Automotive Services Company Reduces Identity Risk by 90% with SecurEnds User Access Review Management Platform
BACKGROUND The organization provides a wide range of services catering to automotive needs, including roadside assistance, vehicle maintenance, insurance products, and travel assistance, ensuring support to millions of members across the USA. CHALLENGE The client faced a critical need to streamline user access reviews for …
Customer Story: Top 5 Fortune 500 Healthcare Company Automates Security & Compliance with SecurEnds Identity Management Solution
BACKGROUND This company is a major player in the healthcare industry, operating globally. They act as a middleman between manufacturers and healthcare providers, distributing pharmaceuticals, medical supplies, and laboratory products. CHALLENGE This enterprise client required a way to efficiently manage a large number of identities …
Customer Story: Telecom Leader Reduces User Access Review Time by 67% with SecurEnds
BACKGROUND The client is an international telecommunications company mainly serving mid-size businesses. Before adopting SecurEnds, they were conducting user access reviews manually using spreadsheets which slowed their process down heavily. CHALLENGE Initially, the client was not using any automation tools to conduct user access reviews, …
Customer Story: Regional Bank Rapidly Scales User Access Reviews 4X with SecurEnds Automation
BACKGROUND A fast-growing regional bank serving multiple areas of North America, this organization’s rapid expansion led to a sharp increase in applications used by their staff (300%), which quickly made manual identity and access management processes impossible. CHALLENGE Manual application reviews were far too time-consuming, …
Customer Story: FinTech Company Accelerates User Access Reviews by 75% with SecurEnds Identity MindMap
BACKGROUND The organization provides market-leading technology that simplifies and unifies healthcare payments. Much like their business goals, they wanted to streamline user access reviews to better secure their organization and more easily adhere to regulations. CHALLENGE The client initially conducted user access reviews using Excel …
How Decentralized User Access Reviews Empower Efficiency in Large Enterprise Companies [Identity Experts Series]
In this article, we’ll explore the differences between centralized and decentralized user access review management in large enterprises. After learning the pros and cons of each, you’ll also find out why choosing the right SaaS solution is key to making the most of your efforts. …
Customer Story: Leading Healthcare Provider Reduces User Access Review Time by 50%
BACKGROUND A large provider of healthcare services to Medicare plan-based individuals, the client was relying on manual spreadsheets for user access reviews which posed major risks for HIPAA compliance and placed a time-consuming burden on their team. CHALLENGE The client’s manual user access review process …
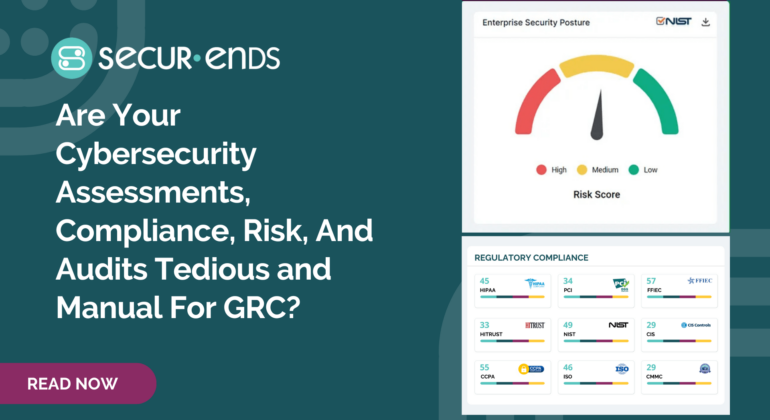
Are Your Cybersecurity Assessments, Compliance, Risk, And Audits Tedious and Manual For GRC?
Cyber Security assessments and compliance is manual and tedious with control questionnaire collecting answers to the questions and documents in organizations for GRC. Automated Security Risk Assessment help internal IT team efficiently demonstrate compliance with standard such as NIST, CIS Controls, PCI, SOX, GDPR, ISO27001, …
Ultimate 2024 Compliance Checklist: User Access Reviews & Best Practices
Compliance has become more critical than ever for organizations across industries. As we step into 2024, the need for efficient user access controls and reviews is continuing to play a key role in safeguarding sensitive data and meeting regulatory requirements. This comprehensive guide is crafted …
Year in Review 2023: Insights, Updates, and Customer Success
As we bid farewell to another transformative year in the realm of cybersecurity, it’s time to reflect on the milestones, innovations, and achievements that have defined our journey at SecurEnds. In this comprehensive article, we’ll delve into captivating insights, unveil the latest advancements in our …