Best Ways to Conduct User Access Reviews: Strategies for Efficiency and Accuracy
Best Ways to Conduct User Access Reviews: Strategies for Efficiency and Accuracy

In this comprehensive guide, we’ll delve into the best ways to conduct user access reviews. We’ll explore why they are critical, the common challenges organizations face, the steps involved in an effective review process, and best practices to make them as seamless and impactful as possible. Let’s jump in.
Why Are User Access Reviews Important?
Before diving into the details of conducting user access reviews, it’s essential to understand why they are so important for your organization. Here are a few key reasons:
- 1️⃣ Improving Security: Access reviews are essential for ensuring that users only have the permissions necessary to perform their job functions. Over time, employees may accumulate excessive privileges due to job changes, project involvement, or other circumstances. These excessive privileges can lead to potential security risks, such as unauthorized access to sensitive information. By regularly reviewing user access, organizations can prevent these risks and ensure that access rights are correctly aligned with each employee’s responsibilities.
- 2️⃣ Compliance with Regulatory Standards: Many regulatory frameworks, such as GDPR, HIPAA, SOX, and PCI-DSS, require organizations to conduct regular user access reviews to ensure that only authorized personnel have access to sensitive data. Failing to comply with these regulations can result in significant fines and reputational damage. Regular access reviews help organizations stay compliant and provide auditors with evidence of diligent oversight.
- 3️⃣ Mitigating Insider Threats: Insider threats—whether intentional or unintentional—are one of the leading causes of security breaches. Employees with excessive access can accidentally or maliciously expose sensitive data, leading to financial and reputational loss. Conducting user access reviews helps to minimize insider threats by ensuring that access levels are appropriate and by detecting potential issues early on.
- 4️⃣ Enhancing Operational Efficiency: By streamlining access rights, organizations can improve efficiency and reduce complexity within their systems. Over-provisioned users can cause bottlenecks and create unnecessary operational challenges. Regular access reviews ensure that only the right people have the appropriate level of access, reducing complexity and improving overall efficiency.
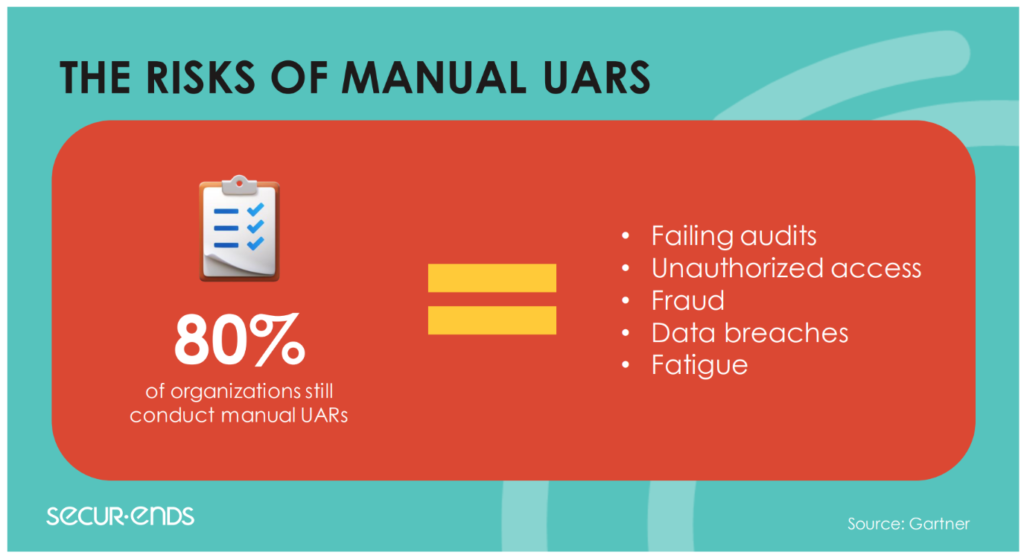
Common Challenges in User Access Reviews
While user access reviews are critical for security and compliance, they are not without challenges. Here are some common issues organizations encounter:
- 👎 Manual Processes and Human Error: Many organizations still rely on manual processes, such as spreadsheets, to conduct access reviews. This approach is time-consuming, error-prone, and inefficient. The more users and systems an organization has, the more difficult it becomes to manage access reviews manually.
- 👎 Incomplete or Inaccurate Data: Access reviews require accurate, up-to-date information about users, roles, and permissions. In many cases, organizations struggle to maintain comprehensive data across various systems, making it difficult to perform thorough reviews.
- 👎 Lack of Visibility Across Systems: Many organizations have multiple systems, applications, and databases with different access control mechanisms. Without a unified view, conducting a comprehensive review becomes difficult, as access rights may be scattered across various platforms.
- 👎 Role Creep: Role creep occurs when users accumulate access privileges over time without their old privileges being revoked. This can happen as employees move between roles, take on temporary assignments, or are granted additional access for special projects. Without regular reviews, role creep can go unnoticed, leading to over-provisioned users and increased security risks.
- 👎 Audit Fatigue: As compliance standards become more stringent, organizations are under pressure to provide evidence of their user access reviews for auditors. Without automation and clear reporting, this process can quickly become overwhelming, leading to audit fatigue.
Steps to Conducting Effective User Access Reviews
Now that we’ve outlined the importance of user access reviews and the challenges organizations face, let’s walk through the steps involved in conducting an effective review process.
1. Define the Scope of the Review
The first step in conducting a user access review is to define its scope. This involves determining which systems, applications, and data repositories will be included in the review. Not all systems require the same level of scrutiny, so it’s important to prioritize based on risk.
- Critical Systems: Focus on high-risk systems first, such as financial systems, customer databases, HR platforms, and cloud environments.
