What is Identity Governance and Administration (IGA)?
What is Identity Governance and Administration (IGA)?
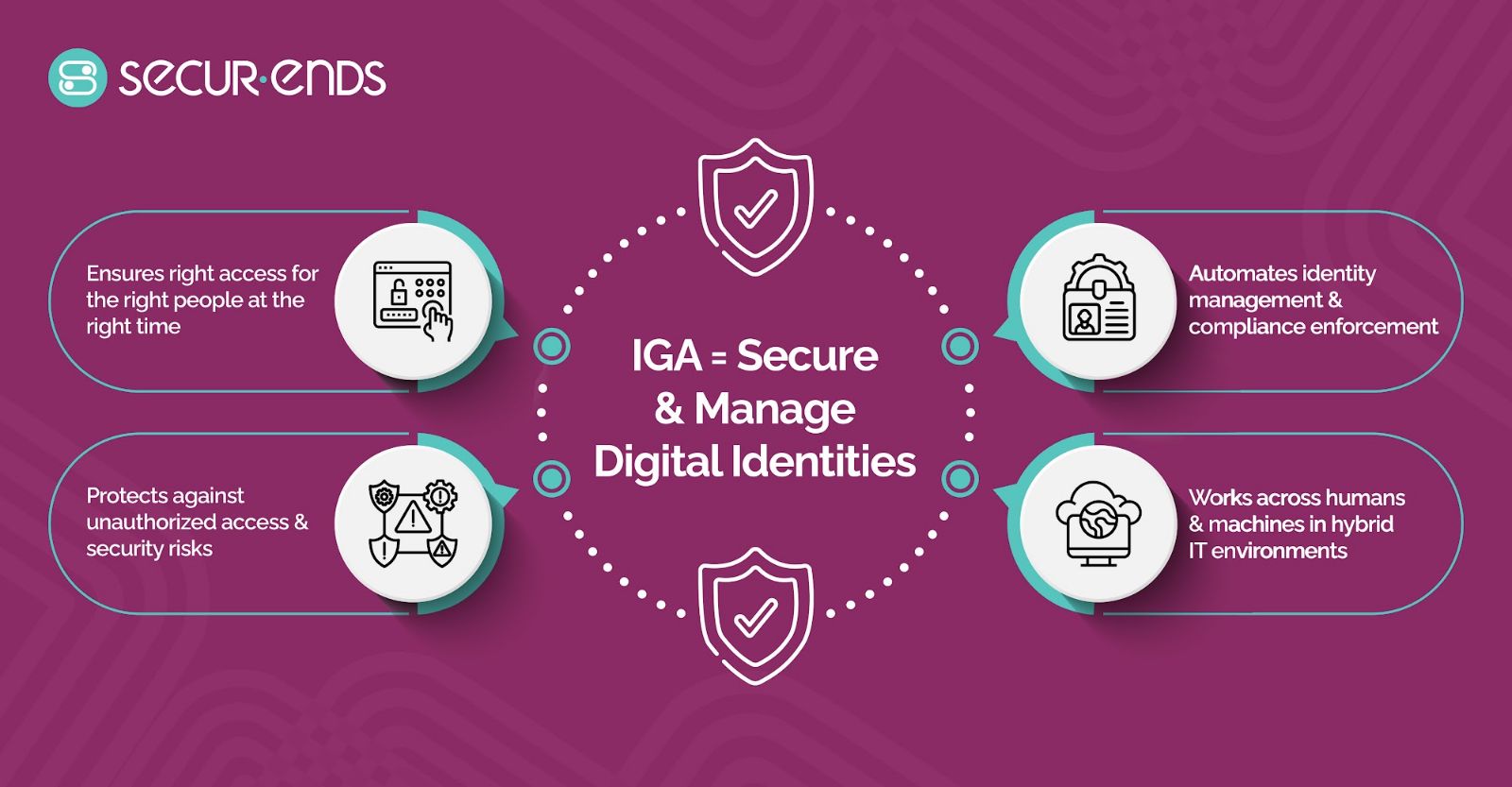
Identity Governance and Administration (IGA), also referred to as identity governance, is a cornerstone of modern cybersecurity. But what is IGA in cybersecurity, and why does it matter?
At its core, IGA is a system that governs and secures digital identities—both human and machine—within an organization. It ensures the right individuals have appropriate access to resources by enforcing policies, automating processes, and mitigating risks.
When comparing identity governance vs identity management, the distinction becomes clear: identity management focuses on provisioning and authenticating users, while IGA goes further, providing oversight, compliance, and policy enforcement.
In today’s hybrid IT environments, IGA streamlines critical processes like onboarding, access reviews, and lifecycle management while ensuring regulatory compliance. Its role in reducing security vulnerabilities and maintaining accountability makes IGA indispensable for organizations navigating the complexities of modern cybersecurity.
2. Why Your Organization Needs IGA Services

In the digital-first landscape of 2025, managing identities and access efficiently is no longer optional—it’s a necessity for businesses aiming to safeguard their operations, meet regulatory requirements, and maintain seamless workflows.
