The Dangers of Manual User Access Reviews & How to Overcome Them [Webinar Recap & Full Guide]
The Dangers of Manual User Access Reviews & How to Overcome Them [Webinar Recap & Full Guide]

Today’s ever-evolving cybersecurity and compliance landscape causes organizations to face constant challenges in protecting sensitive data and ensuring regulatory compliance.
Among the critical tasks for maintaining a robust security posture is managing user access to systems and data. While user access reviews are essential, relying on manual processes can introduce significant risks and inefficiencies.
In this article, we’ll explore the dangers associated with manual user access reviews and provide actionable strategies to overcome them — by embracing automated user access reviews, you can enhance security, streamline compliance efforts, and mitigate potential risks.
But before we get into that, let’s first take a look at the most prominent issues CISOs are concerned about and how UARs are involved.

Today’s Cybersecurity Landscape & Top Concerns of CISOs
In today’s dynamic cybersecurity and compliance landscape, Chief Information Security Officers (CISOs) face a myriad of challenges. Let’s delve into some of the most important ones:
- 👉 Network Visibility: CISOs are increasingly concerned about maintaining comprehensive network visibility. With the proliferation of endpoints, including Internet of Things (IoT) devices and remote workforce, it becomes challenging to monitor and secure the entire network infrastructure. Lack of visibility can leave blind spots for potential threats and vulnerabilities, making it difficult to implement effective security measures.
- 👉 Avoiding New Risks as the Number of Apps Grows: The number of applications within organizations continues to grow rapidly. CISOs are concerned about the risks associated with deploying and managing multiple applications. Each new application introduces potential security vulnerabilities and attack vectors. CISOs must ensure proper security measures are in place and that applications are regularly updated and patched to mitigate risks.
- 👉 Reducing Stress on Security Teams: CISOs are mindful of the stress placed on their security teams. The ever-evolving threat landscape and the need to manage a multitude of security tools and technologies can overwhelm security professionals. CISOs seek ways to reduce stress and optimize their team’s efficiency, such as through automation, collaboration tools, and prioritization of critical tasks.
- 👉 Compliance vs. Security: While compliance frameworks provide guidelines, they may not always align with the latest security best practices. CISOs must navigate this delicate balance, ensuring that compliance is achieved without compromising the organization’s overall security stance.
- 👉 Skyrocketing Enterprise Application Counts: Organizations are adopting an increasing number of enterprise applications to support their business operations. Each application brings its own security considerations, ranging from access controls to data protection. CISOs must manage the security risks associated with this expanding application landscape, including ensuring secure configurations, conducting regular assessments, and maintaining strong access controls.
- 👉 SaaS Applications as the Fastest Growing Category: Software-as-a-Service (SaaS) applications offer numerous benefits, such as scalability and flexibility. However, the rapid adoption of SaaS applications poses unique challenges for CISOs. They need to ensure that these applications are properly integrated into the security framework, align with compliance requirements, and have robust security controls in place.
So, what role do user access reviews play in all this? All the points above have one thing in common — they start with identity and revolve around who has access to what in an organization.

Now, let’s define user access reviews and clarify their part in identity management.
What are User Access Reviews?
User access reviews, also known as user access certifications or entitlement reviews, are systematic processes that organizations use to evaluate and validate user access rights and permissions to systems, applications, data, and resources within their IT environment.
The primary purpose of user access reviews is to ensure that users have appropriate and necessary access privileges aligned with their roles and responsibilities.
By conducting access reviews, organizations can assess and validate the access rights of individuals, detect and remediate any excessive or inappropriate access, and maintain a strong security posture.
What Manual UARs Look Like
The manual user access review process typically involves several steps, which may vary slightly depending on the organization’s specific procedures and policies. Here is a general overview of the manual user access review process:
- 1️⃣ Preparation: The process begins with identifying the scope and objectives of the access review. This includes determining which systems, applications, and data repositories will be included in the review. The review period is established, and the individuals or roles responsible for conducting the review are designated.
- 2️⃣ User Access Data Collection: The next step is gathering the necessary data related to user access rights and permissions. This data includes user account information, roles and responsibilities, system/application access privileges, and any associated entitlements. The data can be obtained from user directories, access control lists, or identity management systems.
- 3️⃣ Review Analysis: The IT administrators responsible for conducting the access review analyze the collected data. They compare the access rights of individual users with their assigned roles and responsibilities. The goal is to identify any discrepancies, such as excessive privileges or unauthorized access, by comparing the actual access levels with the defined access requirements.
