauthorized users.
- Modify user permissions based on business needs and security policies.
- Implement risk-based access reviews by prioritizing high-risk accounts (e.g., admin accounts and financial data users).
Step 5: Document Findings for Compliance & Future Audits
- Maintain detailed records of access review decisions, including:
- User details (Name, Role, Department, Access Level)
- Approved, Revoked, or Modified status
- Review timestamps and reviewer comments
- Generate audit-ready reports to demonstrate compliance with SOX, HIPAA, and GDPR regulations.
How Automation Simplifies the User Access Review Process
According to Gartner, organizations that automate user access reviews reduce compliance risks by 60% and spend 70% less time on manual access audits. SecureEnds’ user access review software helps businesses:
✅ Automate data collection & access validation
✅ Generate real-time risk insights & audit reports
✅ Ensure continuous compliance & security
By following a structured access review process and leveraging automation, businesses can eliminate security gaps, improve compliance, and enhance operational efficiency.
6. Common Challenges in Manual User Access Reviews
Many organizations still rely on manual user access reviews, which are time-consuming, error-prone, and inefficient. According to Gartner, over 40% of companies struggle with compliance violations due to ineffective access review processes. Manual reviews often lead to delays, inaccuracies, and increased security risks.
Key Challenges of Manual User Access Reviews
1. Time-Consuming & Labor-Intensive
- Large enterprises manage thousands of user accounts across multiple applications, making manual reviews complex and resource-intensive.
- A 2023 Ponemon Institute study found that companies spend an average of 48 hours per user access review cycle, resulting in significant productivity losses.
2. High Risk of Human Errors
- Manually tracking access rights increases the likelihood of errors, such as failing to revoke permissions for former employees.
- A 2024 IBM Security Report found that 30% of insider security incidents result from incorrectly assigned access rights.
3. Difficulty Tracking Access Across Multiple Systems
- Organizations use a mix of on-premise, cloud, and hybrid systems, making it challenging to consolidate user access data.
- A Statista survey found that 57% of security teams struggle with visibility across different IT environments, increasing the risk of unauthorized access.
4. Delays in Remediation & Compliance Risks
- Regulatory frameworks like SOX, HIPAA, and GDPR require timely user access reviews and immediate remediation of excessive privileges.
- A 2023 SOX Compliance Audit found that 80% of companies failed initial user access audits due to delayed revocations of excessive permissions.
