IAM: Top Challenges Facing Banks, Credit Unions, and Financial Institutions
IAM: Top Challenges Facing Banks, Credit Unions, and Financial Institutions

The finance sector is the lifeblood of the global economy, and its guardians—banks, credit unions, and financial institutions—are entrusted with protecting both the wealth of nations and the assets of individuals.
However, in this era of ever-advancing cyber threats and stringent regulatory frameworks, protecting these financial fortresses comes with its own set of unique challenges. Chief among them is the complex landscape of Identity and Access Management (IAM).
In our increasingly interconnected world, where data is the new currency, IAM plays a pivotal role in safeguarding financial institutions and their clients from cyber threats while ensuring compliance with a web of regulatory requirements. As the guardians of financial well-being, banks, credit unions, and financial institutions must navigate a labyrinthine landscape of data security, customer privacy, and user access control.
In this blog article, we’ll delve into the core challenges faced by these institutions in the realm of IAM. We’ll explore the intricacies of data protection, regulatory adherence, fraud prevention, and the delicate balance between security and user experience. Join us as we uncover the top IAM challenges that financial institutions grapple with daily and discover the strategies they employ to safeguard the financial bedrock of our world.
The current security landscape for the financial sector
Identity and access management (IAM) is a critical component of cybersecurity for banks, credit unions, and financial institutions. These organizations face unique challenges in this domain due to the sensitive nature of financial data and the regulatory requirements they must adhere to. Here are some of the top challenges they encounter:
- 👉 Data Security: Protecting customer and financial data is paramount. IAM systems must ensure that only authorized individuals have access to sensitive information. Any breach of this data can have severe financial and reputational consequences.
- 👉 Regulatory Compliance: The financial sector is heavily regulated, and compliance with regulations such as GDPR, HIPAA, and industry-specific standards like PCI DSS is mandatory. IAM systems must help institutions meet these requirements, which often involve stringent access control measures and audit trails.
- 👉 Fraud Prevention: Financial institutions are prime targets for fraudsters. IAM solutions must incorporate robust authentication mechanisms to prevent unauthorized access, including multi-factor authentication (MFA) and biometrics.
- 👉 Customer Experience: While security is critical, IAM systems must also provide a seamless and user-friendly experience for customers. Striking the right balance between security and convenience can be challenging.
- 👉 Hybrid Environments: Many financial institutions have a mix of on-premises and cloud-based systems, making IAM more complex. Managing identities and access across these hybrid environments can be challenging.
- 👉 Third-Party Access: Financial institutions often rely on third-party vendors and partners. Managing the access of external entities while ensuring security is a challenge, as they may not have the same level of security controls in place.
- 👉 Scale and Complexity: Large financial institutions have a vast number of employees, customers, and applications. Managing identities and access at scale, while keeping track of complex user roles and permissions, is a significant challenge.
- 👉 Employee Lifecycle Management: Onboarding, offboarding, and role changes for employees require efficient IAM processes to ensure that access rights are granted or revoked promptly and accurately.
- 👉 Privileged Access Management (PAM): Protecting privileged accounts is crucial because they have the highest level of access to sensitive data. Implementing effective PAM solutions is challenging but essential.
- 👉 Security Awareness: Ensuring that employees and customers are aware of security best practices and the importance of safeguarding their credentials is an ongoing challenge.
- 👉 Mobile and Remote Access: With the rise of remote work and mobile banking, IAM systems must accommodate secure access from various devices and locations, which can be more vulnerable to attacks.
- 👉 Legacy Systems: Older systems may lack modern IAM capabilities and integrating them with newer technologies can be complex.
- 👉 Incident Response: Having a plan in place for responding to security incidents related to identity and access breaches is crucial. This includes promptly revoking access and investigating the incident.
- 👉 Resource Constraints: Smaller financial institutions may lack the resources to invest in sophisticated IAM solutions and expertise, making them more vulnerable to security threats.
To address these challenges, banks, credit unions, and financial institutions should prioritize IAM as a foundational element of their cybersecurity strategy. This includes implementing strong authentication methods, regularly auditing and reviewing access rights, investing in IAM technologies that can scale, and ensuring compliance with relevant regulations. Additionally, fostering a security-conscious culture among employees and customers is vital for overall IAM success.
