The Ultimate Guide to Identity Access Management Solutions
The Ultimate Guide to Identity Access Management Solutions

Introduction
In an era where cyber threats are more sophisticated than ever, businesses face a critical challenge—controlling who has access to their systems and data. Unauthorized access, insider threats, and data breaches can lead to severe financial and reputational damage. This is where Identity and Access Management (IAM) solutions come into play.
IAM solutions help organizations regulate and monitor user access, ensuring that employees, partners, and customers can securely interact with digital systems without compromising security. These solutions go beyond simple login credentials, incorporating multi-factor authentication (MFA), role-based access control (RBAC), and biometric verification to strengthen security.
Over the years, IAM technology has evolved from basic password management tools to comprehensive platforms that integrate with cloud environments, artificial intelligence (AI), and automation. As businesses increasingly move towards digital transformation, adopting a robust IAM solution is no longer optional—it is a necessity for securing sensitive data and meeting regulatory requirements.
This article delves into what IAM solutions are, why they are essential for businesses, and how they have evolved to keep pace with modern cybersecurity challenges.
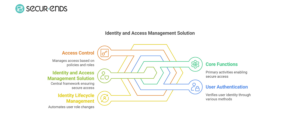
2. What is an Identity and Access Management Solution?
An identity and access management solution is a framework of technologies, policies, and processes that ensure the right individuals have the appropriate access to an organization’s digital resources. It is designed to manage and control user identities, authentication, and authorization across systems, applications, and networks.
At its core, an identity access management solution enables businesses to define and enforce access policies, ensuring users can only access the information and systems necessary for their roles. The primary functionalities of an identity and access management solution include:
- User Authentication – Verifying a user’s identity using passwords, multi-factor authentication (MFA), biometrics, or other authentication methods.
- Access Control – Granting or restricting access based on predefined policies, roles, and permissions.
- Identity Lifecycle Management – Automating user provisioning, de-provisioning, and role assignments as employees join, move within, or leave an organization.
- Single Sign-On (SSO) – Allowing users to log in once and gain access to multiple systems without re-entering credentials.
- Privileged Access Management (PAM) – Securing and monitoring access for high-level users with elevated permissions.
- Compliance and Audit Reporting – Helping organizations meet regulatory requirements by tracking and reporting access activities.
How IAM Differs from Traditional Security Systems
Unlike traditional security systems that focus on perimeter defense (such as firewalls and antivirus software), an identity access management solution prioritizes identity-based security. Traditional security models assume that threats come from outside the organization, while IAM solutions recognize that unauthorized access can occur internally as well.
Key differences include:
- Identity-Centric Security: Traditional security focuses on securing networks and endpoints, while IAM solutions secure access at the user level.
- Automation and AI Integration: Modern identity and access management solutions leverage artificial intelligence (AI) and automation to detect anomalies and enforce real-time security measures, unlike traditional manual security processes.
- Cloud and Remote Access: While traditional security systems are often designed for on-premises environments, IAM solutions support cloud-based applications and remote workforces, enabling secure access from anywhere.
By implementing a robust identity access management solution, organizations can enhance security, streamline user access, and ensure compliance with industry regulations—all while reducing the risk of unauthorized access and data breaches.
3. Why Do Organizations Need IAM Solutions?
As organizations increasingly rely on digital systems, securing user access has become a top priority. Without access management solutions, businesses are vulnerable to cyber threats, compliance risks, and operational inefficiencies. Implementing the best identity management solutions ensures secure, seamless, and compliant access to critical resources.
Security Threats Without IAM
Without access management solutions, organizations face significant security risks, including:
- Unauthorized Access: Weak or shared credentials can lead to data breaches and insider threats.
- Identity Theft and Credential Abuse: Cybercriminals exploit stolen passwords to infiltrate systems.
- Lack of Visibility: Organizations struggle to monitor and manage user activities across multiple platforms.
- Insider Threats: Employees or contractors with excessive permissions can misuse sensitive data.
The best identity management solutions mitigate these risks by enforcing strong authentication, access controls, and continuous monitoring.