- Data Sensitivity: Identify systems that handle sensitive data, such as personally identifiable information (PII), intellectual property, or financial data.
- User Categories: Differentiate between employee, contractor, and third-party access. Each group may require different review processes.
By narrowing the scope, you can ensure a more focused and manageable review process.
2. Compile User and Access Data
Once you’ve defined the scope, the next step is to gather a comprehensive list of users and their access rights for the systems being reviewed. This includes:
- Users: Gather data on all users with access to the targeted systems. This could include employees, contractors, and external partners.
- Roles: Collect information on the roles each user holds within the organization.
- Access Rights: Identify the specific access rights or permissions each user has for each system.
Many organizations struggle with this step due to scattered data. Tools that consolidate access information from multiple systems into a single view can significantly simplify the process.
3. Review and Validate Access
Once you’ve compiled user access data, the next step is to review and validate it. This process involves comparing each user’s access rights against their job responsibilities to ensure that they have the appropriate level of access.
- Work with Department Heads: Collaborate with department managers and system owners to validate user access. These stakeholders are often best positioned to determine whether access levels are appropriate based on each user’s role.
- Check for Role Creep: Review users who have access to multiple systems and roles to ensure that role creep has not occurred. If users have accumulated access privileges they no longer need, those privileges should be revoked.
- Identify Dormant or Inactive Accounts: Remove or disable accounts that belong to former employees or are no longer in use.
4. Revoke Unnecessary Access
After identifying users with excessive or outdated access, the next step is to revoke these permissions. It’s important to approach this step carefully to avoid disrupting business operations. Use a phased approach to ensure that any changes made do not negatively impact productivity.
- Least Privilege Principle: Ensure that access is granted based on the principle of least privilege, meaning that users should have the minimum level of access necessary to perform their job functions.
- Document Changes: Maintain detailed records of any access rights that are modified or revoked. This is important not only for security purposes but also for compliance audits.
5. Document the Process
Thorough documentation is critical for both internal record-keeping and external audits. After completing a user access review, document all the actions taken, including:
- Systems and data repositories reviewed
- List of users and their access rights
- Access rights that were validated, revoked, or modified
- Approval from department heads or stakeholders
- Any issues identified during the review process
This documentation provides a clear audit trail and demonstrates that your organization is taking proactive steps to manage access and maintain compliance.
6. Generate and Distribute Reports
After the access review is completed and documented, generate reports that outline the findings and actions taken. These reports are crucial for:
- Auditors: Providing evidence of compliance with regulatory requirements.
- Leadership: Ensuring executives are informed of potential security risks and compliance gaps.
- IT Teams: Highlighting any areas that need improvement or further attention.
Automated tools can simplify the reporting process by generating comprehensive reports with just a few clicks, saving time and reducing human error.
7. Automate Future Reviews
One of the most effective ways to streamline user access reviews is by automating the process. Manual reviews are labor-intensive, prone to errors, and difficult to scale as your organization grows. Automation tools can help:
- Streamline Data Collection: Automatically gather user access data from multiple systems and consolidate it into a unified view.
- Schedule Recurring Reviews: Set up regular, automated reviews (e.g., quarterly or biannually) to ensure that access rights are always up-to-date.
- Real-Time Alerts: Receive real-time notifications when unusual access patterns are detected, allowing for immediate investigation and resolution.
- Audit-Ready Reporting: Generate detailed, audit-ready reports with the click of a button, reducing the manual burden on your IT and compliance teams.

Best Practices for Conducting User Access Reviews
Conducting effective user access reviews requires careful planning and execution. Here are a few best practices to ensure that your reviews are efficient, accurate, and impactful:
- 💎 Conduct Reviews Regularly: Regular reviews are essential for maintaining security and compliance. Depending on the size and complexity of your organization, you may choose to conduct access reviews quarterly, biannually, or even more frequently for high-risk systems.
- 💎 Involve Key Stakeholders: User access reviews should not be conducted in isolation by the IT or security teams. Involve department heads, HR, compliance officers, and system owners to ensure that all access rights are validated by individuals who understand each user’s job responsibilities.
- 💎 Use Role-Based Access Control (RBAC): Implement role-based access control (RBAC) to simplify access management. By assigning permissions based on predefined roles, rather than individual users, you can reduce complexity and make reviews more straightforward.
- 💎 Ensure Access to Cloud Environments: With the growing adoption of cloud services, it’s important to include cloud environments in your access reviews. Many organizations have a hybrid IT infrastructure with both on-premise and cloud-based systems. Ensure that cloud accounts and permissions are reviewed along with traditional on-premise systems.
- 💎 Monitor for Anomalies: In addition to periodic reviews, monitor user access for unusual activity or anomalies. Anomalies such as users accessing systems outside their normal hours or unusual login locations may indicate potential security threats and should be investigated promptly.
- 💎 Leverage Automation: Automation is key to making user access reviews more efficient, accurate, and scalable. Tools like SecurEnds IGA can streamline the process by automating data collection, workflows, reporting, and alerts. Automation not only saves time but also reduces the risk of human error.
Automate User Access Reviews with SecurEnds
User access reviews are a critical component of any organization’s security and compliance strategy. By regularly reviewing and validating user access rights, organizations can reduce the risk of security breaches, prevent insider threats, and ensure compliance with regulatory standards.
While the process may seem complex, following the steps outlined in this guide and adopting best practices can significantly simplify the process. Moreover, leveraging automation tools like SecurEnds IGA can help organizations overcome common challenges, such as manual errors, lack of visibility, and audit fatigue, while improving overall security and operational efficiency.
If you’re ready to take your user access review process to the next level, consider implementing a solution that automates and streamlines these tasks, helping you stay secure and compliant in today’s dynamic digital landscape.
✍ Article by Dino Juklo