What is Federated Identity Management (FIM)?
What is Federated Identity Management (FIM)?
As technology continues to evolve, managing digital identities securely has become a critical concern for organizations. Federated Identity Management (FIM) offers a solution by allowing users to access multiple applications across different organizations using a single set of credentials. This eliminates the need for multiple login credentials, simplifying authentication while maintaining security.
Federated Identity Access Management operates through a network of trusted entities known as trust domains, which can include businesses, organizations, or subsidiaries. These domains rely on an identity provider (IdP) to authenticate users and facilitate secure access. By eliminating the need for multiple passwords, FIM reduces security risks and enhances user experience.
This approach not only simplifies authentication but also improves cybersecurity by ensuring strong access controls. Organizations can streamline identity and access management while reducing administrative overhead and minimizing vulnerabilities associated with password fatigue.
As businesses increasingly adopt cloud-based services and interconnected systems, FIM has become an essential component of modern cybersecurity strategies. It strengthens security frameworks, enhances user convenience, and fosters trust between organizations, making it a critical solution for managing digital identities effectively.
2. What is Federated Identity and Access Management (FIM)?
Federated Identity and Access Management (FIM) is an authentication framework that allows users to access multiple applications or systems using a single set of credentials across different organizations or security domains. This approach enhances security and user convenience by eliminating the need to manage separate login credentials for each service. By enabling seamless access across platforms, FIM plays a crucial role in enterprise security and user experience.
How FIM Differs from Traditional Authentication Methods
Traditional authentication methods require users to create and maintain separate credentials for different systems, leading to password fatigue and security vulnerabilities. In contrast, Federated Identity Management leverages a federated identity model where user authentication is handled by a central identity provider (IdP). Here are some key differences:
- Single Sign-On (SSO) Integration: FIM enables users to sign in once and gain access to multiple applications without repeated authentication.