Identity and Governance Administration (IGA) services provide the essential framework to address these needs while tackling key IGA challenges that businesses face without proper identity management systems.
Top Challenges Businesses Face Without Proper IGA
Without an effective IGA solution, organizations often struggle with:
- Increased Security Risks: Weak or stolen credentials, orphaned accounts, and overprovisioning leave businesses vulnerable to cyberattacks.
- Compliance Failures: Adhering to regulations like GDPR, HIPAA, and HITRUST compliance becomes complex without centralized controls, exposing companies to legal risks and fines.
- Operational Inefficiencies: Labor-intensive processes, such as access certifications, manual access provisioning and deprovisioning, burden IT teams and hinder productivity.
- Audit Fatigue: Lack of streamlined workflows and reporting tools can make audits time-consuming and error-prone.
How IGA Improves Security Posture and Ensures Compliance
Modern IGA tools empower organizations to effectively manage access and mitigate risks:
- Enhanced Security: By implementing the principle of least privilege while setting up roles and enabling real-time visibility into “who has access to what,” IGA prevents unauthorized access and identifies risky activities.
- Regulatory Compliance: IGA automates evidence gathering required to meet regulations such as SOX, SOC, GLBA, GDPR and HIPAA, with role-based access management and comprehensive reporting tools ensuring continuous compliance and addressing compliance benefits.
- Zero Trust Alignment: Modern IGA tools integrate with Zero Trust security models, creating a robust foundation to safeguard identities across human and machine environments.
Business Benefits of IGA Services
The impact of IGA extends beyond security, offering tangible operational and cost benefits:
- Reduced Audit Fatigue: Automated workflows and clear reporting make audits seamless, with less reliance on manual efforts.
- Streamlined Operations: Automating repetitive tasks like access requests and provisioning saves time, allowing IT teams to focus on strategic initiatives.
- Cost Efficiency: Eliminating errors caused by manual processes and reducing operational overhead translates into significant cost savings.
With IGA, organizations can transform their approach to identity management, enabling secure, compliant, and efficient operations.
By addressing IGA challenges proactively, businesses can focus on growth and innovation without compromising security or compliance.
3. Key Features of a Robust IGA Solution
A modern IGA solution is equipped with essential features that streamline access management, improve security, and ensure compliance. These capabilities not only address today’s business challenges but also enable seamless integration with existing systems, effectively modernizing legacy IAM solutions.
Here are the key features that make a robust IGA platform indispensable for any organization:
Entitlement Management for Precise Access Control
- Automated Identity Lifecycle Management: Simplifies processes such as onboarding, offboarding, and managing access rights (entitlement management). This ensures that users only have the access they need, reducing security risks associated with overprovisioned permissions.
- Access Discovery Functionality: Automatically identifies and tracks user accounts and entitlements across hybrid IT environments, ensuring no unauthorized access is overlooked.
- Self-Service Capabilities: Empowers users to request access on demand with minimal IT intervention, streamlining workflows and improving user experience without compromising security.
Role-Based Access Control (RBAC) for Scalable Security
- Centralized Role Management: Role-Based Access Control (RBAC) ensures that permissions are assigned based on roles, providing consistency and reducing manual errors. This makes scaling security effortless as organizations grow and their workforce evolves.
- HR System Integrations: By integrating with HR systems, RBAC allows automated role assignments and updates, reducing human errors and ensuring that only the right people have access to the right resources.
- Policy Enforcement: With RBAC, organizations can enforce security policies, ensuring access privileges align with business requirements and compliance standards.
Automation for User Access Reviews and Compliance Tracking
- User Access Reviews: Automates periodic access certification, enabling administrators to regularly review and update access privileges across systems. This ensures continuous compliance with internal policies and external regulations.
- Automated Workflows: Automatically routes access requests for approval and manages entitlements with pre-configured workflows, saving time and enhancing efficiency.
- Comprehensive Analytics and Reporting: Provides real-time reporting and auditing capabilities, making it easier to demonstrate compliance with regulations such as GDPR, HIPAA, and HITRUST.
Modernizing Legacy IAM Solutions
- Automate Legacy IAM Solutions: A robust IGA platform can help organizations automate legacy IAM solutions, replacing manual processes and outdated systems that hinder efficiency.
- Seamless Integration with SaaS and Cloud Solutions: Built-in integrations and plug-ins support modern IT environments, making it easier to manage identities and access across both on-premise and cloud-based systems.
- Reduced Complexity: By consolidating IAM tasks into a single, user-friendly platform, IGAs eliminate the need for multiple, disconnected solutions, simplifying management and improving security.
By leveraging these features, a modern IGA solution can enhance entitlement management, streamline user access reviews, and effectively automate legacy IAM solutions, providing a scalable and secure framework for managing user identities and access rights across the organization.
4. How SecurEnds Delivers Excellence in IGA
SecurEnds offers cutting-edge IGA automation tools designed to meet the evolving access management and compliance needs of modern organizations.