Compliance and Regulatory Requirements
Many industries are subject to strict compliance regulations that mandate secure identity and access management. Regulations such as GDPR, HIPAA, PCI-DSS, and SOX require organizations to protect user identities and control access to sensitive data.
Access management solutions help businesses meet these requirements by:
- Implementing role-based and least-privilege access controls.
- Maintaining audit logs and access reports for compliance audits.
- Enforcing multi-factor authentication (MFA) and encryption for sensitive data.
Failing to comply with these regulations can result in hefty fines, legal consequences, and reputational damage.
Enhancing User Experience and Productivity
Beyond security and compliance, the best identity management solutions improve user experience and operational efficiency. They streamline access to systems and applications, reducing friction in daily workflows. Key benefits include:
- Single Sign-On (SSO): Users can log in once and access multiple applications without repeated authentication.
- Automated User Provisioning: New employees get instant access to necessary tools, reducing onboarding delays.
- Self-Service Password Management: Users can reset passwords without IT intervention, minimizing downtime.
By implementing access management solutions, businesses create a secure, efficient, and user-friendly environment, ultimately driving productivity and innovation.
4. Key Features of an IAM Solution
A robust IAM solution is essential for securing digital identities, managing user access, and ensuring compliance. The right identity management solution provides a comprehensive set of features to streamline authentication, authorization, and user lifecycle management while enhancing security and user experience.
Authentication and Authorization
One of the core functions of an IAM solution is to verify user identities before granting access to systems and applications. Authentication ensures that users are who they claim to be, while authorization determines what resources they can access based on predefined policies.
Key aspects include:
- Role-Based Access Control (RBAC): Users are assigned access based on their job roles.
- Attribute-Based Access Control (ABAC): Access is granted dynamically based on user attributes, such as department or location.
- Policy-Based Access Control (PBAC): Access rules are enforced according to organizational policies.
Single Sign-On (SSO)
A critical feature of any identity management solution, Single Sign-On (SSO) allows users to log in once and gain access to multiple applications without the need to re-enter credentials. This enhances security while reducing password fatigue and IT support requests.
Benefits of SSO include:
- Improved user experience by eliminating multiple logins.
- Reduced risk of password-related breaches.
- Centralized access control and monitoring.
Multi-Factor Authentication (MFA)
To strengthen security, an IAM solution integrates Multi-Factor Authentication (MFA), requiring users to verify their identity through multiple authentication factors:
- Something You Know – Passwords or security questions.
- Something You Have – One-time passcodes (OTP), smart cards, or security keys.
- Something You Are – Biometric authentication such as fingerprints or facial recognition.
By implementing MFA, organizations can significantly reduce the risk of unauthorized access, phishing attacks, and credential theft.
User Provisioning and Deprovisioning
An efficient identity management solution automates user provisioning and deprovisioning, ensuring that users have the right access at the right time.
- User Provisioning: Automatically grants access to new employees based on their roles.
- User Deprovisioning: Revokes access when employees leave the organization, reducing security risks.
- Lifecycle Management: Adjusts user permissions as roles change, ensuring compliance with security policies.
By leveraging these key features, an IAM solution enhances security, simplifies access management, and supports compliance with regulatory requirements.
5. Types of IAM Solutions Available in the Market
Organizations have several options when it comes to implementing identity management systems, each catering to different business needs, infrastructure models, and security requirements. The three primary types of IAM solutions available in the market are on-premises IAM solutions, cloud-based IAM solutions, and hybrid IAM solutions.
On-Premises IAM Solutions
On-premises IAM solutions are deployed within an organization’s own data centers, giving businesses complete control over their identity management systems. These solutions are typically preferred by industries with strict regulatory and security requirements, such as banking, healthcare, and government sectors.
Key Benefits:
- Full control over security and data management.
- Customizable to fit specific business processes.
- Does not rely on third-party cloud providers, reducing external risks.
Challenges:
- High upfront costs for infrastructure and maintenance.
- Requires dedicated IT teams for management and updates.
- Limited scalability compared to cloud-based IAM solutions.