Examples of high-profile financial data breaches
The financial sector has experienced several high-profile data breaches over the years, some of which have had significant repercussions for both the affected organizations and their customers. Here are a few notable examples:
- 🚨 Equifax (2017): Equifax, one of the major credit reporting agencies, suffered a massive data breach that exposed the personal information of approximately 143 million Americans. The breach included sensitive data such as Social Security numbers, birthdates, and addresses. It was a severe blow to consumer privacy and led to congressional hearings and increased scrutiny of credit reporting agencies.
- 🚨 JPMorgan Chase (2014): JPMorgan Chase, one of the largest banks in the United States, experienced a breach in 2014 that compromised the contact information of 76 million households and 7 million small businesses. While no financial data or Social Security numbers were stolen, the incident raised concerns about the security of the financial industry.
- 🚨 Capital One (2019): Capital One, a major financial institution, suffered a data breach in 2019 that exposed the personal information of over 100 million customers. A former employee exploited a vulnerability to gain access to customer data stored on Amazon Web Services (AWS) servers. The breach underscored the importance of securing cloud-based infrastructure.
- 🚨 Target (2013): While Target is a retailer rather than a financial institution, the breach it experienced in 2013 had significant financial implications. Attackers gained access to Target’s payment system and stole credit card and personal information from approximately 40 million customers during the holiday shopping season.
- 🚨 Sony Pictures Entertainment (2014): Sony Pictures is not a financial institution, but the cyberattack it experienced in 2014 had financial consequences and highlighted the risks organizations face. The breach involved the theft of sensitive corporate data, including confidential emails and unreleased films, and was attributed to North Korean hackers.
- 🚨 SWIFT Banking System (Various): While not a single breach, the SWIFT banking system has been targeted multiple times by cybercriminals. Attackers have used SWIFT to transfer funds fraudulently, resulting in significant financial losses for banks and financial institutions. The Bangladesh Bank heist in 2016 is one of the most notable incidents, where cybercriminals attempted to steal nearly $1 billion but were partially thwarted.
Now that we know some real-world implications that have significantly impacted the financial sector, let’s take a look at where data breaches such as these usually start.
Where do these cyberattacks typically originate?
Data breaches in banks, credit unions, and financial institutions can be caused by a variety of factors and vulnerabilities. While the specific causes may vary from one breach to another, some common factors that have led to data breaches in these organizations include:
- 🔍 Phishing Attacks: Phishing remains one of the most prevalent and successful attack vectors. Cybercriminals use deceptive emails or messages to trick employees into revealing login credentials or clicking on malicious links.
- 🔍 Weak Authentication: Insufficiently strong or multifactor authentication methods can make it easier for attackers to gain unauthorized access to systems and sensitive data.
- 🔍 Insider Threats: Malicious or negligent actions by employees, contractors, or partners can result in data breaches. This may involve stealing sensitive information or inadvertently exposing it.
- 🔍 Third-Party Vulnerabilities: Many financial institutions rely on third-party vendors for various services. If these vendors have weak security practices or vulnerabilities, attackers can exploit them to gain access to the financial institution’s systems.
- 🔍 Unpatched Software: Failure to promptly apply security patches and updates to software and systems can leave vulnerabilities open for exploitation.
- 🔍 Misconfigured Security Settings: Inadequate security configurations on servers, databases, or cloud resources can lead to data exposure. This is a common issue, especially as organizations adopt complex cloud environments.
- 🔍 Social Engineering: Attackers may use social engineering techniques to manipulate employees into divulging sensitive information or compromising security controls.
- 🔍 Ransomware: Ransomware attacks can encrypt critical data, effectively locking organizations out of their own systems until a ransom is paid. Failure to protect against ransomware can result in data breaches and significant financial losses.
- 🔍 Inadequate Data Encryption: Lack of proper data encryption can expose sensitive information when it’s transmitted or stored, making it easier for attackers to access valuable data.
- 🔍 Poor Security Culture: In organizations where security is not a top priority and employees are not adequately trained on security best practices, the risk of data breaches increases.
- 🔍 Legacy Systems: Outdated or unsupported legacy systems may have known vulnerabilities that attackers can exploit. These systems can be challenging to secure and update.
- 🔍 Lack of Monitoring and Detection: Insufficient monitoring and detection mechanisms can delay the identification of a breach, allowing attackers to operate within a network undetected for extended periods.
- 🔍 Complexity of IT Environments: Financial institutions often have complex IT infrastructures with numerous interconnected systems and services, which can be difficult to secure comprehensively.