Leveraging seamless integrations and advanced features, SecurEnds IGA solutions ensure that enterprises can implement comprehensive and automated identity governance across all applications.
Here’s how SecurEnds excels in delivering superior identity governance tools:
Overview of SecurEnds Solutions
SecurEnds offers advanced Identity Governance solutions that empower organizations to manage user access efficiently, ensure regulatory compliance, and enhance security. Built for both cloud and on-premise environments, SecurEnds IGA solutions leverage the latest technology for faster implementation and seamless adoption.
SecurEnds Okta Governance
SecurEnds enhances Okta’s identity management capabilities by providing:
- Automated Access Certifications and Entitlement Reviews for both Okta-enabled and custom applications.
- Approval Workflows and Grouping for better access control within Okta-enabled applications.
- Self-Service Access Requests for non-Okta-enabled applications, improving user autonomy and efficiency.
With these capabilities, SecurEnds Okta Governance delivers a modern Identity Governance solution that meets the evolving needs of Okta customers, offering a comprehensive approach to managing access and compliance.
SecurEnds Workday Integration
SecurEnds significantly enhances Workday environments by enabling:
- Comprehensive Access Certifications and Periodic User Access Reviews, ensuring compliance with SOX, HIPAA, and FISMA.
- Granular Access Controls to protect sensitive data and ensure only authorized personnel have access.
- Automated Compliance Processes, reducing manual efforts while strengthening security oversight.
By integrating seamlessly with Workday, SecurEnds IGA solutions provide organizations with enhanced visibility, control, and regulatory assurance for identity governance.
SecurEnds ServiceNow Integration
The SecurEnds CEM module, with its native ServiceNow integration, offers:
- User Access Reviews for SOX & HIPAA compliance directly within ServiceNow.
- Automated Joiner-Mover-Leaver Processes for streamlined access requests and lifecycle management.
- A Centralized Identity Repository, allowing organizations to connect with multiple cloud and on-premise applications beyond ServiceNow.
Unlike basic workflow-based solutions, SecurEnds IGA solutions augment ServiceNow ITSM by providing full-featured identity governance tools, ensuring governance across ServiceNow and all connected applications.
With its advanced automation, scalability, and easy integrations, SecurEnds IGA solutions enable organizations to maintain robust security, compliance, and governance—without excessive complexity or cost.
Key Features of SecurEnds Tools
SecurEnds stands out for its powerful automation, scalability, and seamless integrations with leading platforms. Key features include:
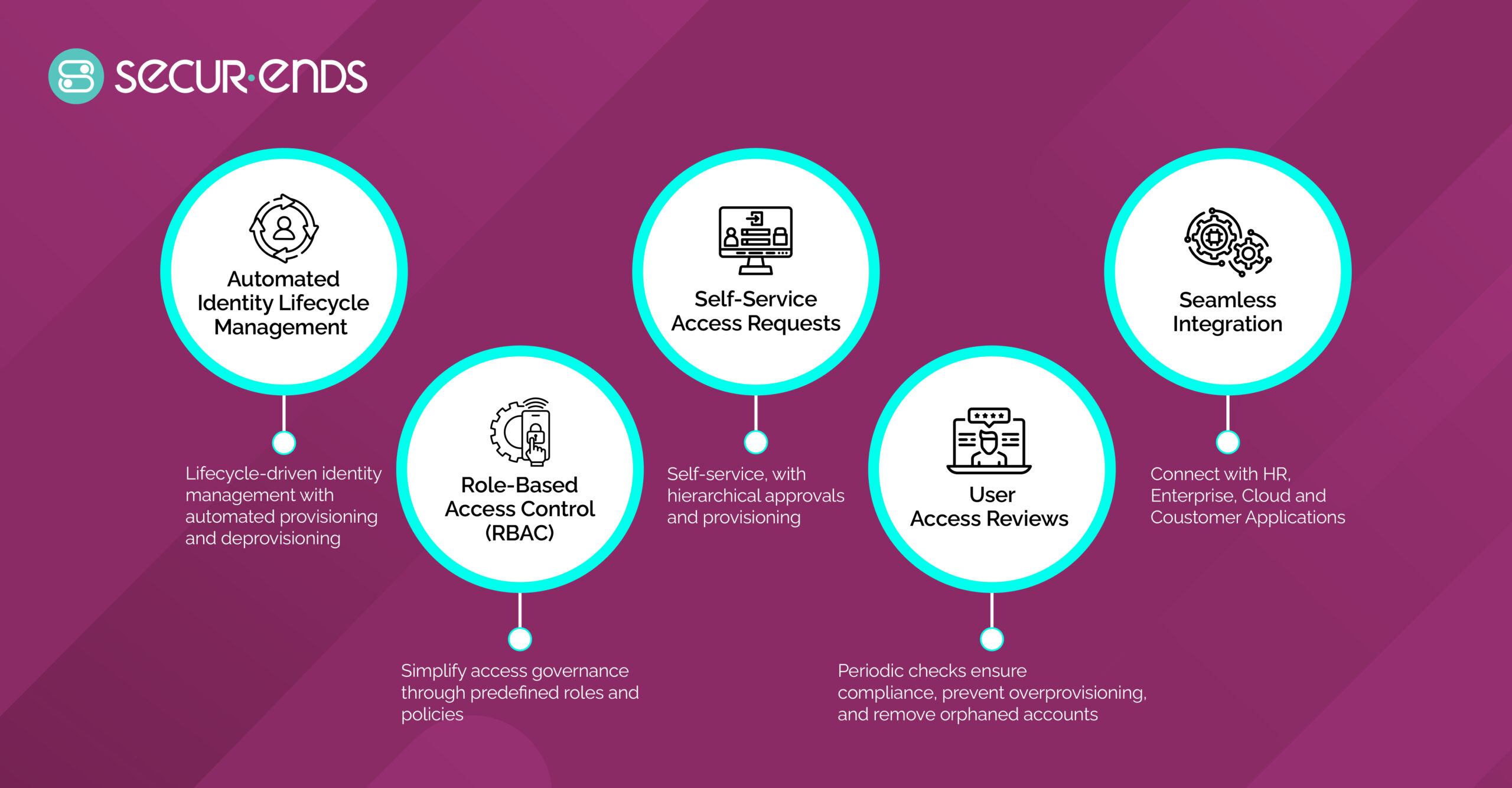
Comprehensive Identity Lifecycle Management (ILM) & Automation
Automate and streamline identity management across your enterprise. From onboarding to offboarding, SecurEnds IGA solutions ensure the right people have the right access at the right time, reducing manual effort and human errors.
Advanced Access Certification for Compliance
Automate access reviews and certifications to minimize security risks. SecurEnds IGA solutions ensure continuous compliance with regulatory standards and provide easy audit access across all systems and applications.
Seamless & Easy Integration
Integrate effortlessly with your existing IT infrastructure, including cloud and on-premise applications. SecurEnds IGA solutions support a wide range of platforms, unifying identity management and governance across your organization.
Intelligent Risk Management