Cloud-Based IAM Solutions
With the increasing adoption of cloud computing, many organizations are turning to cloud-based IAM solutions to streamline identity and access management. These solutions are hosted by third-party providers and delivered as a service, reducing the burden of on-premises infrastructure.
Key Benefits:
- Scalability: Easily adjusts to business growth and changing user demands.
- Cost-Effectiveness: Reduces hardware and maintenance costs.
- Anywhere Access: Enables secure authentication for remote employees and cloud applications.
- Automatic Updates: Managed by the service provider to ensure up-to-date security measures.
Challenges:
- Less direct control over security and compliance compared to on-premises IAM solutions.
- Dependency on cloud providers for uptime and data protection.
- Potential concerns over data sovereignty and regulatory compliance.
Hybrid IAM Solutions
For organizations seeking a balance between security, flexibility, and scalability, hybrid IAM solutions offer the best of both worlds. These solutions integrate on-premises IAM solutions with cloud-based IAM solutions, allowing businesses to manage identities across multiple environments.
Key Benefits:
- Flexibility: Allows organizations to maintain sensitive data on-premises while leveraging cloud efficiencies.
- Enhanced Security: Provides layered security by integrating both local and cloud-based identity management.
- Compliance Support: Helps businesses meet regulatory requirements while benefiting from cloud advancements.
Challenges:
- Complex integration and management across different environments.
- Requires a well-planned IAM strategy to ensure seamless user experiences.
- Potential for increased costs due to dual infrastructure management.
Choosing the Right Identity Management System
Selecting the right IAM solution depends on an organization’s specific security requirements, budget, and operational needs. While enterprise IAM solutions may benefit from the robust control of on-premises IAM solutions, startups and growing businesses often find cloud-based IAM solutions more cost-effective. A hybrid IAM solution is ideal for businesses that require a balance between security and scalability.
By understanding these options, organizations can implement identity management systems that best align with their digital security and operational goals.
6. How Cloud-Based IAM Solutions Are Changing the Security Landscape
As businesses transition to digital-first operations, securing user identities has become crucial. Cloud-based IAM solutions are transforming identity management by offering scalable, cost-effective, and automated security measures. Unlike traditional on-premises identity management systems, cloud IAM solutions provide seamless access, enhanced compliance, and reduced IT overhead, making them the best identity management solutions for modern enterprises.
Benefits of Cloud IAM
Cloud IAM solutions offer several advantages over traditional IAM, including scalability, cost savings, and improved security. These solutions allow businesses to scale identity management effortlessly while reducing infrastructure costs. Features like Single Sign-On (SSO) and Multi-Factor Authentication (MFA) enhance user experience by providing seamless and secure access. Additionally, cloud-based IAM solutions support remote work by enabling users to authenticate securely from any location. Another major benefit is automated security updates and compliance management, reducing IT workload while ensuring that organizations meet industry regulations.
Cloud IAM vs. Traditional IAM
Unlike traditional IAM solutions, which require in-house infrastructure and IT teams for maintenance, cloud IAM solutions are hosted and managed by third-party providers, eliminating the need for costly hardware investments. They offer better scalability, allowing businesses to expand or adjust their access management without major infrastructure changes. Security updates are handled automatically by the service provider, reducing the risk of vulnerabilities. Traditional IAM systems, on the other hand, require manual updates, making them more time-consuming and potentially less secure. Additionally, cloud IAM solutions provide secure remote access, making them more suitable for modern work environments, while traditional IAM systems are primarily designed for internal networks.
Security Considerations for Cloud-Based IAM
While cloud-based IAM solutions provide significant benefits, businesses must implement strong security measures to mitigate potential risks. Encrypting identity data both in transit and at rest ensures that sensitive information remains protected from cyber threats. Adopting a Zero Trust Security Model further strengthens security by continuously verifying users and devices before granting access. Compliance is another critical aspect, and businesses must ensure that their cloud IAM solutions adhere to regulations like GDPR, HIPAA, and PCI-DSS to avoid penalties and security breaches. Additionally, implementing well-defined identity governance and access policies helps organizations monitor and control user activities, reducing the risk of insider threats and unauthorized access.