- 🔍 Mobile and Remote Work Vulnerabilities: The shift to remote work and the use of mobile devices can introduce new security challenges if not adequately managed.
- 🔍 Supply Chain Attacks: Attackers may compromise the supply chain, infecting software or hardware before it reaches the financial institution. This can result in breaches further downstream.
There are clearly a wide range of reasons security breaches and audit findings occur, which can make it very difficult to know where to start when to comes to addressing them. Now, let’s look at where IAM comes into play.
What IAM strategies are the most effective?
Effective Identity and Access Management (IAM) strategies for banks, credit unions, and financial institutions are critical for safeguarding sensitive data and ensuring compliance with regulations. While specific strategies may vary based on an organization’s size, complexity, and regulatory environment, several proven IAM strategies have demonstrated their effectiveness in this sector:
- ⚡ Strong Authentication: Implementing strong authentication methods, such as multi-factor authentication (MFA) or two-factor authentication (2FA), for both employees and customers is crucial. This adds an extra layer of security beyond just passwords.
- ⚡ Role-Based Access Control (RBAC): Implement RBAC to ensure that users have the right level of access based on their roles and responsibilities within the organization. This minimizes the risk of privilege abuse.
- ⚡ Least Privilege Principle: Apply the principle of least privilege to restrict access rights for users and systems to the minimum necessary for their tasks. This reduces the attack surface and limits the potential damage caused by insider threats.
- ⚡ Identity Governance and Administration (IGA): IGA solutions help organizations manage user identities and access rights efficiently. They automate onboarding, offboarding, and access reviews, ensuring that users have the appropriate access at all times.
- ⚡ Privileged Access Management (PAM): Protect privileged accounts and ensure strict control over who can access them. PAM solutions help organizations manage, monitor, and audit privileged access to critical systems and data.
- ⚡ Continuous Monitoring: Implement continuous monitoring of user activities, including behavior analytics, to detect and respond to suspicious or anomalous behavior promptly.
- ⚡ Single Sign-On (SSO): SSO solutions streamline the login process for users, reducing the need to remember multiple passwords while improving security by centralizing authentication.
- ⚡ Access Reviews and Recertification: Regularly review and recertify user access rights to ensure that they align with current job responsibilities and business needs. This helps prevent excessive or unnecessary access.
- ⚡ Data Encryption: Implement data encryption both in transit and at rest to protect sensitive information from unauthorized access, even if a breach occurs.
- ⚡ User Training and Awareness: Invest in ongoing security awareness training for both employees and customers to educate them about security best practices and potential threats like phishing.
- ⚡ Incident Response Plan: Develop a comprehensive incident response plan that outlines the steps to take in case of a security breach. This plan should include processes for containing the breach, notifying affected parties, and conducting a post-incident analysis.
- ⚡ Cloud Security: If using cloud services, adopt cloud-specific IAM solutions and best practices to secure access to cloud resources effectively.
- ⚡ Vendor Risk Management: Assess the security practices of third-party vendors and partners that have access to your systems or data. Ensure they meet your security standards and contractual obligations.
- ⚡ Regulatory Compliance: Stay up to date with relevant regulatory requirements and implement IAM solutions that help you meet compliance obligations, including audit trails and reporting capabilities.
- ⚡ User Self-Service: Provide users with self-service options for tasks like password resets and account recovery to reduce the burden on IT support while maintaining security.
- ⚡ Secure Mobile and Remote Access: Ensure that mobile and remote access to systems and data is secure, utilizing secure VPNs, mobile device management (MDM) solutions, and secure containerization where necessary.
- ⚡ Redundancy and Disaster Recovery: Implement redundancy and disaster recovery measures for IAM systems to ensure continuous operation and data availability even in the event of a system failure or breach.
Effective IAM is an ongoing process that requires a combination of technology, policies, and user education. Financial institutions should continuously assess and update their IAM strategies to adapt to evolving threats and regulatory changes while prioritizing both security and user experience.