- Cross-Domain Authentication: Unlike traditional methods, which operate within a single domain, FIM facilitates authentication across different organizations and security frameworks.
- Reduced Password Management Risks: By minimizing the need for multiple credentials, FIM reduces the risk of phishing attacks and password-related security breaches.
Why Businesses Are Shifting Toward Federated Identity Management
Organizations are increasingly adopting federated identity management due to its numerous benefits in security, compliance, and operational efficiency. Some key reasons include:
- Enhanced Security and Compliance: FIM ensures strong authentication mechanisms and reduces password vulnerabilities, aligning with regulatory requirements such as GDPR and HIPAA.
- Improved User Experience: Employees, partners, and customers benefit from seamless access to multiple services, leading to higher productivity and satisfaction.
- Cost and IT Efficiency: By reducing password resets and IT support costs, businesses can streamline authentication processes and improve resource utilization.
- Cloud and Multi-Platform Integration: With the rise of cloud computing and remote work, FIM enables secure access across various cloud platforms and enterprise applications.
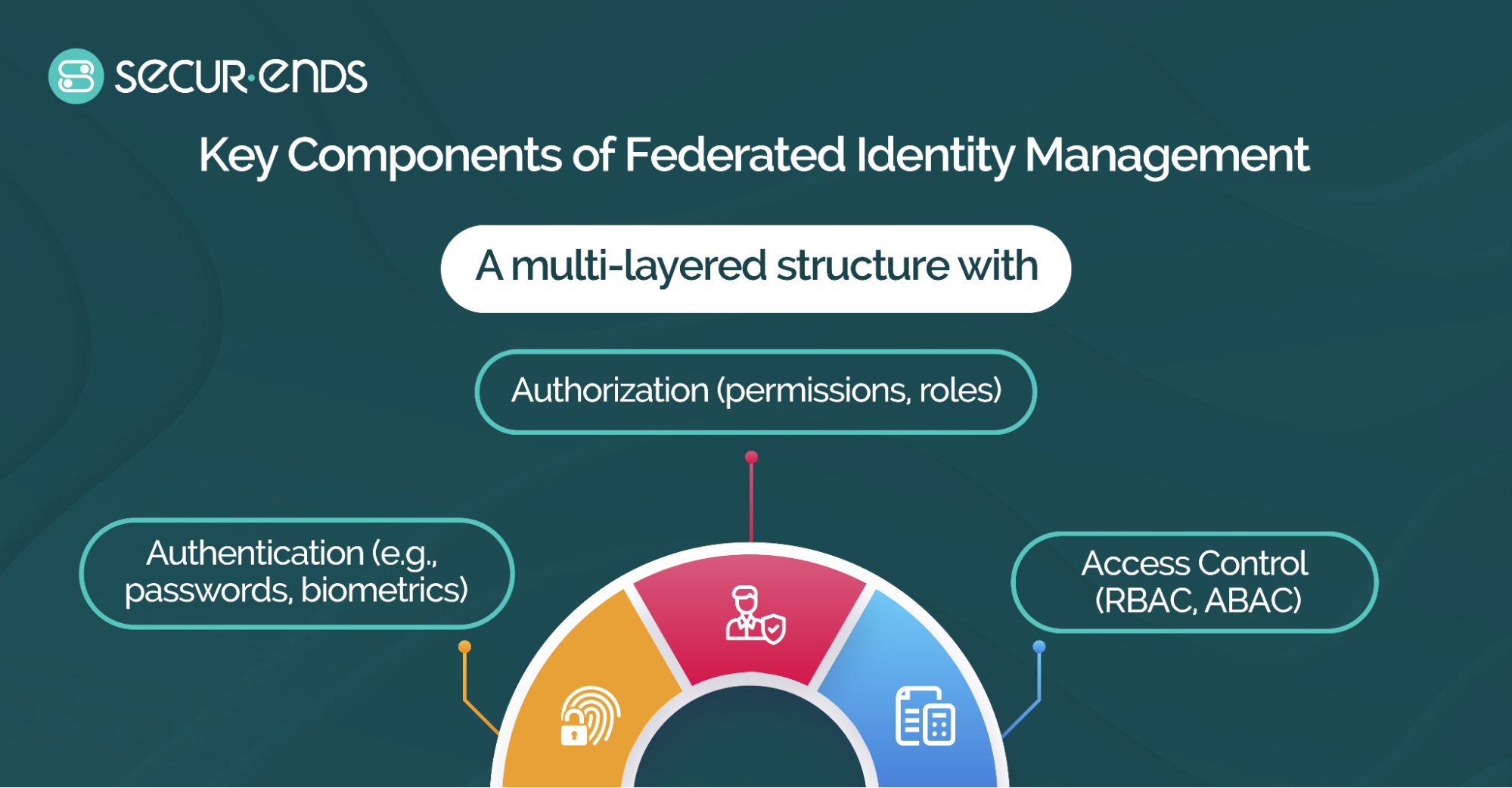
3. Key Components of Federated Identity Management
Authentication
Authentication verifies a user’s identity before granting access to resources. Federated Identity Access Management commonly employs multi-factor authentication (MFA) to enhance security by requiring users to provide multiple forms of verification, such as passwords, biometrics, or security tokens. Additionally, single sign-on (SSO) simplifies authentication by allowing users to access multiple applications with a single set of credentials.
Authorization
Once authenticated, users are granted specific permissions based on predefined policies. Authorization ensures users can only access resources relevant to their roles and responsibilities.
Access Control
Access control defines security policies governing user permissions. Role-based access control (RBAC) and attribute-based access control (ABAC) are commonly used mechanisms to enforce security policies.
Identity Providers (IdPs)
IdPs are responsible for authenticating users and providing identity credentials to service providers. Examples include Microsoft Azure AD, Google Identity, and Okta.
Service Providers (SPs)
SPs are platforms or applications that rely on federated identity access management to verify users without maintaining their authentication credentials. Examples include cloud-based applications, enterprise software, and SaaS platforms.