5. Lack of Audit-Ready Documentation
- Without automated tracking, businesses struggle to provide accurate audit trails for compliance reporting.
- A Forrester report found that companies without access review tools spend 4x more time preparing compliance reports.
7. Best Practices for Conducting User Access Reviews Efficiently
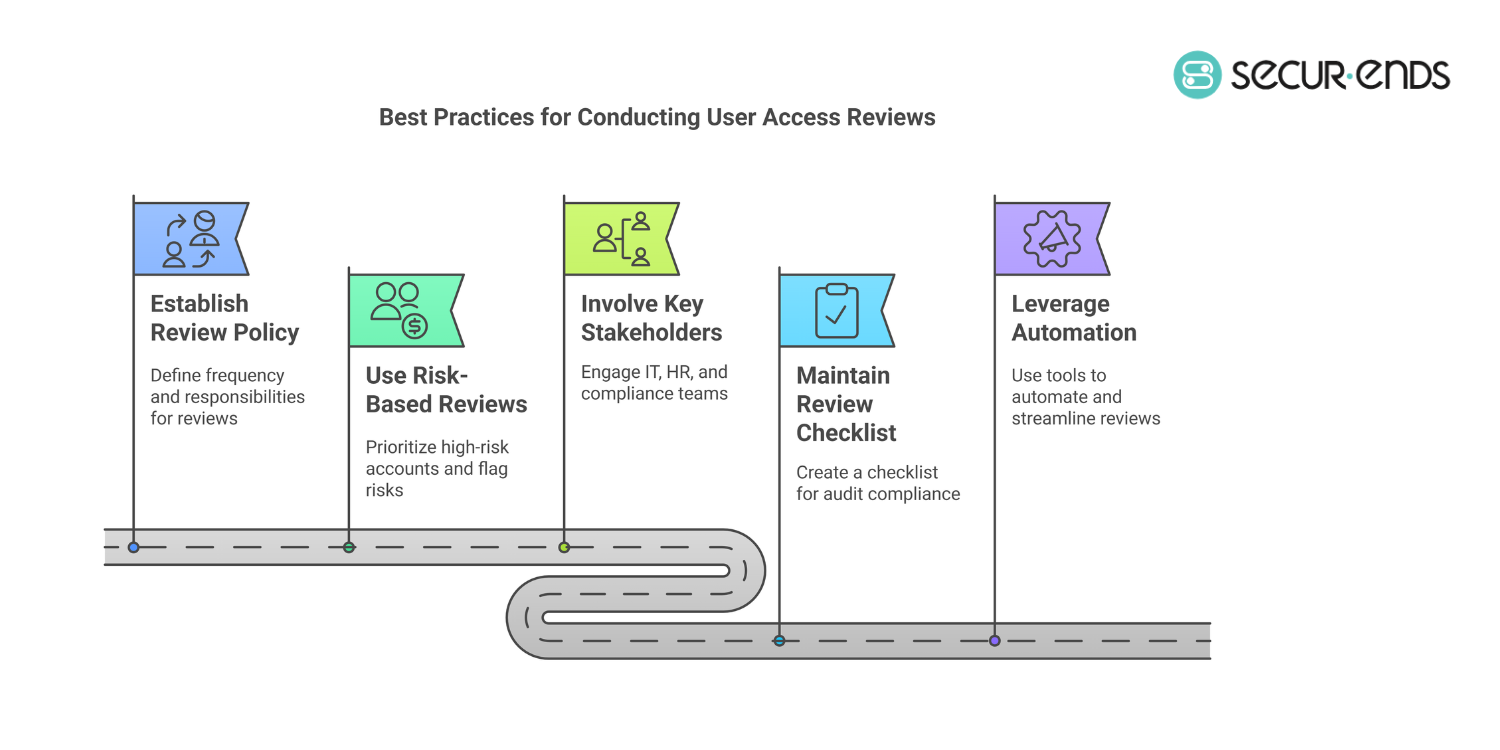
Implementing best practices for user access reviews (UARs) ensures that businesses maintain security, compliance, and operational efficiency. According to Gartner, organizations that follow structured user access review policies reduce compliance risks by 60% and cut manual review time by 70%.
1. Establish a Clear User Access Review Policy
- Define how frequently user access reviews should be conducted (quarterly, semi-annually, or annually).
- Specify who is responsible (IT, HR, compliance teams) for conducting reviews.
- Set up automated alerts and workflows to streamline the review process.
2. Use Risk-Based Reviews to Prioritize High-Risk Accounts
- Focus on privileged users, such as administrators, financial officers, and IT personnel, as they pose the highest security risks.
- Implement real-time risk scoring to flag suspicious access patterns.
- According to Okta’s Identity Report, businesses using risk-based user access reviews experience 50% fewer insider threats.
3. Involve Key Stakeholders in the Review Process
- IT Teams: Validate access permissions and enforce identity governance policies.
- HR Teams: Ensure access aligns with employees’ current job roles and responsibilities.
- Compliance Officers: Verify that reviews meet SOX, HIPAA, and GDPR requirements.
4. Maintain a User Access Review Checklist for Audits
A structured user access review checklist ensures no critical steps are missed:
✅ Define Scope: Identify applications, databases, and systems requiring access reviews.
✅ Gather Access Data: Collect user role and permission details.
✅ Review & Validate: Audit excessive privileges and inactive accounts.
✅ Revoke Unnecessary Access: Remove outdated or unauthorized permissions.
✅ Document Everything: Store logs for compliance audits.
5. Leverage Automation for Faster & More Accurate Reviews
- Manual reviews are error-prone and time-consuming—automating UARs improves efficiency.
- Statista reports that companies using user access review software cut compliance audit preparation time by 80%.
- Tools like SecureEnds simplify user entitlement reviews by:
✅ Automating access validation
✅ Generating real-time risk insights
✅ Providing audit-ready reports
By following these best practices, businesses can enhance security, reduce compliance risks, and streamline the user access review process.
