Supported Features
SecurEnds application supports the following OIDC feature:
- Service Provider (SP)-Initiated Authentication (SSO) Flow
Step 1: Add SecurEnds Application in Okta dashboard
- Within the Okta Admin dashboard select the Applications link in the header of the page
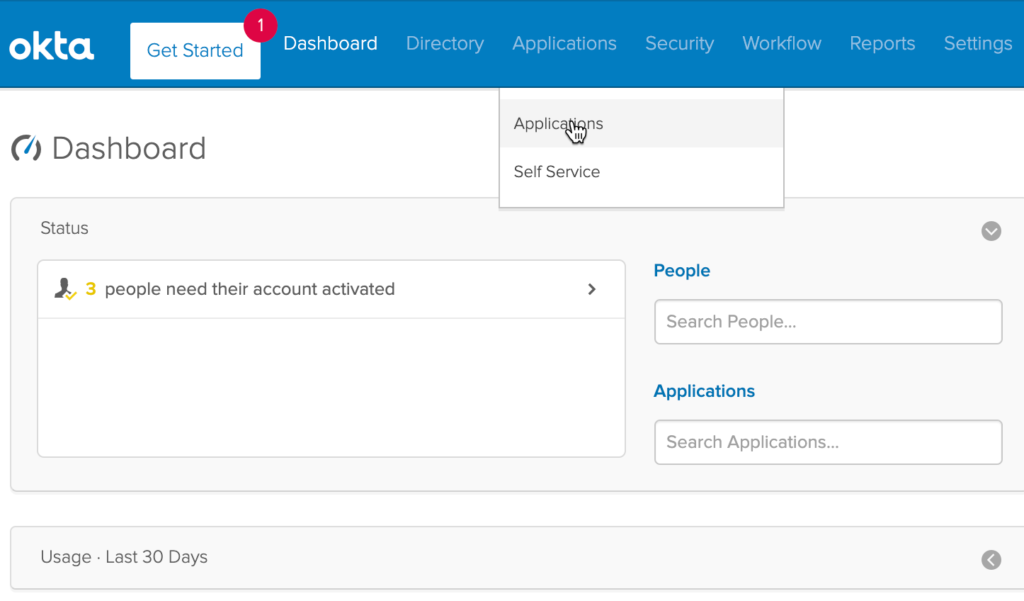
- Select the Add Application button on the Application screen
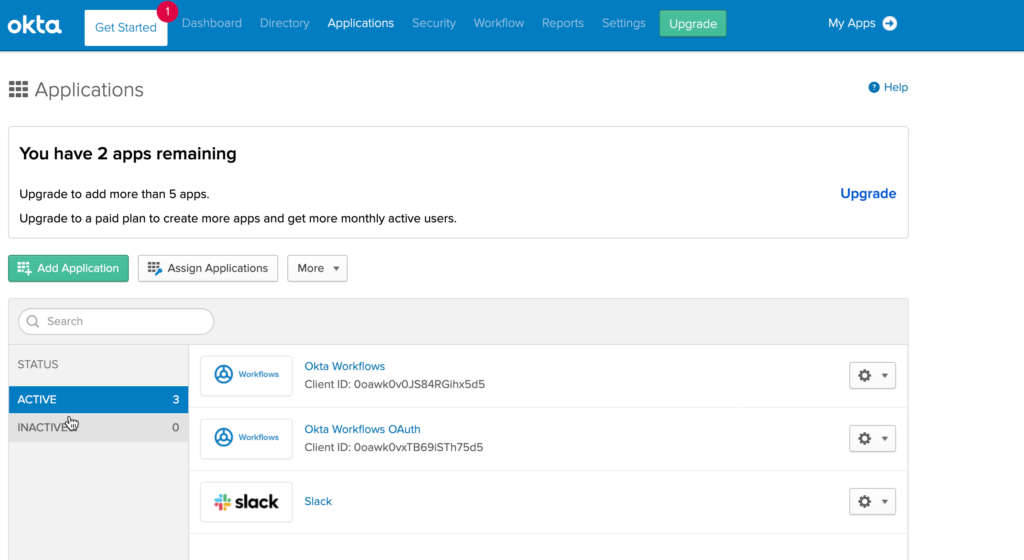

- Search for “SecurEnds” application and select the SecurEnds application from the results shown
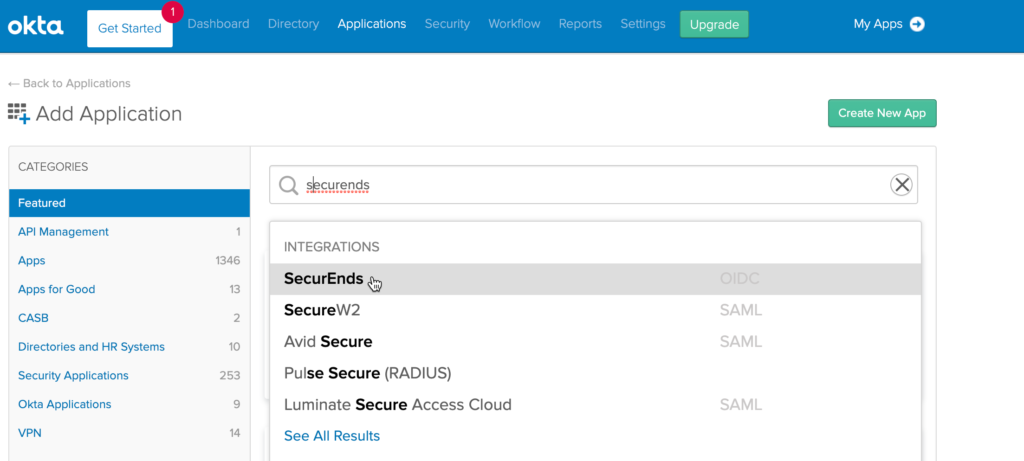
- Select the Add button on the SecurEnds screen
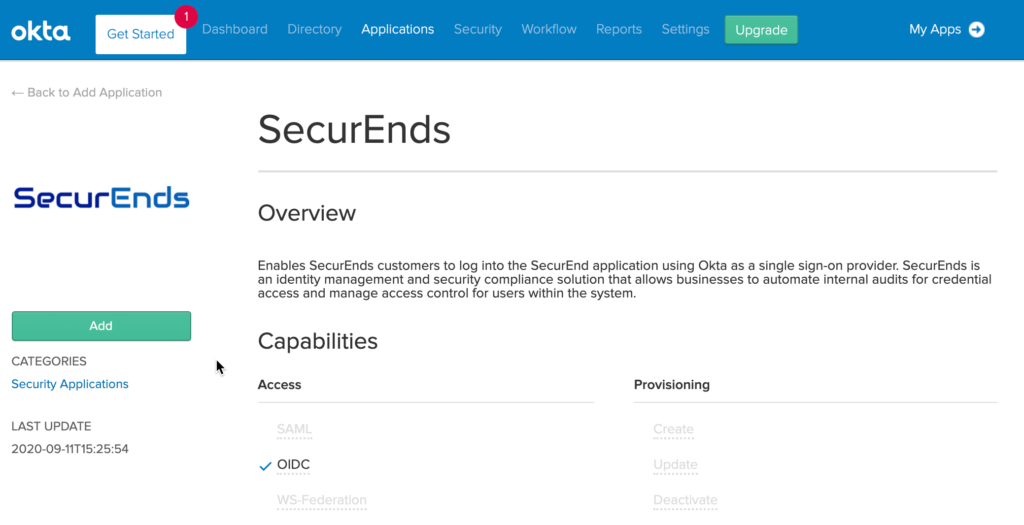
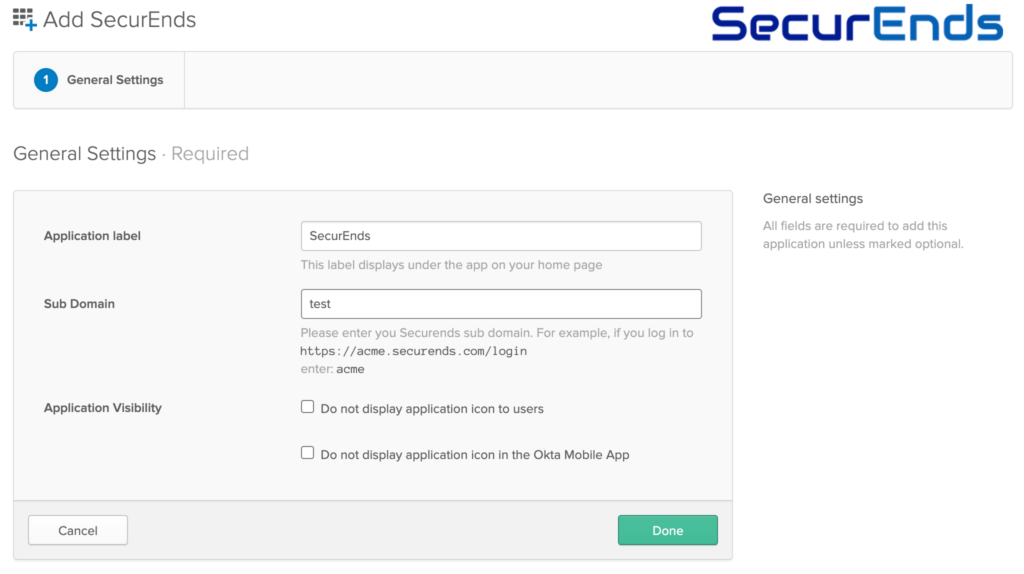
- Provide Application label and Sub Domain details and select the Done button
- Example Application Label
- SecurEnds
- Example Sub Domain
- If the URL is “https://test.securends.com/” then the Sub Domain will be “test”, the first part of the URL prior to “.securends.com”