Leverage advanced analytics to proactively identify and mitigate identity-related risks. SecurEnds IGA solutions provide actionable insights to strengthen your security posture.
User-Friendly & Scalable Solution
Designed for ease of use, SecurEnds IGA solutions simplify identity and access management with an intuitive interface. Whether for a growing startup or a large enterprise, its scalable architecture adapts to your evolving needs.
Success Stories: Real-World Examples
Many organizations across various sectors have successfully implemented SecurEnds IGA solutions to enhance their identity governance capabilities and improve security posture. From reducing the manual workload in access reviews to optimizing onboarding processes through Workday integration, SecurEnds IGA solutions have delivered measurable improvements in governance and compliance. Here are some notable success stories:
- A large financial institution leveraged SecurEnds Okta Governance to automate access certifications across thousands of users, improving security and compliance while reducing operational overhead.
- A global healthcare provider used the SecurEnds IGA solutions with Workday integration to streamline its employee onboarding process, ensuring full compliance with industry regulations like HIPAA while enhancing data security.
5. Best Practices for Implementing Identity Governance
Implementing Identity Governance and Administration (IGA) is essential for organizations looking to enhance security, streamline access management, and mitigate identity-related risks.
A well-structured IGA framework ensures that the right individuals have appropriate access to resources while maintaining compliance with regulatory requirements.
Below are the best practices for IGA implementation.
Steps to Establish a Strong IGA Framework
1. Assess Organizational Needs and Existing Infrastructure
Begin by evaluating the current identity management system. Identify gaps in security, analyze user access patterns, and assess compliance requirements. This thorough assessment will guide you in applying effective IGA implementation tips to create a tailored strategy.
2. Establish a Cross-Departmental Implementation Team
IGA is not solely an IT responsibility. Engage stakeholders from HR, compliance, security, and operations to align governance policies with business objectives and user workflows.
3. Define Access Roles Based on Job Functions
Implement role-based access control (RBAC) to ensure users have only the necessary permissions. Collaborate with HR to map job functions to appropriate access levels, minimizing entitlement creep and unauthorized access.
4. Integrate IGA with Existing IT Systems
Ensure your IGA solution seamlessly integrates with IAM platforms, cloud services, and enterprise applications. A well-integrated system improves operational efficiency and enables real-time monitoring of user access.
5. Regularly Review User Access and Prevent Entitlement Creep
Conduct periodic access reviews to identify and remove unnecessary permissions. Automate these reviews where possible to enhance accuracy and efficiency. Implement strong governance policies to manage role changes and terminations effectively.
Best Practices for IGA Implementation
1. Secure Leadership Buy-In
A top-down approach ensures IGA receives the necessary resources and attention. Involve executive leadership to drive commitment and adherence to governance policies.
2. Conduct Employee Training and Awareness Programs
Educate employees on IAM risk management, access management best practices, security risks, and compliance obligations. Regular training enhances awareness and reduces security vulnerabilities.