8. The Role of User Access Review Software in Automating UARs
With the growing complexity of IT environments, manual user access reviews are no longer sustainable. Businesses are turning to user access review software to automate workflows, enhance security, and maintain compliance. According to Gartner, organizations that adopt identity governance and administration (IGA) solutions reduce access-related security risks by 50%.
What is User Access Review Software?
User access review tools help organizations automate the review, approval, and remediation of user access permissions across multiple systems. These tools integrate with identity and access management (IAM) platforms, ensuring real-time monitoring of user privileges, role changes, and security risks.
How User Access Review Software Streamlines IAM & Compliance
- Automated Access Reviews & Approval Workflows
- Eliminates the need for manual data collection and spreadsheet tracking.
- Ensures real-time user entitlement reviews to detect privilege creep.
- A Forrester study found that companies using automated UAR tools experience 70% faster compliance audits.
- Seamless Integration with IAM & IGA Platforms
- Modern identity access management (IAM) solutions rely on automated access controls for better security.
- SecureEnds integrates with IAM systems like Active Directory, Okta, and Azure AD to ensure continuous access governance.
- Reduces Compliance Risks & Audit Failures
- Regulations like SOX, HIPAA, and GDPR mandate regular access certifications to prevent unauthorized access.
- Statista reports that 64% of businesses fail compliance audits due to poor access control management.
- Automated user access review procedures ensure that excessive permissions are revoked on time, reducing compliance failures.
Key Features to Look for in User Access Review Tools
✅ Automated Access Reviews: Schedule and execute periodic access certifications.
✅ AI-Powered Risk Analysis: Detect high-risk accounts and segregation of duties (SoD) violations.
✅ Audit-Ready Reports: Generate SOX User Access Review logs in one click.
✅ Seamless IAM Integrations: Connect with Okta, Azure AD, AWS IAM, and more.
By leveraging identity governance and administration tools, businesses can enhance IAM, enforce security policies, and simplify compliance processes. SecureEnds’ UAR solution helps organizations automate reviews, mitigate security risks, and maintain a strong compliance posture.
9. Automating User Access Reviews: Benefits & How It Works
As organizations scale, managing user access manually becomes inefficient, error-prone, and a security risk. Automating user access reviews (UARs) with identity and governance solutions helps businesses maintain security, streamline compliance, and enhance operational efficiency. According to Gartner, by 2026, 60% of organizations will use AI-driven identity governance solutions to reduce security risks associated with excessive user permissions and orphaned accounts.
Why Businesses Should Automate User Access Reviews
- Eliminates Manual Errors & Increases Accuracy
- Manual user access review procedures rely on spreadsheets and human validation, increasing the risk of overlooked access privileges.
- A Forrester study found that 47% of security breaches are caused by mismanaged user access controls.
- Enhances Compliance with SOX, HIPAA, and GDPR
- Regulations mandate that businesses perform regular user access reviews and document access changes.
- A 2023 IBM Security Report found that businesses using automated user access review tools reduce compliance violations by 72%.
- Improves Identity & Access Management (IAM) Efficiency
- Identity and governance solutions automate access certification, ensuring timely reviews and risk detection.
- SecureEnds integrates with IAM systems like Okta, Azure AD, and AWS IAM to enforce least privilege access policies.
How Automated User Access Reviews Work
- Data Collection & Analysis
- The system scans all users, roles, and permissions across on-premise, cloud, and hybrid environments.
- AI-powered identity governance solutions detect anomalous access behaviors.
- Automated Access Certification & Risk Scoring
- Users receive automated notifications for access review approvals or revocations.
- Risk-based prioritization ensures high-risk accounts are reviewed first.
- Instant Revocation & Compliance Reporting
- Orphaned accounts and excessive permissions are automatically flagged and revoked.
- Generates audit-ready reports for SOX, HIPAA, and GDPR compliance.