- 4️⃣ User Verification: Once discrepancies are identified, the IT administrators reach out to the appropriate managers or data owners to verify the access rights of individual users. This step ensures that access privileges are aligned with the users’ job functions and responsibilities. Managers provide input and confirm or adjust the access rights as necessary.
- 5️⃣ Documentation: Throughout the review process, all findings, decisions, and actions taken are documented. This includes any adjustments made to user access rights, as well as the rationale behind those changes. Documentation is crucial for audit purposes, compliance reporting, and maintaining an audit trail of the review process.
- 6️⃣ Remediation and Follow-up: If any issues or concerns are identified during the review, the IT administrators work with the relevant stakeholders to address them. This may involve revoking excessive privileges, updating access controls, or providing additional training to users. Remediation activities are tracked and followed up to ensure that appropriate actions are taken.
- 7️⃣ Review Completion: Once all discrepancies have been addressed and access rights have been verified and adjusted, the review process is considered complete. The final documentation is prepared, summarizing the outcomes of the review, any changes made, and the overall results.

It’s important to note that the manual user access review process can be time-consuming, resource-intensive, and prone to human error. Organizations that rely solely on manual processes often face challenges in conducting reviews for a large number of users and systems.
Problems with Manual UARs
Manual user access reviews present several challenges and drawbacks that can hinder an organization’s security and compliance efforts. Some of the key problems associated with manual user access reviews include:
- ❌ Human Error: Manual processes are susceptible to human error. IT administrators responsible for reviewing access rights can make mistakes or overlook critical permissions. These errors can result in granting excessive privileges or missing unauthorized access, leading to potential security breaches or compromised system integrity.
- ❌ Inefficiency and Time Constraints: Manual user access reviews are time-consuming and resource-intensive. Reviewing access rights for a large number of users and systems can take weeks or even months. This delay can lead to delayed access provisioning, impacting employee productivity, and administrative overhead. Moreover, manual processes may not scale well with growing organizations and evolving access requirements.
- ❌ Incomplete Reviews: Manual user access reviews may overlook certain access rights or fail to consider the complete picture. Complex IT environments, changing user roles, and dynamic access requirements make it challenging to ensure comprehensive and accurate reviews. Incomplete reviews can leave security gaps and regulatory compliance vulnerabilities.
- ❌ Lack of Real-Time Visibility: Manual processes often lack real-time visibility into access rights and changes. As a result, organizations may not be promptly aware of unauthorized access attempts or changes in user privileges. This delay in detecting and responding to access issues can increase the risk of data breaches or unauthorized activities.
- ❌ Compliance Risks: Manual user access reviews may struggle to meet compliance requirements effectively. Regulations such as the General Data Protection Regulation (GDPR), Health Insurance Portability and Accountability Act (HIPAA), and Payment Card Industry Data Security Standard (PCI DSS) require organizations to regularly review and validate access rights. Manual processes may fall short in providing the necessary documentation, evidence, and consistency required for compliance audits.
- ❌ Lack of Audit Trail: Manual processes often lack a comprehensive and easily accessible audit trail. This makes it challenging to demonstrate accountability, track changes, and provide evidence of access reviews. An audit trail is crucial for compliance reporting, regulatory audits, and investigations into security incidents or breaches.
- ❌ Difficulty in Keeping Pace with Changes: IT environments are dynamic, with users changing roles, joining or leaving the organization, and systems being updated or decommissioned. Manual user access reviews struggle to keep up with these changes efficiently. Consequently, organizations may have users with outdated access rights or fail to promptly revoke access for users who no longer require it.
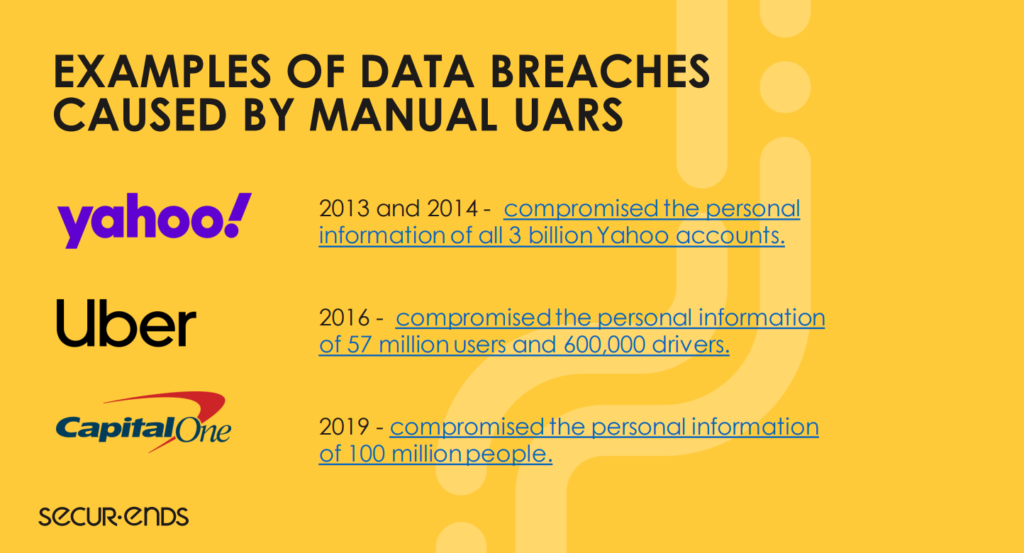
To overcome these challenges and enhance the effectiveness of user access reviews, organizations are increasingly turning to automated solutions.