3. Establish a Feedback Loop for Continuous Improvement
Encourage ongoing feedback from employees and stakeholders. Regularly refine IGA policies based on evolving organizational needs and emerging security threats.
A strong IGA framework enhances security, compliance, and operational efficiency. By regularly reviewing user access, preventing entitlement creep, and integrating IGA with existing IT systems, organizations can successfully implement IGA best practices while ensuring long-term sustainability.
6. Industry-Specific Use Cases for IGA
Identity Governance and Administration (IGA) plays a crucial role in ensuring security, compliance, and access management across various industries. Below are sector-specific applications of IGA:
IGA for Financial Institutions: Meeting Regulatory Requirements like SOX and PCI
Financial institutions operate under stringent regulations such as the Sarbanes-Oxley Act (SOX) and the Payment Card Industry Data Security Standard (PCI DSS).
Implementing a financial institution solution with IGA helps organizations:
- Ensure Compliance: Automate access controls and maintain detailed audit trails to meet regulatory mandates.
- Enhance Security: Enforce strict access policies to protect sensitive financial data from unauthorized access.
- Streamline Audits: Simplify the process of demonstrating compliance through comprehensive reporting and analytics.
By leveraging IGA, banks, investment firms, and credit union solutions can efficiently manage user identities and access privileges, reducing the risk of breaches and regulatory penalties.
IGA in Healthcare: Ensuring HIPAA and HITRUST Compliance
The healthcare sector must comply with regulations like the Health Insurance Portability and Accountability Act (HIPAA) and HITRUST standards to safeguard patient information.
Implementing IAM for healthcare organizations enables:
- Protecting Patient Data: Implementing role-based access controls to ensure that only authorized personnel can access sensitive health information.
- Maintaining Compliance: Providing automated workflows and audit capabilities to adhere to regulatory requirements.
- Reducing Risk: Identifying and mitigating inappropriate access privileges through continuous monitoring and AI-driven analytics.
Adopting IGA in healthcare settings enhances data security and ensures compliance with industry regulations, thereby maintaining patient trust.
IGA for SMBs: Cost-Effective Solutions Tailored for Smaller Organizations
Small and medium-sized businesses (SMBs) often face the same security and compliance challenges as larger enterprises but with limited resources.
An IGA financial institution solution tailored for SMBs offers:
- Automate Access Management: Reduce manual efforts by automating user provisioning and deprovisioning, ensuring employees have appropriate access.
- Achieve Compliance: Assist in meeting industry regulations such as GDPR and SOC 2 without the need for extensive security teams.
- Enhance Security: Enforce role-based access controls and policy-based governance to prevent unauthorized access.
- Scale Efficiently: Provide scalable solutions that grow with the organization, adapting to changing workforce needs.
Implementing IGA across industries ensures robust access governance, regulatory compliance, and enhanced security. Whether it’s a financial institution solution, a credit union solution, or IAM for healthcare, IGA provides the necessary framework to manage identities efficiently while mitigating risks.
7. Solving Cross-Application Challenges with IGA
Organizations today face challenges in managing user access across various applications, especially when dealing with complex IT environments and legacy systems. Implementing Identity Governance and Administration (IGA) solutions can help address these challenges effectively.
Preventing Cross-Application Segregation of Duties (SoD) Violations
SoD ensures that no single individual has control over all aspects of a critical task, reducing the risk of errors and fraud. In environments with multiple applications, enforcing SoD policies can be difficult.
IGA solutions provide a unified approach to manage user access, ensuring that SoD policies are consistently applied across all applications. This helps in identifying and eliminating potential SoD violations, thereby strengthening organizational security.
By defining and enforcing comprehensive access policies, organizations can eliminate cross-application SoD violations, thereby enhancing their security posture.
Simplifying Access Management in Hybrid IT Environments
Modern IT setups often combine on-premises systems with cloud-based services, creating hybrid environments. Managing user identities and access rights across these diverse platforms can be complex.
IGA solutions offer centralized control, allowing organizations to enforce security policies uniformly across all systems.
This centralization enhances security, simplifies compliance reporting, and reduces administrative efforts. Hybrid IT IAM solutions provide a seamless way to manage identities across these environments.
Integrating and Automating Legacy Systems
Many organizations continue to rely on legacy systems that may not natively support modern identity management protocols. Integrating these systems into a contemporary IGA framework is crucial for maintaining comprehensive security and compliance.
Automate homegrown legacy identity solutions by leveraging automation in identity lifecycle management—such as user provisioning, de-provisioning, and access reviews. This minimizes human error, reduces administrative burdens, and ensures legacy systems align with the organization’s overall identity governance strategy.
In conclusion, organizations can improve security and compliance by implementing IGA solutions that eliminate cross-application SoD violations, streamline hybrid IT IAM, and automate homegrown legacy identity solutions.
8. 2025 Trends in Identity Governance & Administration
In 2025, Identity Governance and Administration (IGA) is poised for significant advancements, driven by emerging technologies and evolving organizational needs. SecurEnds is at the forefront of these developments, offering innovative solutions that align with the latest modern IGA trends.