10. How SecureEnds Automates User Access Reviews
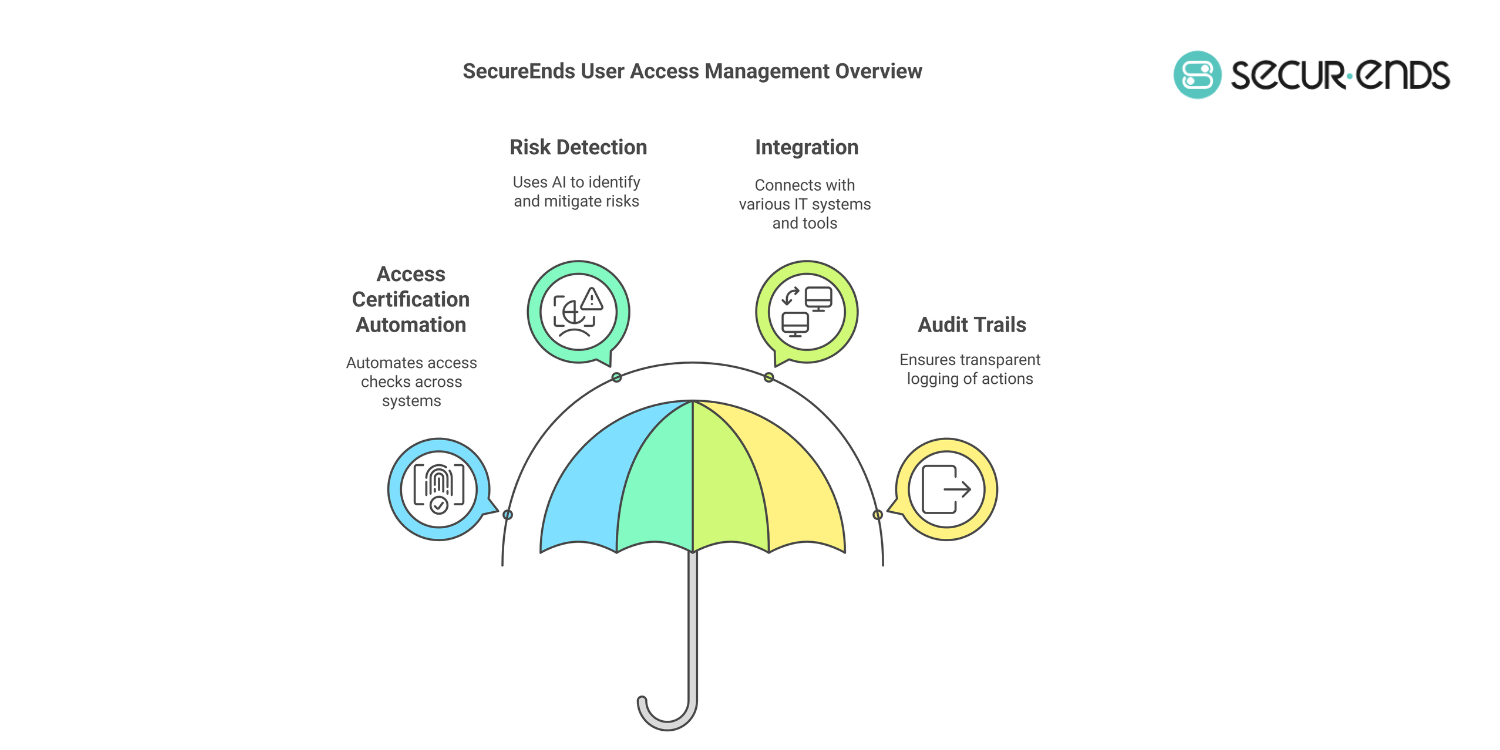
Traditional user access review processes are time-consuming, error-prone, and compliance-heavy. SecureEnds revolutionizes access governance by automating access certifications, enforcing security policies, and simplifying compliance audits. According to Gartner, organizations that deploy identity governance solutions like SecureEnds reduce access-related security risks by 50% and cut compliance review time by 70%.
