Automated Compliance Management: The Key to Staying Ahead in a Regulated World
In today’s fast-paced digital world, staying compliant with industry regulations is no longer optional. …
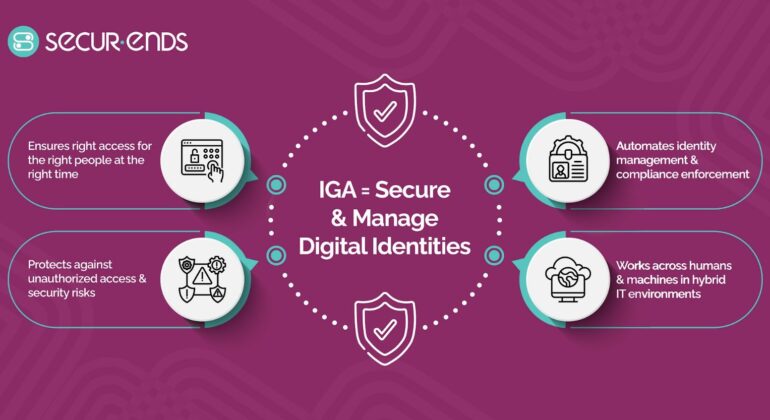
Navigating Premium User Access Management: A Complete Overview
In today’s digital age, where data breaches and cybersecurity threats loom large, user access management (UAM) has emerged as an indispensable aspect of organizational security. Businesses are no longer limited by physical boundaries, …
Fundamentals and Best Practices of Healthcare Identity and Access Management
In the digital age, the healthcare industry is increasingly reliant on technology to manage patient data, …
Cracking the Code of Compliance Automation with Expert Insights and Best Practices
In today’s complex regulatory landscape, organizations are increasingly recognizing compliance as both a …
Automating User Access Reviews for Jack Henry’s SilverLake: How SecurEnds Empowers Credit Unions to Enhance Security and Compliance
In today’s rapidly evolving digital landscape, credit unions must prioritize robust security measures to protect member data and ensure regulatory compliance. A critical component of this security framework is the implementation of effective user access reviews, also known as access certifications. These reviews involve the …
Who Benefits Most from GRC Solutions in Healthcare Regulatory Compliance?
The healthcare industry is one of the most highly regulated sectors globally. Risks and Compliance rank as …
How AI and Automation Are Shaping GRC Software for Compliance and Reporting
As businesses navigate an increasingly complex regulatory environment, the need for robust Governance, Risk …
How Blockchain and Fintech are Elevating GRC Tools in Financial Services
Governance, Risk and Compliance (GRC) tools have been critical to the financial services industry for years …