- You will then be redirected to view the SecurEnds application details
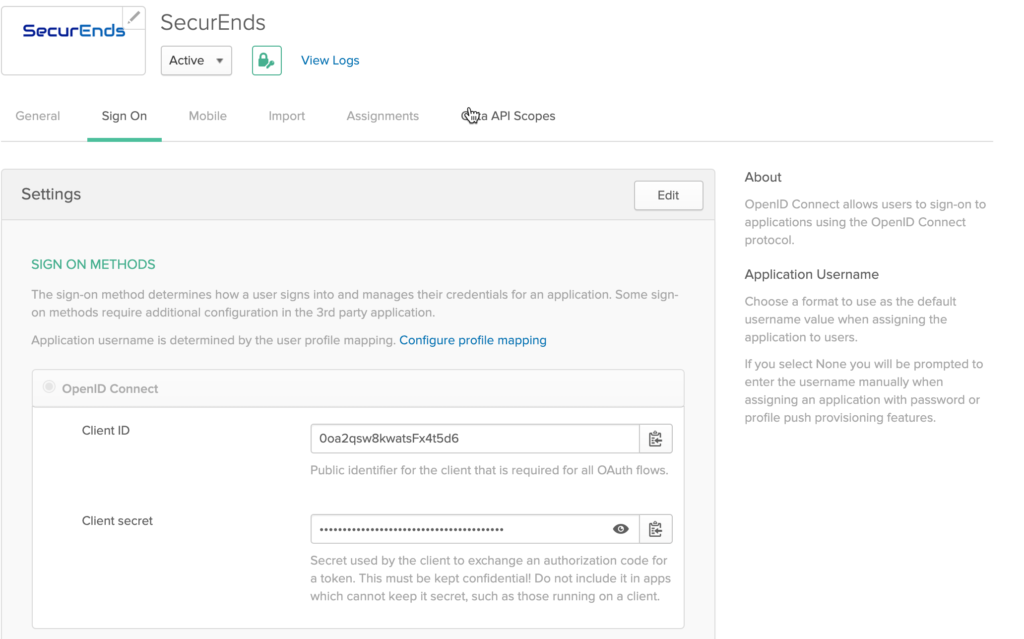
- Select the Sign On tab, copy the Client ID and Client secret values. These values will need to be provided to your SecurEnds Implementation Consultant to be configured within your organizations SecurEnds instance
- The following information will need to be provided to enable Okta SSO
- Client ID
- Issuer
- Client Secret
- The following information will need to be provided to enable Okta SSO
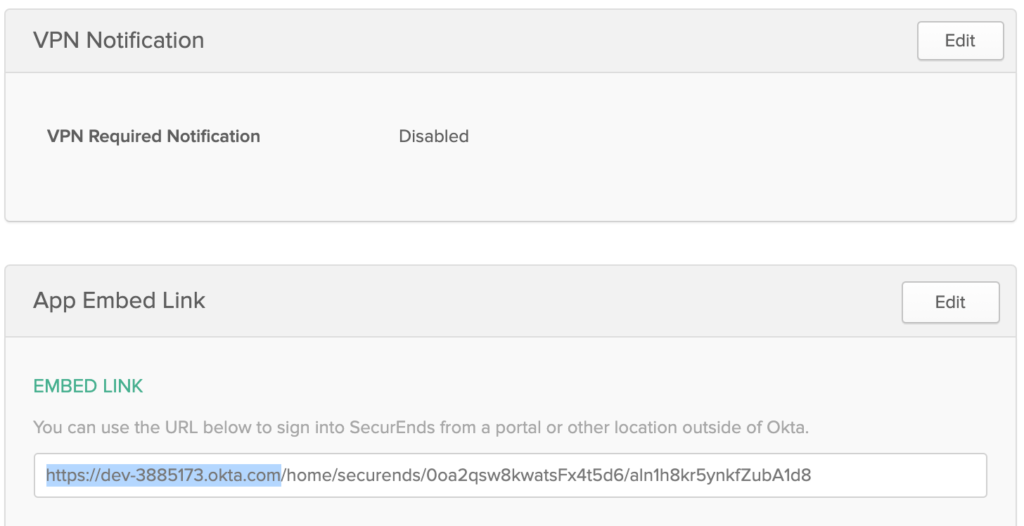
- Once the application is created, go to General Tab
- Navigate to the App Embedded Link Section and copy the URL up until “okta.com”
- This will be the Issuer URL required to enable your organization’s SSO in SecurEnds
- Example Issuer URL: https://dev-577759.okta.com
- This will be the Issuer URL required to enable your organization’s SSO in SecurEnds
- Please provide the following information to your SecurEnds Implementation Consultant to be configured within your organizations SecurEnds Instance