SecureEnds’ Approach to Access Certification & Reviews
SecureEnds provides a cloud-native, AI-driven user access review software that enables businesses to:
✅ Automate access certifications across on-prem, cloud, and hybrid systems
✅ Detect excessive permissions, orphaned accounts, and SoD violations in real time
✅ Generate audit-ready reports for SOX, HIPAA, and GDPR compliance
How SecureEnds Enhances Identity Governance & Security
- AI-Driven Risk Detection & Automated Remediation
- Uses machine learning algorithms to analyze access patterns and detect anomalous user behavior.
- Automatically flags high-risk accounts and revokes unauthorized access permissions.
- A 2023 Forrester Report found that companies using AI-driven identity and governance solutions reduce insider threats by 55%.
- Seamless Integration with Existing IT Ecosystems
- Connects with IAM systems, ITSM tools, cloud platforms, and business-critical applications.
- Supports integrations with 50+ platforms, including Azure AD, AWS IAM, Okta, Workday, and Salesforce.
- Real-Time Audit Trails & Compliance Automation
- SecureEnds automatically logs every access review action, ensuring full audit transparency.
- Generates SOX user access review reports in seconds, reducing compliance workloads.
- According to IBM Security, automated UAR solutions cut compliance costs by up to $1.5 million per year.
11. SecureEnds User Access Review Connectors & Integrations
Seamless integration with enterprise systems is crucial for efficient user access reviews. SecureEnds offers pre-built connectors that enable organizations to automate access controls across multiple platforms, reducing manual efforts and improving compliance..
Why Integrations Matter in User Access Reviews
- Centralized Identity Management: Eliminates the need for manual data extraction by synchronizing user access data across IT ecosystems.
- Faster Compliance Audits: Pre-built user access review tools generate audit-ready reports for SOX, HIPAA, and GDPR in seconds.
- Enhanced Security & Risk Detection: Real-time identity access management (IAM) integrations ensure immediate detection of excessive privileges and orphaned accounts.
SecureEnds’ Pre-Built User Access Review Connectors
✅ Identity & Access Management (IAM) Connectors
✔ Active Directory (AD), Azure AD, AWS IAM, Okta, OneLogin, JumpCloud
✅ Cloud & Storage Connectors
✔ AWS, Google Cloud, Google Drive, AWS Cloud DB & Storage
✅ ITSM & Ticketing Systems
✔ ServiceNow, Zendesk, TeamDynamix, DesktopPro, Freshdesk
✅ Collaboration & Code Repositories
✔ Slack, Confluence, Jira, SharePoint, GitHub, GitLab, Bitbucket, BOX
✅ HR, Finance & ERP Systems
✔ Workday, ADP, Paylocity, SAP SuccessFactors, NetSuite, Microsoft Dynamics, UKG, Fiserv, Jack Henry Silverlake, Ceridian Dayforce, GFX
✅ Databases & File Transfer Connectors
✔ MS SQL Server, MySQL, Oracle via Flex, Postgres via Flex, DB Flex, Flex SFTP, Flex Folder
✅ Other Key Business Applications
✔ Salesforce, Office 365, Docusign, Dropbox, Lawson, WebAPI, Thycotic, RPA, Symitar, Concur
A Statista study found that organizations integrating user access review software with IAM solutions improve compliance efficiency by 60% and reduce access risks by 45%. SecureEnds’ extensive integration capabilities ensure businesses can automate access reviews effortlessly, enforce least privilege access, and simplify compliance audits.
12. SOX User Access Review: What You Need to Know
The Sarbanes-Oxley Act (SOX) enforces strict regulations on how companies handle financial data, ensuring transparency, accuracy, and security. SOX User Access Review is a critical component of compliance, requiring organizations to validate, audit, and monitor access permissions to financial systems. Failure to comply can lead to hefty fines, legal penalties, and reputational damage.
Why SOX User Access Reviews Are Required
- Prevents Financial Fraud: Ensures that only authorized users can access financial data, reducing the risk of fraudulent transactions and insider threats.
- Ensures Data Integrity: Enforces segregation of duties (SoD), preventing conflicts of interest in financial reporting.
- Regulatory Compliance: Companies listed on U.S. stock exchanges must perform access reviews regularly to meet SOX requirements.
Key SOX Compliance Requirements for User Access Reviews
- Access Controls & User Authentication
- Enforce least privilege access by granting users only the permissions necessary for their job roles.
