Introduction to Identity and Access Management (IAM) Certification
Introduction to Identity and Access Management (IAM) Certification
In today’s interconnected digital world, organizations handle vast amounts of sensitive data, making security a top priority. Identity and Access Management (IAM) is a critical component of cybersecurity, ensuring that only authorized users can access specific systems, applications, and data. As cyber threats become more sophisticated, businesses must adopt robust IAM solutions to protect against unauthorized access, data breaches, and identity theft.
With the increasing reliance on cloud computing, remote work, and digital services, the demand for IAM professionals has risen significantly. Organizations are actively seeking experts who can design, implement, and manage Identity and access management strategies that enhance security and ensure compliance with industry regulations. IAM certification equips IT professionals with the necessary skills to safeguard digital identities, enforce access controls, and mitigate security risks.
As cybersecurity challenges continue to evolve, IAM certification is becoming an essential credential for those looking to advance their careers in IT security. It validates expertise in identity governance, authentication protocols, and access management frameworks, making certified professionals valuable assets in any organization’s security infrastructure.
2. Benefits of Identity & Access Management (IAM) Certification Courses
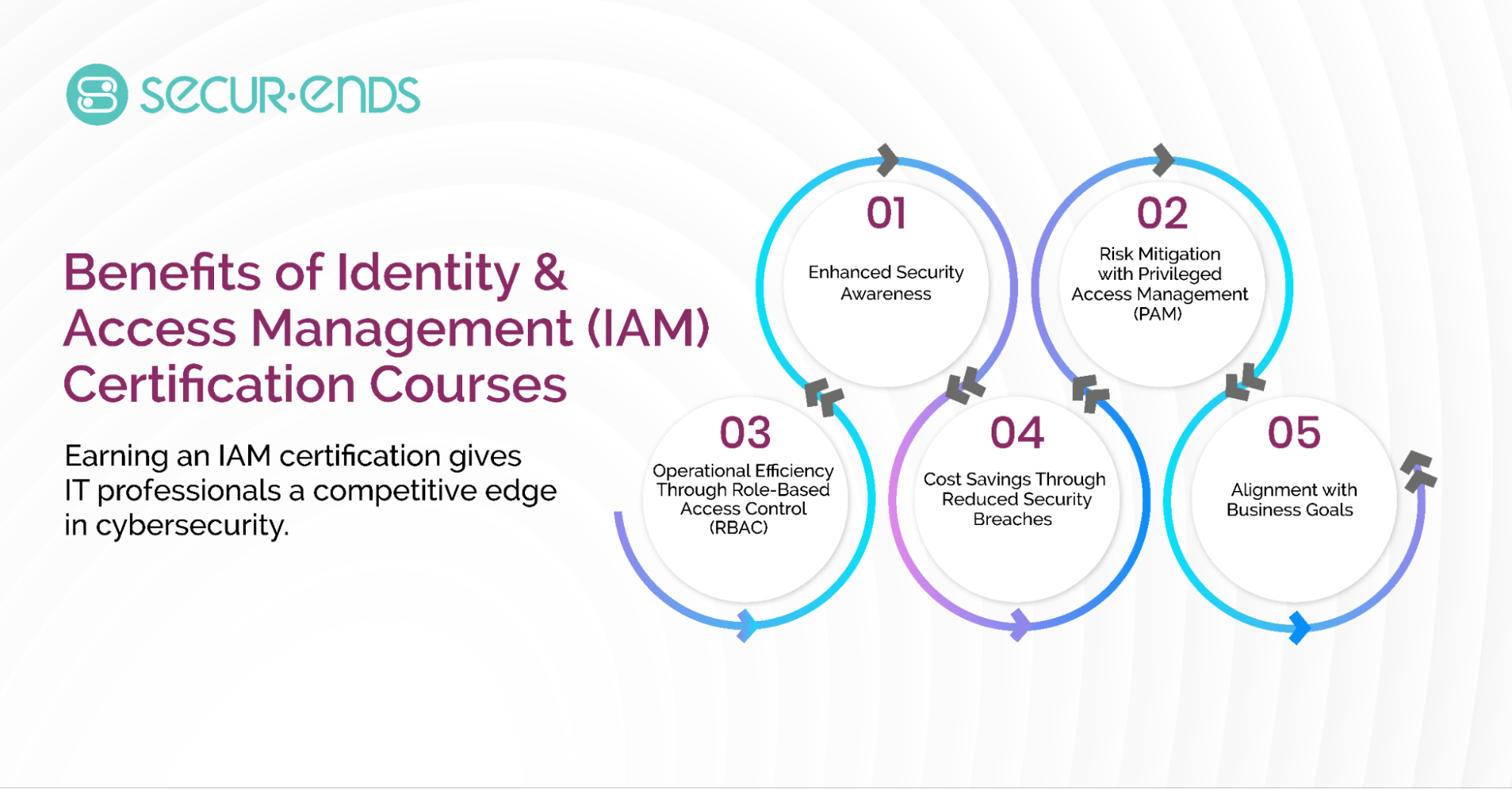
Earning a certification in Identity and Access Management (IAM) provides IT professionals with a competitive edge in the cybersecurity landscape. As organizations strive to strengthen their security frameworks, IAM-certified professionals play a crucial role in managing digital identities, enforcing access controls, and mitigating security risks. Here are some key benefits of IAM certification courses:
Enhanced Security Awareness
IAM training helps professionals develop a deeper understanding of multi-factor authentication (MFA) solutions, identity governance, and authentication protocols. By learning how to implement MFA effectively, IT teams can significantly reduce the risk of unauthorized access and credential-based attacks.
Risk Mitigation with Privileged Access Management (PAM)
Cybercriminals often target privileged accounts to gain unauthorized access to sensitive systems. IAM certification covers Privileged Access Management (PAM) strategies, ensuring professionals can implement robust security measures that protect high-level credentials and reduce insider threats.
Operational Efficiency Through Role-Based Access Control (RBAC)
A well-structured IAM framework improves efficiency by streamlining user access based on organizational roles. Certification programs emphasize role-based access control (RBAC), allowing IT teams to automate permissions and minimize manual interventions, thereby enhancing productivity and security.
Cost Savings Through Reduced Security Breaches