4. How Federated Identity & Access Management Works
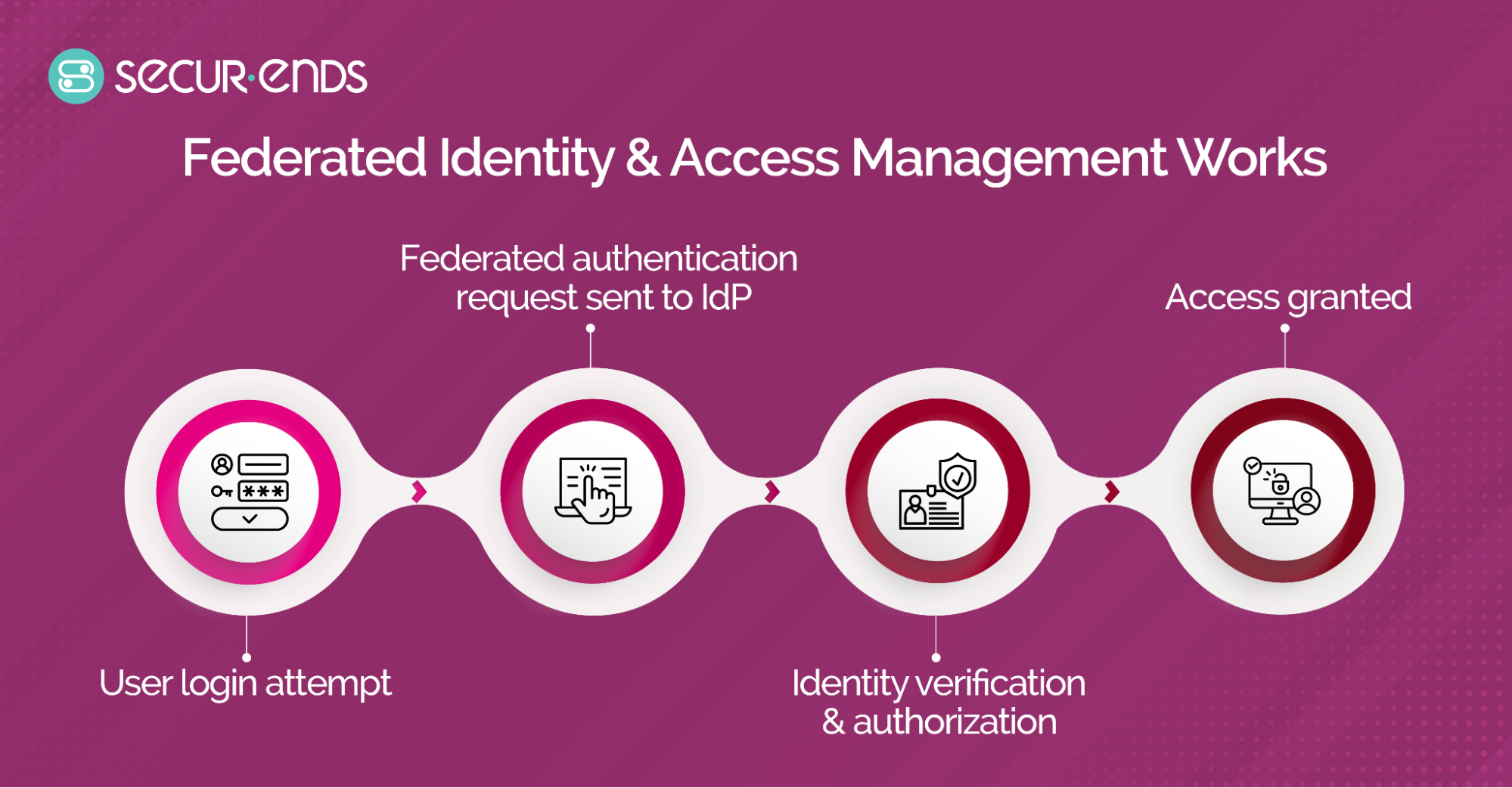
- User Login Attempt
When a user initiates authentication through a service provider (SP) that employs federated identity management, it triggers a secure and seamless authentication mechanism. This marks the beginning of a unified access experience across interconnected services.
For example, an employee logging into a corporate workspace enters their credentials, signaling their intent to access enterprise tools and applications.
- Federated Authentication Request –
Once the user attempts to log in, the service provider generates and transmits a federated authentication request to the designated identity provider (IdP). This request is essential for ensuring secure authentication without exposing sensitive credentials.
Key objectives of this request include:
Identity Verification: The service provider does not store or manage authentication data directly. Instead, it delegates the authentication process to a trusted identity provider.
Data Security: The request ensures that sensitive authentication data, such as passwords or biometric credentials, remains within the secure domain of the identity provider, mitigating risks of exposure or breaches.
- Identity Verification & Authorization
Federated identity management relies on industry-standard authorization protocols to securely transmit authentication and access data between the identity provider and the service provider.
- OAuth (Open Authorization): This framework allows users to grant limited access to their data without revealing credentials. For instance, logging into a third-party service using Google or Facebook credentials utilizes OAuth-based authentication.
- OpenID Connect (OIDC): Built on top of OAuth 2.0, OpenID Connect focuses on identity verification, providing ID tokens that enable the service provider to confirm the user’s identity securely.
- SAML (Security Assertion Markup Language): SAML facilitates single sign-on (SSO) by securely transferring authentication data between different domains. For example, a university network using SAML enables students to access multiple services with a single login.
Upon receiving the authentication request, the identity provider follows a comprehensive verification process to confirm the user’s identity and access rights.