The Rise of AI-Driven Identity Analytics
Artificial Intelligence (AI in identity governance) is transforming IGA by enabling more sophisticated identity analytics. AI enhances the ability to detect anomalies, predict potential security threats, and automate complex decision-making processes.
SecurEnds leverages AI to provide advanced identity analytics, offering unique insights that strengthen identity governance and streamline security controls.
Expanding IGA Capabilities for Cloud and SaaS Applications
As organizations increasingly adopt cloud IGA and Software as a Service (SaaS) applications, there is a growing need for robust IGA solutions that can seamlessly integrate with these platforms.
SecurEnds’ holistic identity and infrastructure governance platform provides a unified view across both cloud and on-premises environments, ensuring comprehensive access management and compliance.
Predictions for Hybrid IT Environments and Identity Governance
The prevalence of hybrid IT environments, combining on-premises and cloud-based systems, necessitates adaptable IGA strategies. SecurEnds offers scalable solutions designed to empower organizations with seamless identity governance, access management, and compliance controls, effectively addressing the complexities of hybrid infrastructures.
By embracing these modern IGA trends, including cloud IGA and AI in identity governance, SecurEnds positions itself as a forward-thinking provider, committed to delivering cutting-edge solutions that meet the evolving demands of today’s digital landscape.
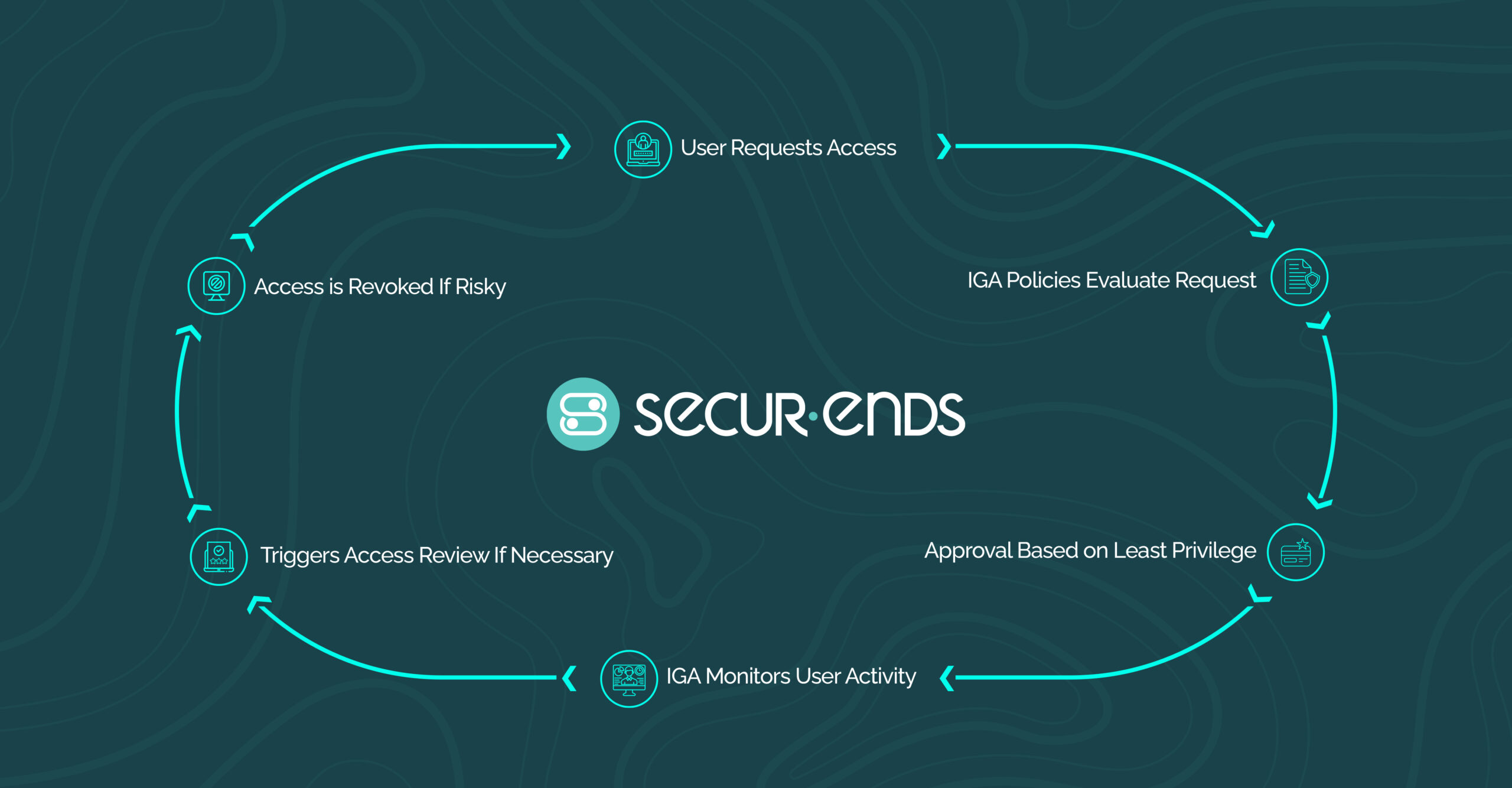
9. Difference Between IGA and IAM
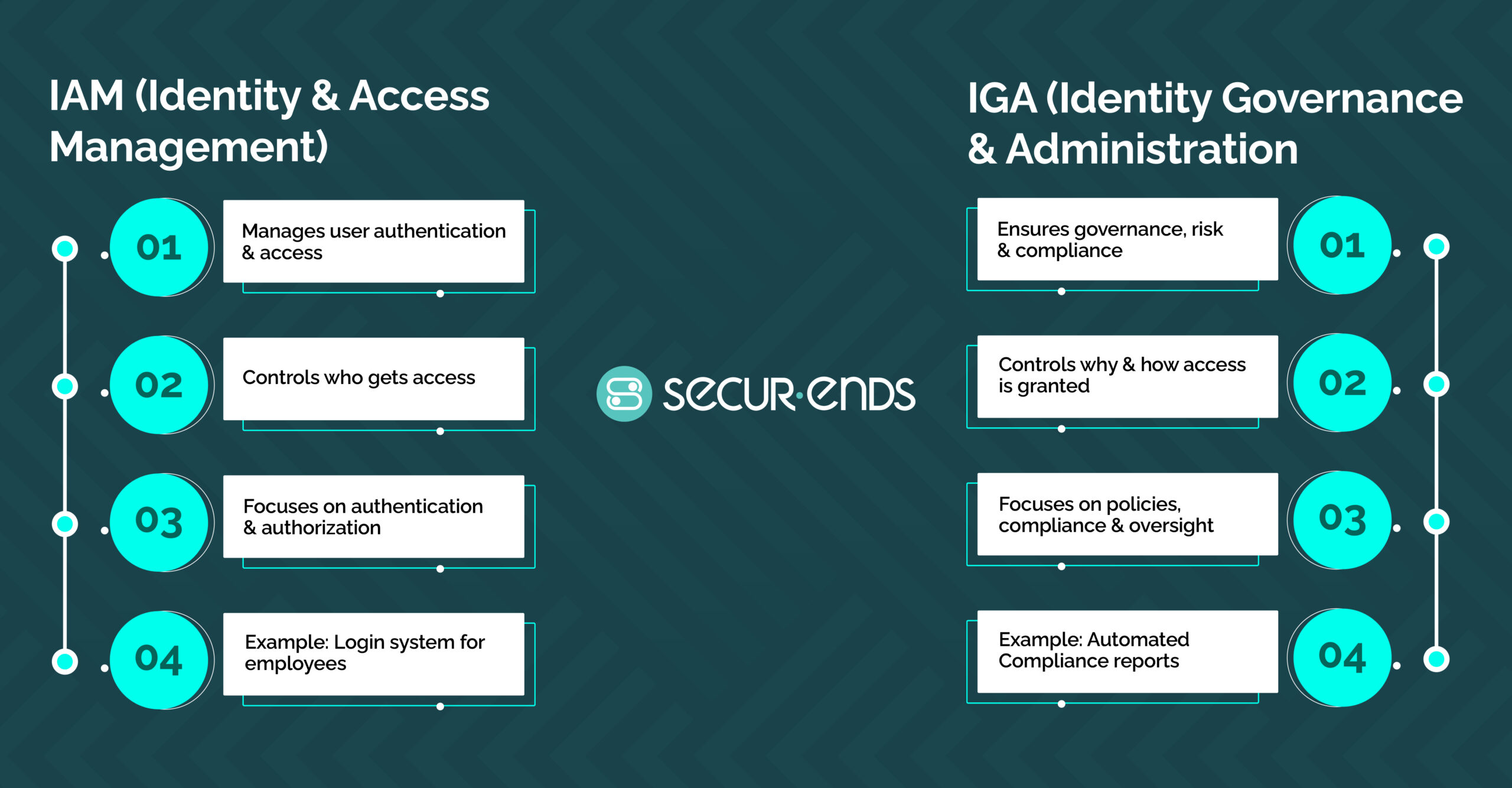
Identity Governance and Administration (IGA) and Identity Access Management (IAM) are two fundamental components of identity management, each serving distinct yet complementary roles. IAM vs IGA is often a point of confusion, as both deal with user access and identities, but their functions diverge in important ways.
IAM focuses on the operational aspects of managing user identities and their access to resources. It encompasses processes such as user authentication, authorization, and role assignment, ensuring that individuals can access the systems and data necessary for their roles. IAM systems automate the creation, maintenance, and deletion of user accounts, streamlining access management and enhancing security.
In contrast, IGA extends beyond the operational functions of IAM by emphasizing governance, compliance, and risk management. It involves defining and enforcing policies related to user identities, roles, and privileges to ensure that only authorized individuals have appropriate access to critical systems and data.