Organizations that invest in IAM strategies experience fewer security incidents, leading to reduced financial losses from cyberattacks and compliance violations. By implementing strong access controls and security measures, IAM-certified professionals help organizations avoid costly penalties associated with regulatory non-compliance.
Alignment with Business Goals
IAM is not just about security—it also supports organizational growth. Certified IAM professionals help align identity and access management strategies with business objectives by ensuring seamless user access, compliance adherence, and risk management. This contributes to operational resilience and long-term success.
IAM certification equips IT professionals with skills in MFA, RBAC, and PAM, enhancing their ability to secure digital systems. As cybersecurity grows in importance, certified experts play a key role in protecting organizational data.
Read: Mastering User Access Control: How to Safeguard Your Organisation from Security Breaches
3. Top Identity and Access Management Certifications
Earning identity and access management certifications is essential for IT professionals looking to advance their careers in cybersecurity. As businesses continue to strengthen their security frameworks, certified IAM experts are in high demand to manage user identities, enforce access controls, and mitigate security risks.
With rising cyber threats, organizations need skilled professionals who can implement strong IAM strategies. Obtaining top identity and access management certifications validates expertise in identity governance, authentication methods, and compliance requirements. It also enhances job prospects, increases earning potential, and opens doors to senior cybersecurity roles.
Comparison of the Top Identity and Access Management Certifications
There are several top identity and access management certifications that cater to different levels of expertise and career goals. Some of the most recognized certifications include:
- Certified Identity and Access Manager (CIAM) – Focuses on identity lifecycle management and governance.
- Certified Information Systems Security Professional (CISSP) – IAM Specialization – Covers IAM principles, access control models, and security best practices.
- Okta Certified Professional – Provides expertise in cloud-based identity management and authentication solutions.
- Microsoft Certified: Identity and Access Administrator Associate – Specializes in managing Azure AD, access policies, and identity protection.
- Certified Access Management Specialist (CAMS) – Focuses on access control techniques and IAM implementation strategies.
Key Skills Covered in IAM Certification Programs
Professionals pursuing identity and access management certifications gain expertise in:
- Identity governance and lifecycle management
- Authentication methods, including multi-factor authentication (MFA)
- Access control models and role-based access control (RBAC)
- Implementation of privileged access management (PAM) solutions
- Compliance with data security regulations such as GDPR and HIPAA
With the growing importance of cybersecurity, obtaining top identity and access management certifications ensures professionals stay ahead in the field, equipping them with the knowledge and skills needed to secure modern IT infrastructures effectively.