- Monitor high-risk user accounts, such as administrators and finance personnel.
- Periodic User Access Reviews & Certification
- Conduct quarterly or semi-annual access reviews for financial applications and databases.
- Identify inactive, excessive, or unauthorized user permissions and revoke unnecessary access.
- Audit Trail & Documentation
- Maintain detailed records of who has access to financial systems and who approved the access.
- Generate SOX-compliant reports to demonstrate due diligence in access management.
SOX User Access Review Checklist
✔ Define Scope: Identify financial systems that require periodic reviews.
✔ Gather User Access Data: Collect and verify user roles and permissions.
✔ Review & Validate: Flag excessive access and inactive accounts.
✔ Remediate Risks: Revoke unnecessary permissions and enforce access policies.
✔ Document & Report: Maintain compliance logs for SOX audits.
13. User Access Review Templates: How to Standardize Your Process
Standardizing user access reviews (UARs) with structured templates ensures efficiency, accuracy, and compliance. A well-defined user access review template simplifies access certification, making it easier for IT, compliance, and security teams to audit and validate user permissions across multiple systems.
Why Standardized User Access Review Templates Are Important
✔ Consistency: Ensures uniform review processes across all departments and applications.
✔ Compliance: Aligns with SOX, HIPAA, GDPR, and ISO 27001 access control requirements.
✔ Efficiency: Reduces manual errors and access-related security risks.
✔ Audit Readiness: Generates structured reports for compliance audits.
What Should a User Access Review Template Include?
A well-structured user access review template should capture:
✅ User Information: Name, email, job title, department.
✅ Application & System Access: List of platforms the user has access to.
✅ Access Level: Read, Write, Admin, or Custom roles.
✅ Review Status: Approved, Modified, Revoked.
✅ Reviewer Comments: Justifications for changes made.
✅ Timestamp & Approvals: To maintain audit trails.
📂 User Access Review Template (Excel Format)
| User | Department | Application | Access Level | Review Status | Reviewer Comments | Approval Date |
| John Doe | Finance | SAP ERP | Admin | Revoked | No longer in this role | 2024-03-10 |
| Sarah Lee | HR | Workday | Read/Write | Approved | Still required for payroll access | 2024-03-10 |
📥 Download User Access Review Template (Excel) – Click Here