Governance vs access management becomes clear here, as IGA ensures access is compliant and governance-driven. IGA includes activities like access certifications, policy enforcement, and audit reporting, providing organizations with the tools to maintain compliance with regulations and internal policies.
While IAM addresses the “how” of access management, IGA focuses on the “why” and “what,” ensuring that access rights are appropriate, justified, and compliant with organizational standards and regulatory requirements.
The comparison of identity governance vs identity management is evident in these distinct roles: IAM governs access operations, while IGA focuses on the strategic governance of identities to minimize risk.
10. Managing Identity Governance in Hybrid IT Environments
Organizations today operate in complex IT landscapes that include on-premises systems, cloud services, and Software as a Service (SaaS) applications. Managing identities across these diverse environments presents unique challenges.
To effectively govern identities in hybrid IT IAM setups, organizations must implement solutions that provide centralized control over user access across all platforms. This involves integrating hybrid identity management and cloud IGA systems with various applications and services to ensure consistent access policies and compliance standards are maintained.
Automation plays a crucial role in this context. By automating processes such as user provisioning, de-provisioning, and access reviews, organizations can reduce manual errors, enhance operational efficiency, and ensure that access rights are promptly updated in response to changes in user roles or employment status.
11. Role-Based Access Control (RBAC)
Role-Based Access Control (RBAC) is a security methodology that restricts system access based on users’ roles within an organization. By assigning permissions to roles rather than individual users, RBAC simplifies access management and enhances security.
In an RBAC system, roles are defined according to job responsibilities, and users are assigned to these roles. Each role has specific permissions that grant access to necessary resources. This approach ensures that users have access only to the information and systems required for their duties, minimizing the risk of unauthorized access and potential data breaches.
RBAC not only streamlines access management but also supports compliance efforts by providing clear documentation of who has access to what resources, facilitating audits and regulatory reporting.
By leveraging scalable IAM solutions, organizations can efficiently manage access control, ensuring that RBAC systems grow seamlessly with the organization’s expanding needs and complexities.
12. Integrating Identity Governance with Existing Tools
Integrating IGA solutions with existing IT tools and platforms is essential for organizations seeking to enhance their identity management capabilities without overhauling their entire infrastructure.
Compatibility with widely used tools such as Okta Governance, Workday, and ServiceNow identity governance allows organizations to extend their identity governance frameworks seamlessly. For instance, IGA integrations with Okta can centralize user access controls and compliance reporting, while connecting with ServiceNow can streamline IT service management processes.
To ensure a smooth integration, organizations should assess the compatibility of their IGA solutions with existing systems, plan for data synchronization, and establish clear workflows for user provisioning and de-provisioning. This approach enables organizations to leverage their current investments while enhancing their identity governance posture.
13. Top Identity Governance and Administration Tools
Selecting the top IGA tools is crucial for organizations aiming to strengthen their identity management frameworks. Key features to consider include:
- Automated Access Certifications: Streamlining the process of reviewing and certifying user access rights to ensure compliance.
- Role-Based Access Control (RBAC): Implementing roles to manage user permissions efficiently.
- Comprehensive Audit Capabilities: Providing detailed logs and reports to support audits and regulatory requirements.
SecurEnds tools offer these features, enabling organizations to automate access reviews, manage roles effectively, and maintain compliance with various regulations.
Other notable identity governance software include SailPoint and Oracle Identity Governance, each offering robust features tailored to different organizational needs. Evaluating these tools based on specific requirements and existing IT infrastructure is essential for selecting the most suitable solution.
14. Benefits of IGA for Organizations
Implementing IGA solutions offers several tangible benefits, some of the IGA benefits include:
- Improved Compliance: Ensuring adherence to regulatory compliance requirements such as GDPR, HIPAA, and HITRUST by providing clear audit trails and facilitating access reviews.
- Enhanced Operational Efficiency: Automating identity management processes reduces manual workloads, accelerates user onboarding and offboarding, and minimizes errors.
- Reduced Risk of Data Breaches and Insider Threats: By enforcing strict access controls and regularly reviewing permissions, organizations can mitigate the risk of unauthorized access and potential data breaches and stabilize data security.
- Better User Experience: Streamlined access processes and self-service capabilities enhance the experience for both employees and customers, leading to increased productivity and satisfaction.
As organizations navigate an increasingly complex digital ecosystem, Identity Governance and Administration (IGA) has emerged as a cornerstone of modern cybersecurity and compliance strategies. Beyond mitigating risk and ensuring regulatory adherence, a well-executed IGA framework empowers businesses with operational agility, data integrity, and enhanced user trust.
SecurEnds stands at the forefront of this transformation, delivering cutting-edge IGA solutions that seamlessly integrate with hybrid IT environments, automate compliance processes, and fortify enterprise security. By adopting a forward-thinking approach to identity governance, organizations can not only safeguard their digital assets but also unlock new efficiencies, positioning themselves for sustained success in an era of rapid technological advancement.
The future of identity governance is intelligent, automated, and indispensable. The question is no longer whether your organization needs IGA—it’s how soon you can implement a solution that drives measurable impact.