4. Top 10 Identity and Access Management Certification Courses

For IT professionals looking to strengthen their expertise in identity and access management (IAM), earning a certification is a great way to enhance career prospects. These top identity and access management certifications provide training in key areas like role-based access control (RBAC), multi-factor authentication (MFA) solutions, and Privileged Access Management (PAM). Below is a detailed list of the best IAM courses available, covering their core topics and intended audience.
1. Identity & Access Management – Learn OAuth, OpenID, SAML, LDAP
This course provides a deep dive into IAM protocols such as OAuth, OpenID, SAML, and LDAP. It explains how role-based access control (RBAC) and multi-factor authentication (MFA) solutions enhance security. The training is ideal for IT administrators, security analysts, and network engineers looking to understand access control models and implement strong authentication mechanisms.
2. AWS Identity & Access Management – Practical Applications
Focusing on AWS identity and access management (IAM), this course covers IAM policies, roles, and security best practices within the AWS ecosystem. It teaches how to configure permissions, manage access to AWS resources, and implement secure authentication protocols. The course is best suited for cloud security professionals, AWS administrators, and DevOps engineers.
3. Identity Access Management & Security Assessment and Testing
This course emphasizes Privileged Access Management (PAM) and access lifecycle management. It includes hands-on labs, compliance strategies, and risk mitigation techniques to prevent unauthorized access. IT professionals responsible for security audits, penetration testing, and risk assessment will find this training highly beneficial.
4. Introduction to Identity and Access Management
A foundational course covering IAM principles, multi-factor authentication (MFA) solutions, and password policy enforcement. It focuses on developing strong identity and access management (IAM) strategies for enterprises. Ideal for beginners and IT professionals looking to build a solid understanding of IAM fundamentals.
5. The Principles of Zero Trust
Zero Trust security is a rising standard in cybersecurity, and this course focuses on eliminating implicit trust within networks. It covers Privileged Access Management (PAM), real-time access controls, and the implementation of Zero Trust principles. IT security professionals and network architects can benefit from this course to strengthen their security posture.
6. CompTIA Security+ Cert (SY0-501): Identity/Access Management
A popular certification that includes identity and access management (IAM) training as part of its broader cybersecurity curriculum. The course covers multi-factor authentication (MFA) solutions, role-based access control (RBAC), and security best practices. It prepares candidates for the CompTIA Security+ certification, which is recognized globally in the cybersecurity industry.
7. Certified Information Privacy Technologist (CIPT)
This certification is designed for professionals who specialize in privacy and compliance. It covers top identity and access management certifications that focus on data privacy, regulatory frameworks, and access control mechanisms. IT security professionals handling compliance-related IAM implementation will benefit from this course.
8. Demystifying Identity and Access Management
A comprehensive course that breaks down IAM best practices, role-based access control (RBAC), and AWS identity and access management (IAM). It is designed for IT managers, analysts, and solution architects who want to develop a clear understanding of IAM processes and frameworks in enterprise settings.
9. AWS Identity and Access Management Foundations
This course provides in-depth knowledge of AWS IAM security policies, multi-factor authentication (MFA) solutions, and compliance standards. It covers identity federation, cross-account access, and secure AWS environment configuration. Ideal for cloud security professionals and AWS practitioners.