14. User Access Review Checklist
A structured User Access Review (UAR) checklist ensures organizations conduct thorough and compliant access audits. By following a predefined checklist, security and compliance teams can identify unauthorized access, enforce least privilege policies, and prevent security risks.
According to Gartner, companies that implement a user access review checklist improve compliance by 50% and reduce access-related security risks by 45%.
✅ User Access Review Checklist
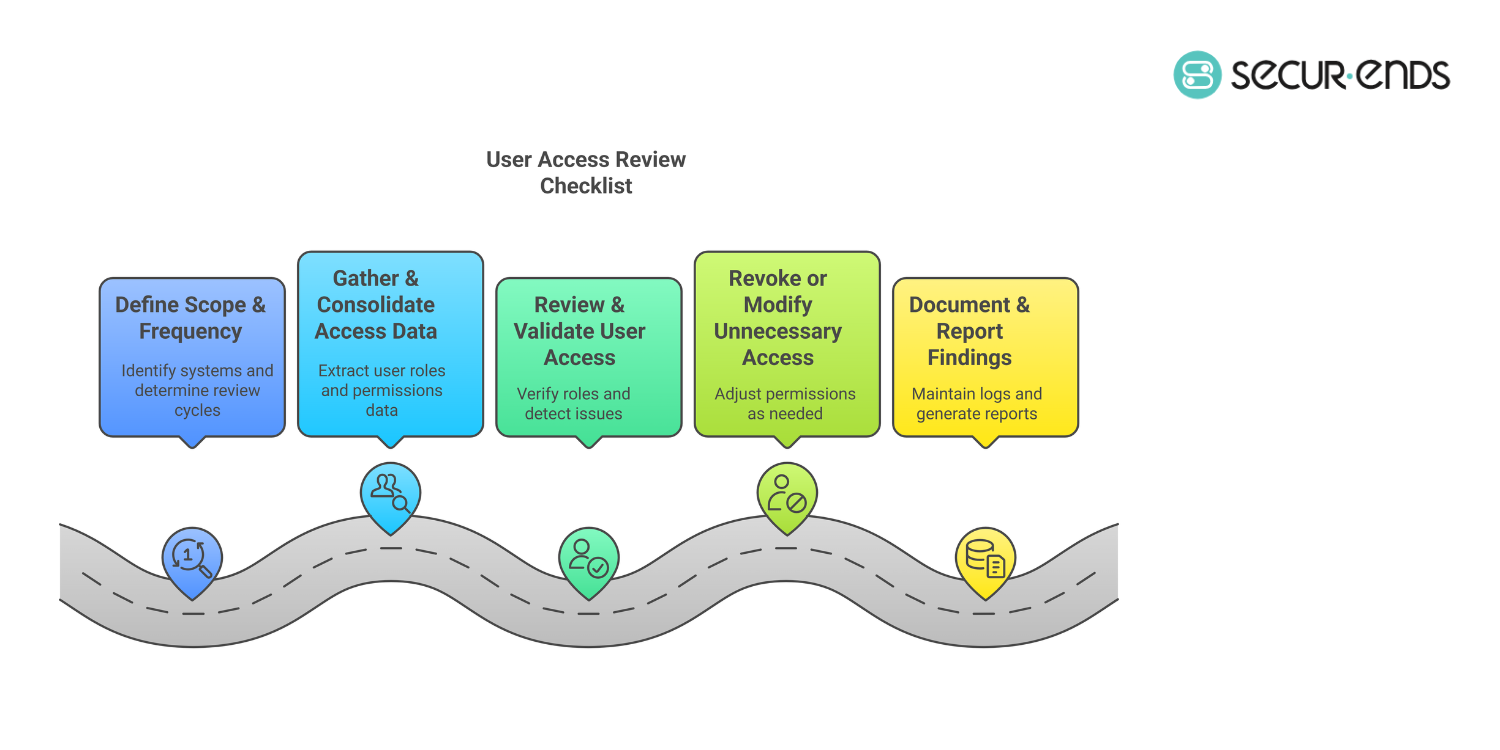
✔ Define Scope & Frequency:
- Identify systems, applications, and databases requiring access reviews.
- Determine review cycles (quarterly, semi-annual, annual) based on risk level and compliance needs.
✔ Gather & Consolidate Access Data:
- Extract user roles, permissions, and last login data from all critical systems.
- Use identity governance solutions to automate data aggregation.
✔ Review & Validate User Access:
- Verify active users, job roles, and access rights.
- Detect privilege creep, orphaned accounts, and excessive permissions.
- Ensure segregation of duties (SoD) to prevent fraud.
✔ Revoke or Modify Unnecessary Access:
- Revoke access for inactive, unauthorized, or terminated users.
- Adjust permissions for users with excessive access rights.
✔ Document & Report Findings:
- Maintain audit logs of who reviewed, approved, and modified access.
- Generate SOX, HIPAA, and GDPR-compliant reports for regulatory audits.
15. Choosing the Right User Access Review Tools & Software
✔ Define Scope & Frequency:
- Identify systems, applications, and databases requiring access reviews.
- Determine review cycles (quarterly, semi-annual, annual) based on risk level and compliance needs.
✔ Gather & Consolidate Access Data:
- Extract user roles, permissions, and last login data from all critical systems.
- Use identity governance solutions to automate data aggregation.
✔ Review & Validate User Access:
- Verify active users, job roles, and access rights.
- Detect privilege creep, orphaned accounts, and excessive permissions.
- Ensure segregation of duties (SoD) to prevent fraud.
✔ Revoke or Modify Unnecessary Access:
- Revoke access for inactive, unauthorized, or terminated users.
- Adjust permissions for users with excessive access rights.
✔ Document & Report Findings:
- Maintain audit logs of who reviewed, approved, and modified access.
- Generate SOX, HIPAA, and GDPR-compliant reports for regulatory audits.