By leveraging the best identity management solutions, businesses can enhance security, improve operational efficiency, and future-proof their access management strategy. Cloud IAM solutions are not just a modern alternative—they are the key to securing digital identities in an evolving cybersecurity landscape.
7. Enterprise IAM Solutions: Managing Identities at Scale
Large organizations handle thousands of users accessing multiple systems daily, making identity management complex. Enterprise IAM solutions help businesses control access, enhance security, and ensure compliance. By adopting top IAM solutions, companies can prevent unauthorized access, protect sensitive data, and streamline authentication.
Challenges of Identity Management in Large Organizations
Enterprises face several challenges when managing identities:
- Complex access policies – Employees need different levels of access based on roles, departments, and locations.
- Multi-cloud and hybrid environments – Security risks increase when managing identities across cloud and on-premise systems.
- Regulatory compliance – Meeting standards like GDPR, HIPAA, and SOC 2 is essential for data protection and legal compliance.
- Insider threats and privileged access risks – Unauthorized use of high-level accounts can lead to security breaches.
Key Features of Enterprise IAM Solutions
To address these challenges, enterprise IAM solutions offer:
- Single Sign-On (SSO): Enables users to access multiple applications with one login.
- Multi-Factor Authentication (MFA): Enhances security by requiring additional verification beyond passwords.
- User provisioning and deprovisioning: Automates account creation and removal based on job roles.
- Role-Based Access Control (RBAC) & Attribute-Based Access Control (ABAC): Restricts access based on user responsibilities.
- Privileged Access Management (PAM): Protects critical accounts with additional security controls.
- Identity analytics & AI-driven threat detection: Identifies suspicious activity and potential security risks.
Enterprise IAM in Action
Many businesses have successfully implemented top IAM solutions to improve security and efficiency:
- A global bank reduced unauthorized access incidents by 40% by implementing SSO and MFA.
- A leading e-commerce company used cloud-based identity management systems to manage millions of secure customer logins.
- A hospital network adopted an enterprise IAM solution to restrict access to patient records, ensuring only authorized medical staff could view sensitive data.
By investing in enterprise IAM solutions, businesses can simplify identity management, strengthen security, and stay compliant. As organizations grow, having the right identity management systems is crucial for securing digital identities at scale.
8. Best IAM Solutions: Top Identity Management Systems for 2025
As cyber threats evolve, businesses need the best IAM solutions to secure their digital identities. Choosing the right identity management solutions ensures seamless authentication, strong access control, and compliance with industry regulations. In 2025, several top IAM solutions stand out for their security features, scalability, and integration capabilities.
Reviewing the Best IAM Providers
The leading IAM providers offer a range of features designed to meet the needs of businesses of all sizes. Some of the top IAM solutions in 2025 include:
- Okta: A cloud-based IAM platform known for its ease of integration and robust security.
- Microsoft Entra ID (formerly Azure AD): Ideal for enterprises using Microsoft services, offering deep integration with Office 365 and cloud applications.
- IBM Security Verify: AI-driven identity management solution with advanced analytics and risk-based authentication.
- Ping Identity: Strong in single sign-on (SSO) and multi-factor authentication (MFA) for enterprises with complex security needs.
- SailPoint: Specializes in identity governance and access management for large organizations.
Key Features Comparison
When evaluating the best IAM solutions, businesses should consider:
- Authentication methods: Support for MFA, SSO, and biometric authentication.
- User lifecycle management: Automated provisioning and deprovisioning for better access control.
- Integration capabilities: Compatibility with cloud services, SaaS applications, and on-premise systems.
- Compliance & security: Features like role-based access control (RBAC), audit logs, and regulatory compliance tools.
Pricing, Integrations, and Customization Options
IAM solutions vary in pricing based on features, user count, and deployment model:
- Subscription-based pricing: Most cloud-based IAM providers offer per-user, per-month pricing.
- Enterprise licensing: Large-scale businesses often require custom pricing based on specific security needs.
