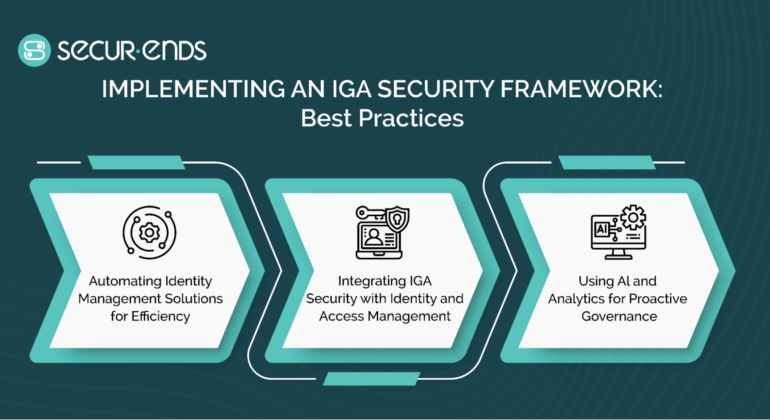
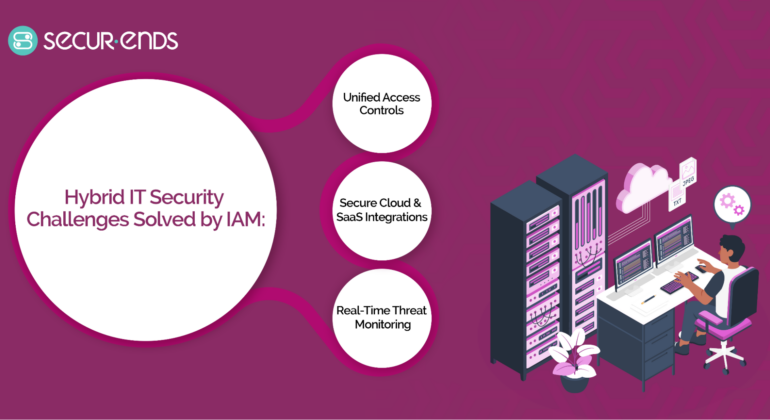
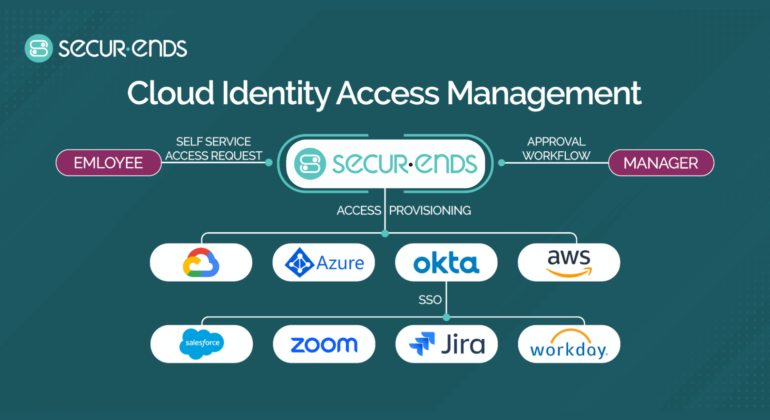
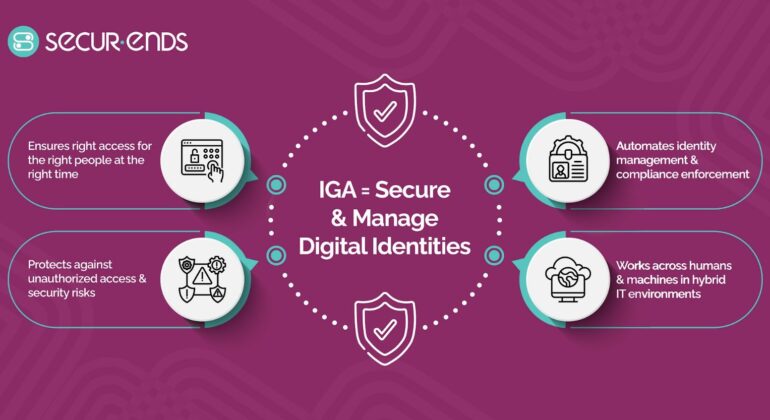
Automated Compliance Management: The Key to Staying Ahead in a Regulated World
In today’s fast-paced digital world, staying compliant with industry regulations is no longer optional. …
Navigating Premium User Access Management: A Complete Overview
In today’s digital age, where data breaches and cybersecurity threats loom large, user access management (UAM) has emerged as an indispensable aspect of organizational security. Businesses are no longer limited by physical boundaries, …
Fundamentals and Best Practices of Healthcare Identity and Access Management
In the digital age, the healthcare industry is increasingly reliant on technology to manage patient data, …
Cracking the Code of Compliance Automation with Expert Insights and Best Practices
In today’s complex regulatory landscape, organizations are increasingly recognizing compliance as both a …