10. Privileged Access Management (PAM) with Cybrary
A hands-on training course that focuses on Privileged Access Management (PAM), teaching how to secure privileged accounts, enforce least privilege policies, and implement risk mitigation strategies. IT security professionals and administrators handling high-privilege accounts will gain valuable skills from this
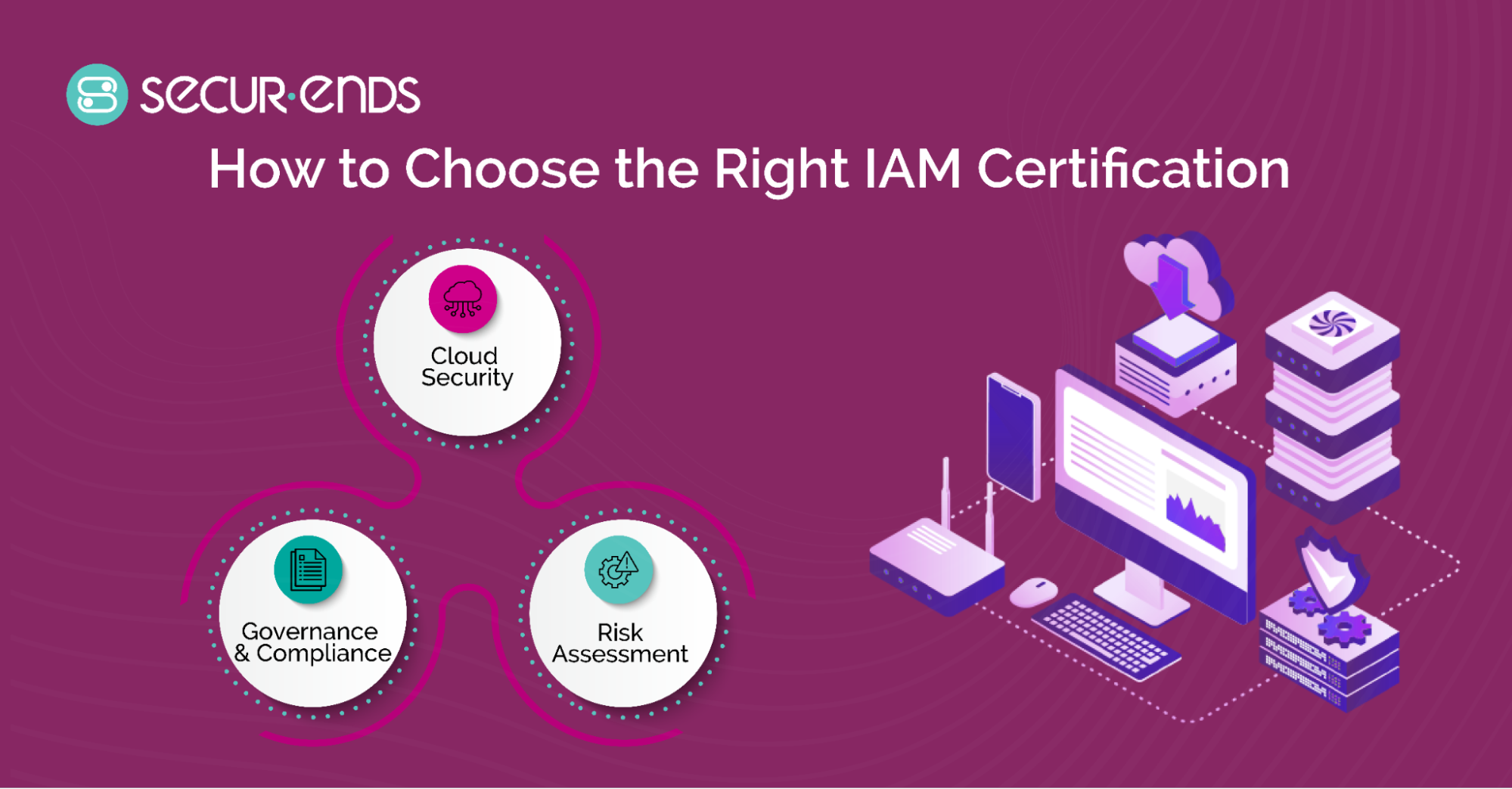
These top identity and access management certifications help IT professionals secure identities, control access, and prevent cyber threats. Training in role-based access control (RBAC), multi-factor authentication (MFA) solutions, and Privileged Access Management (PAM) equips them to protect organizational data. But, choosing the right certification is important for mastering identity and access management (IAM).
5. How to Choose the Right IAM Certification
With numerous identity and access management certifications available, selecting the right one depends on career goals, industry requirements, and the depth of knowledge required. IT professionals must assess their expertise level, specialization preferences, and future aspirations before choosing an IAM certification.
Assessing Career Goals and Selecting Relevant Identity and Access Management Certifications
Professionals looking to advance in cybersecurity, cloud security, or compliance should choose identity and access management certifications that align with their desired career path. For instance:
- Beginners should opt for foundational IAM courses covering key concepts like authentication, authorization, and identity governance.