Identity Verification Methods:
Credentials Validation: The identity provider checks if the provided username and password match registered account details.
Biometric Authentication: Additional security measures like fingerprint scanning or facial recognition enhance identity verification.
Multi-Factor Authentication (MFA): A combination of authentication factors, such as a password and a temporary one-time passcode (OTP), is used to strengthen security.
Access Rights Evaluation:
Permissions Check: The identity provider reviews the user’s assigned roles and permissions within the system to determine accessible resources.
Service-Specific Requirements: Certain services may require additional clearance, and the identity provider ensures compliance before granting access.
- Access Granted
After successful authentication and authorization, the service provider grants the user access to its resources based on identity verification and predefined permissions.
- Personalized Access Experience: The user gains entry to various platforms—such as cloud storage, corporate applications, or e-commerce services—while maintaining a seamless and tailored experience.
- Enhanced Security Controls: The system ensures that only authenticated and authorized users access sensitive data, significantly reducing the risk of unauthorized access or cyber threats.
By leveraging federated identity management, organizations enhance security, simplify authentication processes, and improve user convenience through seamless single sign-on (SSO) across multiple platforms.
5. Benefits of Federated Identity and Access Management
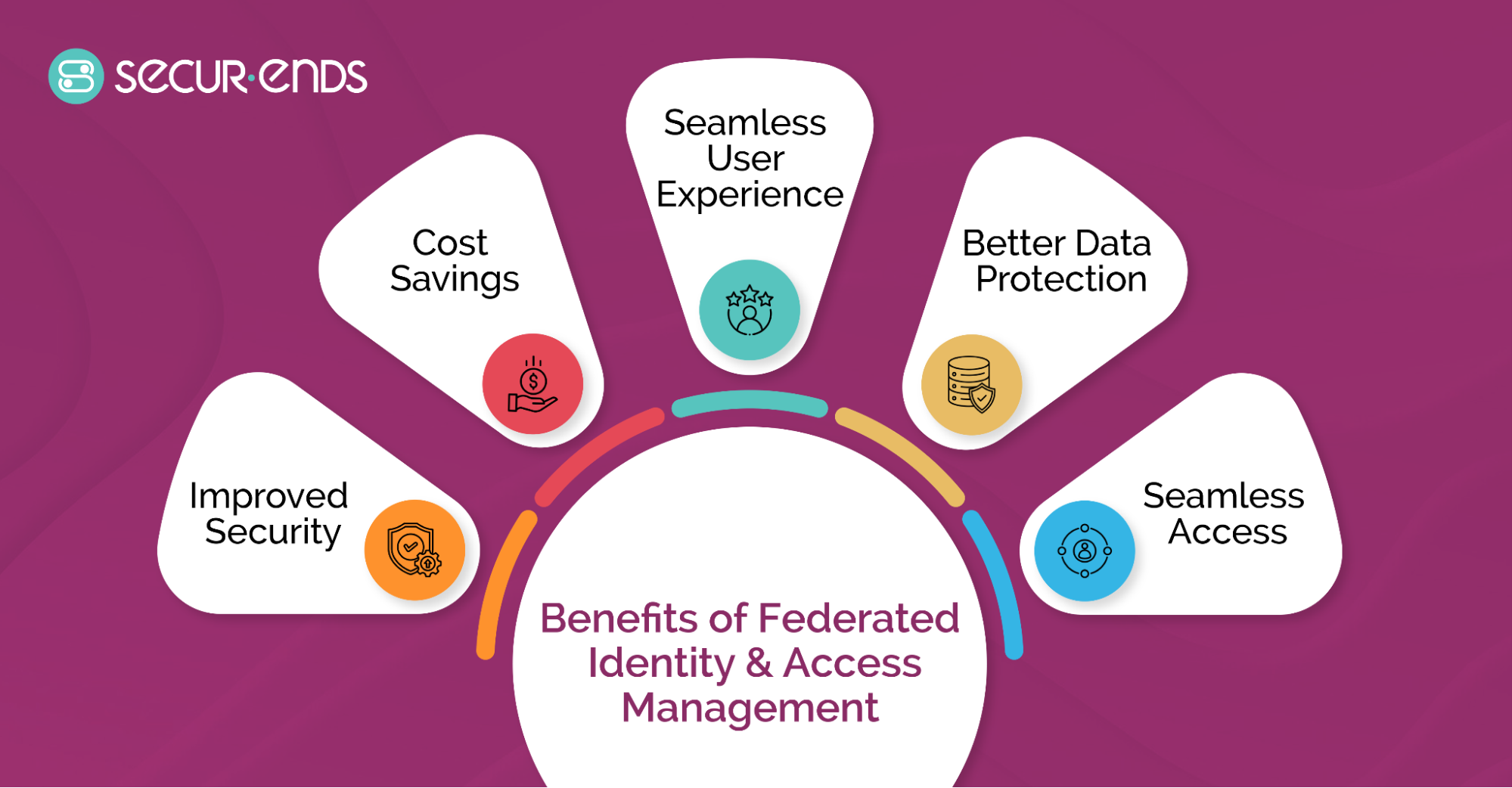
Improved Security
Federated Identity Access Management centralizes authentication, reducing the risk of password-related breaches. Multi-factor authentication further strengthens security.