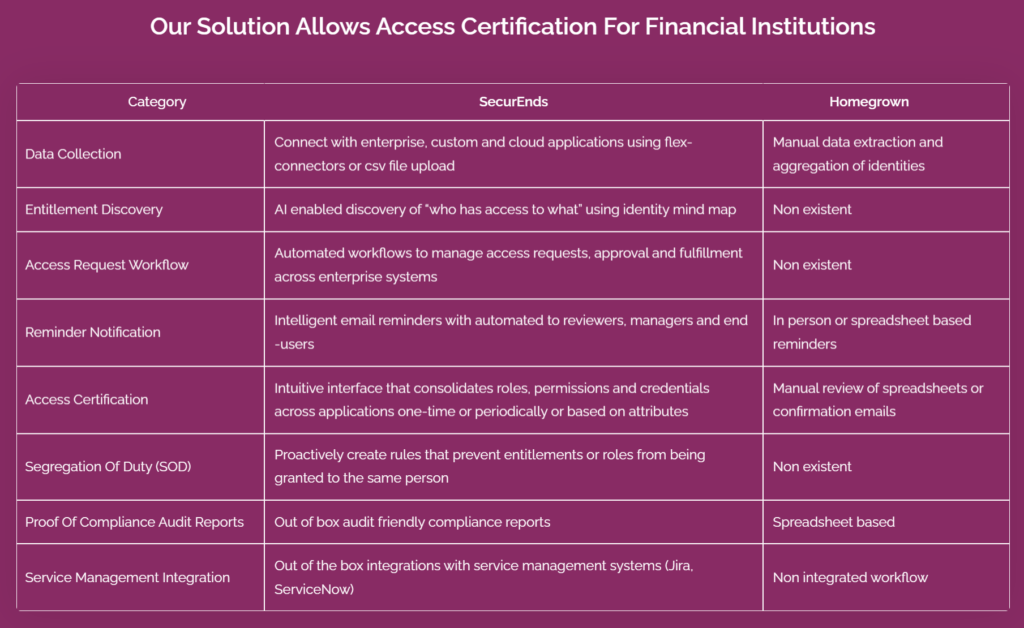
3 ways SecurEnds keeps your org secure and compliant
Automating user access reviews, gaining network visibility, and enforcing proper Segregation of Duties (SoD) are crucial components of an effective Identity and Access Management (IAM) strategy for organizations, especially in the financial sector. Here’s how each of these practices contributes to security and compliance:
1. Automating User Access Reviews
- ✅ Efficiency: Manual access reviews can be time-consuming and error-prone. Automation streamlines the process by automatically generating access review requests, sending notifications to responsible individuals, and providing a centralized platform for conducting reviews.
- ✅ Timeliness: Automated access reviews can be scheduled at regular intervals, ensuring that reviews are conducted promptly and on schedule. This helps identify and address inappropriate access rights in a timely manner.
- ✅ Accuracy: Automation reduces the risk of human errors that can occur during manual reviews. It helps ensure that access permissions align with the user’s current job role and responsibilities.
- ✅ Audit Trail: Automated access reviews typically provide an audit trail, documenting the review process, decisions made, and any actions taken to modify or revoke access. This documentation is valuable for compliance purposes.
- ✅ Compliance: Regular and well-documented access reviews help organizations demonstrate compliance with regulatory requirements, such as GDPR, HIPAA, and industry-specific standards like PCI DSS.
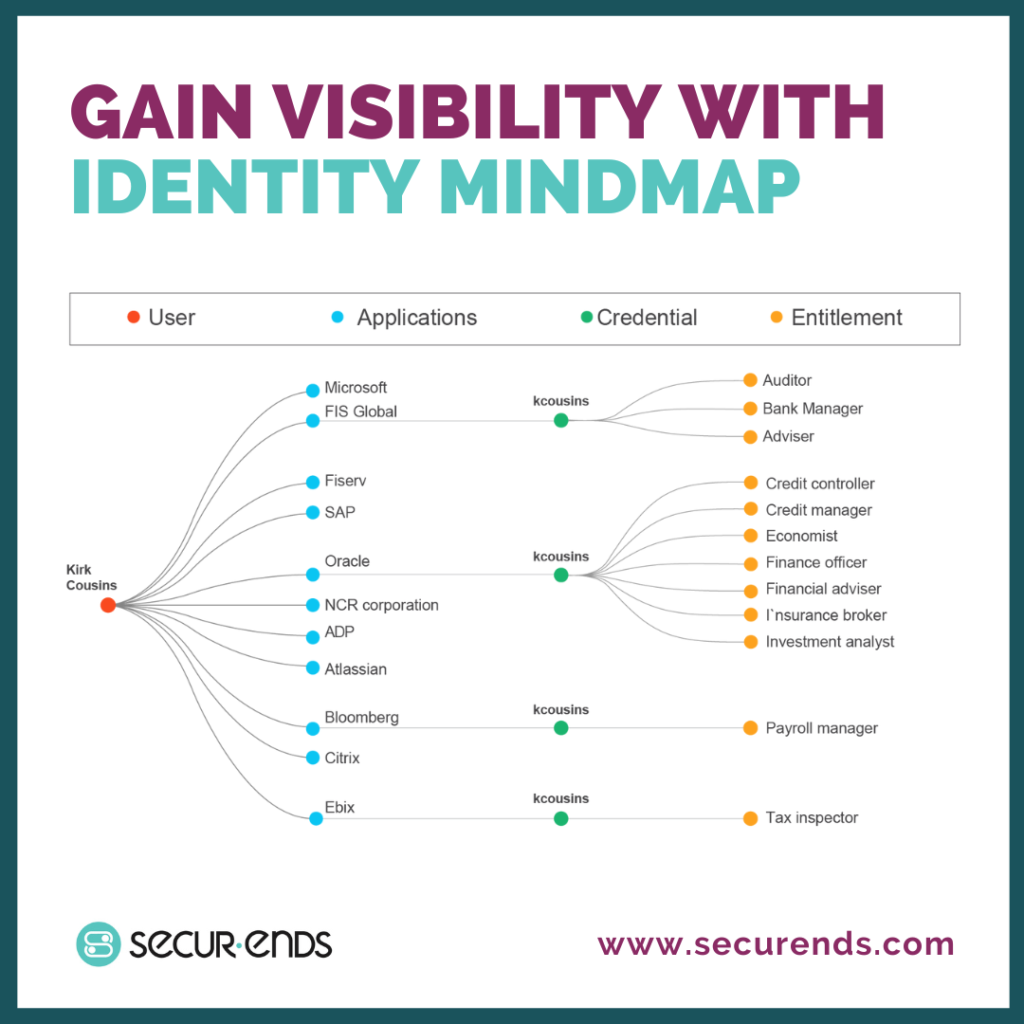
2. Gaining Network Visibility
- ✅ Threat Detection: Network visibility allows organizations to monitor user activities and network traffic. This helps in the early detection of suspicious behavior, such as unauthorized access attempts, data exfiltration, or unusual patterns of network traffic.
- ✅ Incident Response: A clear view of who has access to what enables organizations to respond quickly to security incidents. They can isolate compromised systems, block malicious activities, and conduct forensics to understand the scope and impact of the incident.