Automated user access reviews leverage technology such as identity and access management (IAM) systems, analytics, and machine learning to streamline the process, improve accuracy, and provide real-time visibility into access rights and changes.
Benefits & Advantages of Automating UARs
Automated user access reviews offer numerous benefits and advantages over manual processes. By leveraging technology and advanced capabilities, automated solutions enhance the efficiency, accuracy, and effectiveness of user access reviews. Here are some key benefits of automated user access reviews:
- ✅ Increased Efficiency: Automation streamlines the user access review process, reducing the time and effort required to review access rights. It eliminates manual tasks such as data collection, analysis, and documentation, allowing IT administrators to focus on higher-value activities. This increased efficiency enables organizations to conduct reviews more frequently, even for large user populations and complex IT environments.
- ✅ Enhanced Accuracy and Consistency: Automated user access reviews significantly reduce the risk of human error. By leveraging predefined rules and algorithms, automated solutions can accurately identify discrepancies, unauthorized access, and excessive privileges. This improves the accuracy and consistency of access reviews, ensuring that access rights align with roles and responsibilities consistently across the organization.
- ✅ Real-time Visibility and Monitoring: Automated solutions provide real-time visibility into user access rights and changes. They continuously monitor access privileges and promptly notify administrators of any unauthorized or suspicious activities. Real-time visibility enables organizations to detect and respond to access issues in a timely manner, reducing the risk of data breaches and unauthorized access.
- ✅ Scalability and Flexibility: Automated user access reviews can scale effortlessly to handle large user populations and dynamic IT environments. As organizations grow and evolve, automated solutions can adapt to changing access requirements, new systems, and user roles. They can handle a vast number of access entitlements and systems, ensuring comprehensive and accurate reviews.
- ✅ Compliance and Audit Readiness: Automated user access reviews facilitate compliance with regulatory requirements. They generate detailed reports and audit trails, documenting the review process, access changes, and user entitlements. These reports serve as evidence for compliance audits and regulatory inquiries, simplifying the process and reducing the administrative burden associated with compliance reporting.
- ✅ Proactive Risk Management: Automated solutions help organizations proactively manage access-related risks. By continuously monitoring access rights and activities, they can identify and mitigate potential security vulnerabilities and unauthorized access attempts. Automated alerts and notifications enable organizations to take immediate action to address access issues and strengthen their security posture.
- ✅ Improved Productivity and Resource Allocation: With automation handling the repetitive and time-consuming tasks, IT administrators can focus on higher-value activities such as analyzing access patterns, conducting risk assessments, and implementing security controls. This improves productivity, optimizes resource allocation, and allows IT teams to devote their time and expertise to critical security initiatives.
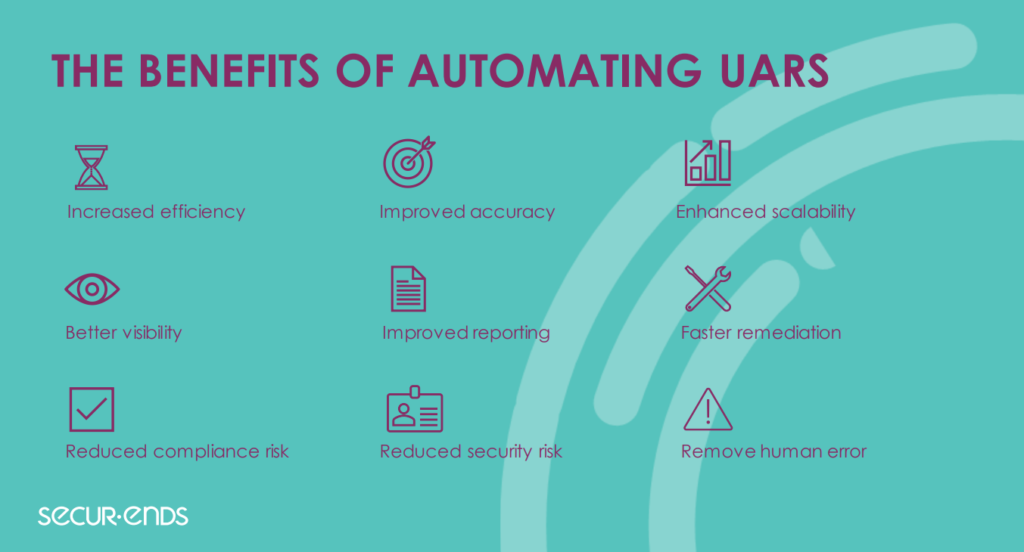
Leveraging automation enables your organization to enhance your access governance, strengthen your security posture, and achieve greater operational efficiency.