Cost Savings
Organizations save costs by reducing password reset requests and IT workload associated with managing multiple authentication systems.
Seamless User Experience
Federated Identity and Access Management provides a frictionless login experience through single sign-on (SSO) , allowing users to access multiple applications without repeated logins.
Better Data Protection
With fewer authentication silos, organizations minimize security vulnerabilities associated with fragmented identity management.
Scalability
FIM simplifies user management across different platforms, making it ideal for enterprises with growing authentication needs.
6. The Role of Single Sign-On (SSO) in Federated Identity Management
Single sign-on (SSO) allows users to authenticate once and access multiple services without re-entering credentials. It enhances convenience and security by reducing password fatigue.
How SSO Simplifies Authentication
SSO integrates with federated identity access management to streamline authentication across various platforms, improving efficiency and security.
Difference Between FIM and Traditional SSO
While SSO simplifies authentication within an organization, Federated Identity Access Management extends authentication across multiple organizations and service providers.
7. How Multi-Factor Authentication Enhances Federated Identity Security
Multi-factor authentication requires users to verify their identity using multiple authentication factors, such as passwords, OTPs, biometrics, or security keys.
Combining SSO with MFA
Integrating MFA with single sign-on (SSO) strengthens security by adding an extra layer of authentication while maintaining a seamless user experience.
Common Authentication Factors
- Something You Know – Passwords, PINs
- Something You Have – OTPs, security tokens
- Something You Are – Biometrics (fingerprints, facial recognition)
8. Implementing Federated Identity and Access Management
Steps for Integration
- Assess business requirements and security needs.
- Choose suitable IdPs and SPs.
- Implement Single Sign-On (SSO) and Multi-Factor Authentication (MFA) for enhanced security.
- Configure access control policies to align with identity and access best practices.
- Continuously monitor authentication processes and maintain compliance.
Choosing the Right IdPs and SPs
Selecting the right identity providers (IdPs) and service providers (SPs) is crucial for seamless authentication and secure federated identity access management. A well-integrated system ensures smooth user experiences while maintaining robust security protocols.
Best Practices for Security and Compliance
- Enforce MFA for all users.
- Regularly audit authentication logs.
- Ensure compliance with regulations like GDPR and HIPAA.
9. Challenges and Considerations in Federated Identity Management
Security Concerns
Centralizing authentication through federated identity management introduces risks such as identity provider breaches. Implementing strong security measures, including encryption and multi-factor authentication (MFA), helps mitigate these vulnerabilities and ensures robust identity and access protection.
Compliance Requirements
Organizations must comply with regulations such as GDPR, HIPAA, and SOC 2 to ensure data privacy and security.
Implementation Complexity
Integrating FIM requires collaboration between IT teams, service providers, and compliance officers to ensure seamless adoption. Establishing clear identity and access policies ensures seamless adoption and minimizes integration challenges.
10. Future Trends in Federated Identity & Access Management
AI and Automation
Artificial intelligence enhances identity verification, anomaly detection, and adaptive authentication in federated identity and access management systems.
Blockchain in Identity Security
Decentralized identity and access management using blockchain can enhance security and privacy in federated authentication.
Advancements in MFA
New authentication methods, such as passwordless authentication and adaptive multi-factor authentication, improve security while reducing friction for users.
Conclusion
Federated Identity and Access Management (FIM) is a powerful solution that enhances security, simplifies authentication, and improves user experience across multiple platforms. By implementing FIM with SSO and MFA, organizations can strengthen security, reduce costs, and ensure compliance with industry regulations. As technology evolves, AI, automation, and blockchain will further shape the future of federated identity management, making it an essential component of modern cybersecurity strategies.