- Integration with existing IT infrastructure: The ability to connect with HR systems, CRM, and cybersecurity tools is essential for seamless identity management.
- Customization: Some providers offer tailored security policies, API access, and AI-driven access controls for businesses with complex security needs.
Choosing the Right IAM Solution
The best IAM solutions depend on a company’s size, security requirements, and IT environment. Businesses looking for scalability and ease of use may prefer cloud-based IAM solutions, while enterprises with strict security policies might opt for on-premise or hybrid IAM systems. By comparing features, pricing, and integrations, organizations can select the most suitable identity management solution for 2025.
9. IAM vs. PAM: Understanding the Difference
When securing digital identities and controlling access, organizations rely on both identity management solutions and access management solutions. Two critical components in this space are Identity and Access Management (IAM) and Privileged Access Management (PAM). While both play a role in securing user access, they serve different functions and are used in different scenarios.
How IAM and PAM Complement Each Other
- IAM manages access for all users within an organization, ensuring that employees, customers, and partners have the right level of access to systems and applications.
- PAM focuses specifically on securing privileged accounts—those with administrative or high-level access—to prevent unauthorized use and insider threats.
- Together, IAM and PAM work to enforce strong security policies by managing standard user access while providing additional layers of security for privileged accounts.
Differences in Security Functions and Policies
IAM applies to regular users, employees, and customers, granting them access to applications, databases, and cloud services. It uses authentication methods like Single Sign-On (SSO), Multi-Factor Authentication (MFA), and Role-Based Access Control (RBAC) to manage identities securely.
PAM is designed for administrators, IT staff, and other high-risk users who have access to critical systems. It enforces strict security controls, such as just-in-time access, session monitoring, and password vaulting, to minimize risks associated with privileged accounts.
IAM focuses on broad access control across an organization, ensuring compliance with regulations like GDPR, HIPAA, and SOC 2. PAM, in contrast, protects against insider threats and unauthorized privilege escalation by restricting access to sensitive resources.
When to Choose IAM vs. PAM
Organizations should implement IAM solutions when they need to manage access for employees, customers, and partners, ensuring secure authentication and authorization across various systems. PAM solutions are necessary when securing privileged accounts, preventing misuse of administrative credentials, and protecting sensitive data from insider threats.
In most cases, businesses need both identity management solutions and privileged access management to create a strong cybersecurity framework that controls all levels of user access.
10. How to Choose the Right IAM Solution for Your Business
Selecting the best identity management solutions is crucial for protecting digital assets, ensuring compliance, and streamlining user access. The right IAM solution should align with your business’s security needs, IT infrastructure, and scalability requirements.
Factors to Consider When Choosing an IAM Solution
- Security & Compliance: Ensure the identity solution supports Multi-Factor Authentication (MFA), Role-Based Access Control (RBAC), and encryption to protect user identities. Compliance with industry standards like GDPR, HIPAA, and SOC 2 is also essential.
- Scalability: The IAM system should grow with your business, handling increasing users, cloud expansion, and remote work environments.
- Integration Capabilities: A strong IAM solution should integrate seamlessly with cloud platforms, enterprise applications, HR systems, and cybersecurity tools.
- User Experience: Features like Single Sign-On (SSO) and adaptive authentication improve convenience while maintaining security.
- Deployment Model: Decide between cloud-based, on-premises, or hybrid IAM solutions based on your IT environment and security policies.
Questions to Ask Before Selecting an IAM Solution
- Does the IAM provider support MFA, SSO, and passwordless authentication?
- How well does it integrate with existing IT infrastructure, SaaS applications, and cloud services?
- Can it handle role-based and attribute-based access controls for different departments and user groups?
- What kind of reporting and audit logs does it provide for compliance and security monitoring?
- Does the vendor offer customization options to fit specific business needs?
- What is the cost structure—is it based on users, features, or deployment model?
Industry-Specific IAM Needs
Different industries have unique identity management challenges:
- Finance & Banking: Requires strong identity verification, fraud detection, and regulatory compliance features.
- Healthcare: Needs strict access control to protect electronic health records (EHRs) while ensuring HIPAA compliance.