10 Steps to Implementing Automated UARs
Implementing automated user access reviews involves a series of key steps to ensure a successful deployment. Here’s what to consider before starting this process:
Step 1 – Assess Your Requirements
Start by assessing your organization’s specific requirements and objectives for implementing automated user access reviews. Identify the systems, applications, and data repositories that need to be included in the review process. Determine the frequency of reviews, compliance requirements, and any specific access governance needs unique to your organization.
Step 2 – Select the Right Solution
Research and evaluate different automated user access review solutions available in the market. Consider factors such as scalability, integration capabilities, reporting and analytics features, ease of use, and compatibility with your existing IT infrastructure. Select a solution that aligns with your requirements and provides the necessary functionality to automate the user access review process effectively.
Step 3 – Define Review Policies and Rules
Establish clear review policies, rules, and criteria for evaluating user access rights. Define the roles and responsibilities of individuals involved in the review process, including IT administrators, managers, and data owners. Determine the access entitlements that should be reviewed, the frequency of reviews, and the process for handling exceptions or mitigating risks identified during the reviews.
Step 4 – Integrate with Identity and Access Management (IAM) Systems
Integrate the automated user access review solution with your organization’s Identity and Access Management (IAM) systems, if applicable. This integration allows for seamless data synchronization and access rights validation. It ensures that user access information is up to date, and any changes in user roles or permissions are reflected in the automated review process.
Step 5 – Data Collection and Analysis
Configure the automated solution to collect user access data from relevant systems and applications. This includes gathering information such as user accounts, roles, entitlements, and access permissions. The solution should analyze the collected data, compare it against defined policies and rules, and identify any discrepancies or access violations.
Step 6 – Define Review Workflows
Define and configure review workflows within the automated solution. This includes setting up review cycles, assigning reviewers and approvers, and establishing the sequence and steps involved in the review process. Define how exceptions or issues identified during the review are escalated, addressed, and remediated.
Step 7 – Automate Review Notifications and Reminders
Configure automated notifications and reminders to notify users and reviewers about upcoming or pending reviews. The solution should send reminders to users to validate their access rights and provide timely notifications to reviewers about pending review tasks. This ensures that the review process progresses smoothly and within the defined timeline.
Step 8 – Generate Reports and Audit Trails
Implement reporting capabilities within the automated solution to generate comprehensive reports and audit trails. These reports should capture the review process, access changes, remediation actions, and any exceptions or risks identified during the review. Audit trails serve as evidence for compliance audits and help track the history of access reviews.
Step 9 – Conduct Training and User Awareness
Provide training and awareness programs to users, managers, and reviewers on the automated user access review process. Ensure they understand the purpose, benefits, and their respective roles in the review process. Train them on using the automated solution effectively and how to address any access-related issues or exceptions identified during the review.
Step 10 – Monitor and Improve
Continuously monitor the effectiveness of the automated user access review process. Regularly evaluate the outcomes, review metrics, and user feedback to identify areas for improvement. Make necessary adjustments to policies, workflows, and configurations to optimize the process and enhance its efficiency over time.
Follow the points above to successfully implement automated user access reviews at your organization, improving efficiency, accuracy, and compliance while strengthening your overall access governance practices.
Leave the Spreadsheets and Phone Calls Behind — Get Started with Automating Your UARs Today
In today’s fast-paced and complex digital landscape, manual user access reviews are no longer sufficient and pose significant risks.
The potential for human error, inefficiency, incomplete reviews, and compliance gaps can have severe consequences, including security breaches, data leaks, and regulatory penalties. However, by leveraging automation, you can overcome these dangers and enhance your access governance practices.
SecurEnds can assist your organization in overcoming the dangers of manual user access reviews. Through our automation platform, you can strengthen your security posture, improve compliance, and mitigate the risks associated with access management.
Ready to see SecurEnds in action? Schedule your personalized demo now.
Article by Bob Pruett ✍