- Client ID
- Client Secret
- Issuer
Test Your Integration
Step 2: Assign Users
First you must assign your integration to one or more test users in your org:
- Select the Assignments tab
- Select Assign and then select either Assign to People or Assign to Groups
- Enter the appropriate users or groups that you wish to enable Single Sign-On into your application, and then select Assign for each
- For any users that you added, verify the user-specific attributes, and then select Save and Go Back
- Select Done
Test Single Sign-On
- Sign out of your administrator account within your development org by selecting Sign out in the upper-right corner of the Admin Console
- Sign in to the Okta End-User Dashboard as the normal user who was assigned the SecurEnds integration
- In your dashboard, select the Okta tile for the integration and confirm that the user is signed into SecurEnds application
Notes
Users can access SecurEnds application using OIDC features in the following ways:
- Customer can login to their okta org url
- After authentication, customer can click on the SecurEnds App available in the dashboard and will be redirected to the SecurEnds application
- Access SecurEnds instance url directly
- Customer will be redirected to their okta org for authentication and after authentication customer will be redirected back to SecurEnds application
Troubleshooting and Tips
If you run into issues with your sign-in process, you can try the following to troubleshoot the issues:
- In the Admin Console of your Okta development org, navigate to Reports > System Log and examine any failure messages reported
- Open the developer console of your web browser and examine any status messages related to your authentication request. The console errors have status codes in the 4XX range. Investigate and resolve any error messages generated by your sign-on request
- Please reach out to the SecurEnds Implementation Consultant in case further help is required