Access Request
Identity Security & Compliance with Access Request
Intuitive Request Submission
Provide users with a modern and user-friendly interface that guides them through the process of submitting access requests for various applications. This interface is designed to minimize confusion and maximize user efficiency, ensuring that even non-technical users can easily request the access they need.
Application Catalog
Maintain an up-to-date and organized catalog of available applications within the organization. By presenting resources in a clear and categorized manner, the module makes the request process more efficient and user-friendly.
Automated Approval Workflows
Accelerate the traditionally time-consuming access approval process by implementing automated workflows. As access requests are submitted, the module intelligently routes them to the appropriate approvers based on preconfigured rules. This automation eliminates bottlenecks, reduces manual intervention, and speeds up access provisioning.
Request, approve, provision and de-provision user access to on-prem or cloud applications for easier user onboarding, off boarding and self-service.
Create Identity Profiles
Pre-built templates in SecurEnds ILM enable streamlined identity management across the entire lifecycle. These attribute-based profiles, tailored for various workforce types (employees, contractors, RPA accounts, service accounts), simplify identity creation by using attributes like title, location, and department. This ensures efficient and consistent identity governance across your organization.
Request Access
SecurEnds simplifies the access request process with self-service options for both SSO-enabled and non-SSO-enabled applications. Users can easily submit access requests through an intuitive interface, ensuring a seamless experience regardless of the application type. This self-service capability empowers users to obtain necessary access quickly while maintaining compliance with security policies.
Provision Access
SecurEnds offers a user-friendly solution for self-guided role creation based on specific access requirements. In just a few clicks, users can easily assign application access, including detailed permissions within the application. This streamlined provisioning process enhances operational efficiency while ensuring compliance. With SecurEnds, critical access can be managed enabling teams to work seamlessly and securely.
Pending Requests
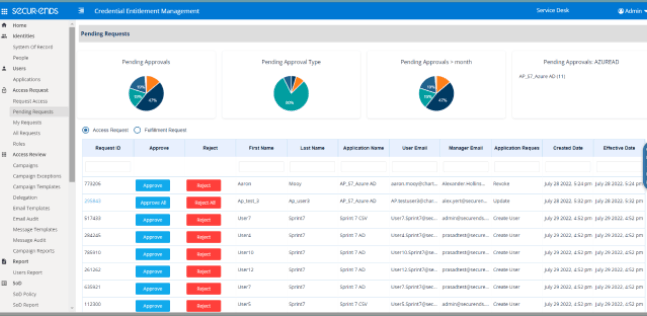
SecurEnds simplifies access management by allowing administrators to approve or revoke end-user access to requested applications with ease. This centralized solution ensures timely decision-making, maintaining security while minimizing access delays. With SecurEnds, organizations can efficiently manage pending requests, ensuring that only authorized users gain access to essential applications. Keep your environment secure and compliant with seamless request management.
Life cycle management
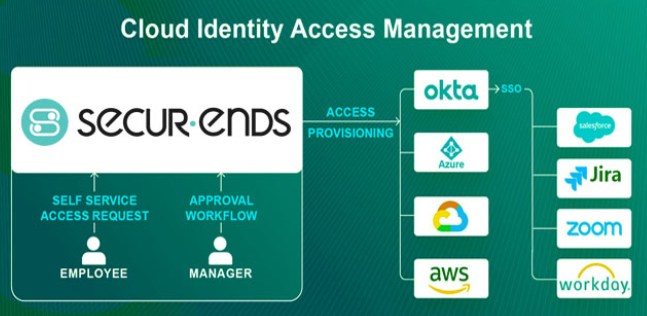
SecurEnds automates user provisioning for critical lifecycle events such as onboarding, offboarding, and internal transfers. By associating identity profiles with role-based profiles, the platform streamlines provisioning and deprovisioning processes, ensuring timely and accurate access updates. Simplify identity lifecycle management and maintain security with automated workflows, reducing manual effort and minimizing risks across your organization.
USE CASES

Employee Onboarding
Role Changes & Promotions

Temporary Access