- ✅ Anomaly Detection: Visibility tools often include anomaly detection capabilities that can identify deviations from normal network behavior. This is particularly useful in detecting insider threats or advanced persistent threats (APTs).
- ✅ Compliance Reporting: Network visibility solutions can generate detailed reports on network activity, which are essential for compliance audits. This documentation provides evidence that security controls are in place and functioning as intended.
- ✅ Data Protection: Gaining visibility into data flows and access patterns helps organizations protect sensitive data. They can track data movement and access to ensure that data is not being mishandled or accessed inappropriately.
3. Enforcing Proper Segregation of Duties (SoD)
- ✅ Risk Mitigation: Proper SoD policies prevent individuals from having conflicting or excessive access rights. This reduces the risk of fraud, errors, and misuse of privileges, all of which can have significant financial and reputational consequences for financial institutions.
- ✅ Compliance: Regulatory requirements often mandate SoD controls to prevent fraud and ensure data integrity. Enforcing SoD policies helps organizations comply with these requirements.
- ✅ Automated Controls: IAM solutions can enforce SoD policies by automatically restricting access rights based on predefined rules. This ensures that users cannot perform conflicting duties without approval.
- ✅ Access Reviews: Automated access reviews play a role in SoD by regularly assessing user access rights for conflicts. Any violations can be flagged for remediation during the review process.
- ✅ User Accountability: Enforcing SoD helps establish clear lines of responsibility within an organization. Users are held accountable for their actions, and violations are more easily identified and addressed.
By combining these practices, financial organizations can create a robust IAM framework that not only enhances security by preventing unauthorized access and detecting suspicious activities but also facilitates compliance with regulatory requirements. This proactive approach to IAM helps organizations maintain the trust of their customers, protect sensitive financial data, and reduce the risk of security breaches and financial losses.
Schedule a call with our team today to see SecurEnds’ IAM capabilities in action.
✍ Article by Dino Juklo