- E-Commerce & Retail: Prioritizes customer identity management with seamless authentication for online shoppers.
- Manufacturing & Enterprises: Focuses on privileged access management (PAM) to protect critical infrastructure and industrial systems.
Choosing the best identity management solutions depends on a company’s security priorities, scalability needs, and compliance requirements. By evaluating key features, integrations, and industry-specific needs, businesses can implement an IAM solution that enhances security while improving user access management.
11. Implementing IAM: Step-by-Step Guide
Deploying identity and access management solutions requires a strategic approach to ensure security, efficiency, and seamless integration with existing systems.
Step-by-Step IAM Implementation
- Define Business Needs & Security Goals: Identify the key security challenges, user access requirements, and compliance needs.
- Choose the Right IAM Solution: Decide between cloud IAM solutions, on-premise, or hybrid based on scalability and security priorities.
- Integrate IAM with Existing IT Infrastructure: Ensure smooth connectivity with HR systems, cloud applications, and legacy databases.
- Set Up Authentication & Access Controls: Implement Multi-Factor Authentication (MFA), Role-Based Access Control (RBAC), and Single Sign-On (SSO) for secure access.
- Monitor & Manage Identities: Regularly update user permissions, audit access logs, and enforce governance policies.
Common Challenges & How to Overcome Them
- User resistance to new authentication methods: Provide training and awareness programs.
- Complex integration with legacy systems: Use APIs and middleware for smoother transitions.
- IAM scalability issues: Choose cloud IAM solutions for flexibility and future expansion.
12. The Future of IAM: Trends and Emerging Technologies
As cybersecurity threats evolve, identity solutions continue to integrate advanced technologies for enhanced security and usability.
Key IAM Trends to Watch
- AI and Machine Learning in IAM: Automates risk detection, anomaly identification, and adaptive authentication.
- Zero Trust Security and IAM: Ensures continuous authentication, requiring verification at every access point.
- Decentralized Identity & Blockchain-Based IAM: Uses blockchain for tamper-proof identity verification, reducing reliance on centralized databases.
Businesses must stay ahead by adopting innovative identity management solutions that offer real-time security enhancements and intelligent access controls.
13. IAM Compliance: Meeting Regulatory Standards
Organizations must align identity access management solutions with global compliance requirements to avoid penalties and security risks.
Key IAM Compliance Standards
- GDPR & CCPA: Protects user data and mandates strict access controls.
- HIPAA & SOX: Ensures identity verification and audit trails for healthcare and financial industries.
How IAM Helps in Compliance
- Automated reporting & auditing for regulatory documentation.
- Enforcing least-privilege access policies to prevent unauthorized data access.
- Real-time monitoring & alerts for compliance violations.
Implementing enterprise IAM solutions ensures businesses remain compliant while strengthening security frameworks.
14. IAM Security Best Practices: Avoiding Common Mistakes
To maximize the effectiveness of identity management systems, organizations must adopt strong security practices.
Essential IAM Best Practices
- Passwordless Authentication & Biometric Security: Reduces phishing risks and improves user experience.
- Preventing Identity Theft with IAM: Implement AI-driven fraud detection and behavior analytics.
- IAM Governance & Risk Management: Some of the best identity management solutions are regular security audits, role-based access policies, and continuous monitoring.
Choosing cloud-based IAM solutions with automated security updates helps businesses stay protected against evolving cyber threats.
15. Conclusion & Final Thoughts on IAM Solutions
The role of top IAM solutions in cybersecurity has never been more crucial. As businesses navigate an increasingly digital landscape, investing in the best IAM solutions is essential for securing digital identities, preventing data breaches, and ensuring compliance with regulatory standards. With the rise of Zero Trust security, AI-driven authentication, and decentralized identity, the future of IAM is rapidly evolving to provide more intelligent and adaptive security measures. Selecting the right identity management solution depends on factors like business size, security requirements, and integration capabilities. By implementing a robust IAM framework, organizations can strengthen access controls, enhance user experience, and protect sensitive data in an ever-connected world.