Comparing Manual vs. Automated User Access Reviews
| Feature | Manual Reviews | Automated Reviews (SecureEnds) |
| Time Required | Weeks or months | Minutes to hours |
| Accuracy | Prone to human error | AI-driven precision |
| Compliance Risk | High due to delays & oversight | Low with automated audit reports |
| Scalability | Difficult for large organizations | Handles thousands of users effortlessly |
| Integration | Limited | Seamless IAM & IGA integrations |
A Statista report found that companies using AI-driven identity and governance solutions like SecureEnds reduce security incidents by 50% and improve access review compliance by 80%.
By investing in the right user access review software, businesses can automate compliance, enhance security, and improve operational efficiency.
16. Future of User Access Management: Trends & Predictions
As cyber threats evolve and compliance regulations tighten, the future of user access management (UAM) will be shaped by AI-driven automation, continuous monitoring, and adaptive access controls. According to Gartner, by 2026, 70% of organizations will adopt AI-powered identity governance solutions to enhance security and compliance.
Key Trends Shaping the Future of User Access Reviews
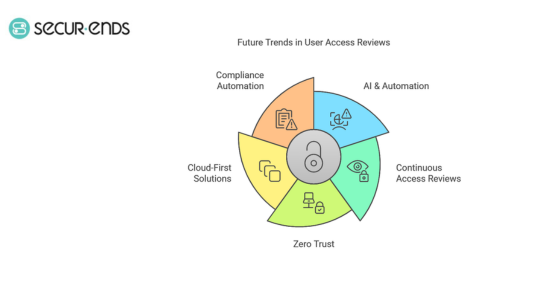
1. AI & Automation in Identity Governance
- Traditional manual access reviews are being replaced by AI-driven access review tools that provide real-time risk analysis and automated remediation.
- A Forrester study found that businesses using AI-powered access reviews experience 50% fewer compliance violations and 40% faster review cycles.
2. Shift Towards Continuous Access Reviews
- Instead of quarterly or annual reviews, companies are moving to continuous, real-time user access monitoring.
- Statista reports that organizations using continuous access reviews improve security by 45% and reduce insider threats.
3. Zero Trust & Adaptive Access Controls
- The Zero Trust model ensures that no user or device is trusted by default—access is granted based on real-time verification.
- Identity access management (IAM) solutions now integrate with risk-based adaptive authentication, requiring additional security layers for high-risk actions.
4. Cloud-First Identity Governance Solutions
- More businesses are shifting to cloud-native identity governance solutions that integrate with multi-cloud environments.
- Gartner predicts that 80% of organizations will rely on cloud-based identity governance platforms by 2025 to support remote work and hybrid IT infrastructures.
5. Increased Focus on Compliance Automation
- Regulations like SOX, HIPAA, and GDPR are driving demand for automated compliance solutions.
- SecureEnds’ automated user access review software ensures businesses meet compliance without manual workload.
A Statista survey found that companies investing in AI-powered user access management reduce security risks by 50% and improve compliance efficiency by 75%. With SecureEnds, businesses can future-proof access governance, streamline compliance, and enhance cybersecurity resilience.
17. SecureEnds: Get Started with Automated User Access Reviews Today
Managing user access reviews (UARs) manually is time-consuming, error-prone, and non-scalable. SecureEnds simplifies access certifications, risk detection, and compliance audits through AI-driven automation, allowing businesses to eliminate security risks, streamline compliance, and improve operational efficiency.
Why Choose SecureEnds for User Access Reviews?
✔ 100% Automation: Eliminate manual errors and reduce review time by 75% (Gartner).
✔ AI-Powered Risk Analysis: Detect and remediate excessive privileges, orphaned accounts, and SoD violations.
✔ Seamless Integrations: Connect with Active Directory, Azure AD, AWS IAM, Okta, Workday, Salesforce, ServiceNow, and 50+ enterprise applications.
✔ Audit-Ready Compliance Reporting: Generate SOX, HIPAA, GDPR, and ISO 27001-compliant reports instantly.
✔ Real-Time Access Monitoring: Continuously track and flag suspicious user access behavior.
Join 100+ enterprises automating identity governance with SecureEnds. Future-proof your security and compliance today!