- Mid-level professionals can benefit from specialized training in role-based access control (RBAC), multi-factor authentication (MFA) solutions, and identity federation.
- Experienced IT security professionals may pursue advanced certifications focusing on risk management, compliance, and Privileged Access Management (PAM).
Read: Avoid Stolen Credentials: Essential Tips for Securing Privileged User Accounts
Importance of Hands-On Training in Privileged Access Management (PAM)
Practical experience is crucial when learning IAM security measures. Certifications that include labs and real-world scenarios help professionals gain hands-on expertise in Privileged Access Management (PAM), an essential aspect of IAM security. By managing privileged accounts, enforcing least privilege policies, and preventing unauthorized access, PAM-certified professionals help strengthen organizational security.
The Role of Role-Based Access Control (RBAC) and Multi-Factor Authentication (MFA) Solutions in Training
A strong IAM certification should cover key security principles like role-based access control (RBAC) and multi-factor authentication (MFA) solutions.
- RBAC helps professionals understand how to streamline access management by assigning permissions based on job roles, reducing security risks.
- MFA solutions enhance authentication processes by adding extra layers of security, such as biometrics, one-time passwords, or hardware tokens.
How IAM Training Enhances Business Security
Effective identity and access management strategies are essential for protecting organizations from cyber threats. IAM training equips professionals with the skills to implement security best practices, enforce access controls, and manage user identities efficiently.
Implementing IAM Best Practices After Training
After completing IAM training, professionals can apply industry best practices to secure digital assets. This includes setting up strong authentication methods, enforcing least privilege policies, and regularly auditing access controls to ensure compliance.
How IAM Experts Strengthen Identity and Access Management Strategies
Trained IAM experts play a crucial role in improving identity and access management strategies. They design and implement secure authentication processes, monitor access to sensitive data, and mitigate risks associated with unauthorized access. Their expertise helps organizations maintain a strong security posture.
Real-World Applications of Privileged Access Management (PAM)
Privileged Access Management (PAM) is a key aspect of IAM security. PAM solutions help businesses protect high-risk accounts, limit administrative privileges, and prevent unauthorized access to critical systems. Real-world applications of Privileged Access Management (PAM) include securing cloud environments, managing privileged credentials, and preventing insider threats.
By mastering identity and access management strategies and implementing Privileged Access Management (PAM), IAM professionals enhance business security and protect organizations from cyber threats.
6. How IAM Training Enhances Business Security
Effective identity and access management strategies are essential for protecting organizations from cyber threats. IAM training equips professionals with the skills to implement security best practices, enforce access controls, and manage user identities efficiently.
After completing IAM training, professionals can apply industry best practices to secure digital assets. This includes setting up strong authentication methods, enforcing least privilege policies, and regularly auditing access controls to ensure compliance.
How IAM Experts Strengthen Identity and Access Management Strategies
Trained IAM experts play a crucial role in improving identity and access management strategies. They design and implement secure authentication processes, monitor access to sensitive data, and mitigate risks associated with unauthorized access. Their expertise helps organizations maintain a strong security posture.
Real-World Applications of Privileged Access Management (PAM)
Privileged Access Management (PAM) is a key aspect of IAM security. PAM solutions help businesses protect high-risk accounts, limit administrative privileges, and prevent unauthorized access to critical systems. Real-world applications of Privileged Access Management (PAM) include securing cloud environments, managing privileged credentials, and preventing insider threats.
By mastering identity and access management strategies and implementing Privileged Access Management (PAM), IAM professionals enhance business security and protect organizations from cyber threats.
7. Conclusion: Maximizing Potential Through IAM Certification
Earning identity and access management (IAM) certifications is key to career growth and stronger cybersecurity. Staying updated with the top identity and access management certifications helps IT professionals protect data, enforce security policies, and stay ahead of evolving threats.
Trained IAM experts improve security by managing Privileged Access Management (PAM), multi-factor authentication (MFA) solutions, and role-based access control (RBAC). Their skills help organizations prevent cyber risks and ensure compliance.
Continuous learning in identity and access management (IAM) keeps professionals competitive and prepared for future challenges. Investing in top identity and access management certifications benefits both individuals and businesses, making digital environments safer.