SecurEnds application is built using Spring Boot. Spring Boot makes it easy to create stand-alone, production-grade Spring based Applications that you can “just run”. We have multiple instances of Spring Boot. The end users interact with SecurEnds through web-based User Interface, which communicates over HTTPS. The UI is developed by using React JS.
SecurEnds Application is typically deployed on AWS EC2 Instance but can be deployed on other IAAS such as Azure. We employ Elastic Load Balancing to automatically distribute incoming traffic across multiple targets, such as EC2 instances, containers, and IP addresses, in one or more Availability Zones. To access AWS , IAM policy with MFA (Multi Factor Authentication) is used and Rotate Access Keys are enabled. MFA, or extra authentication controls, is used to combat increasing levels of identity theft.
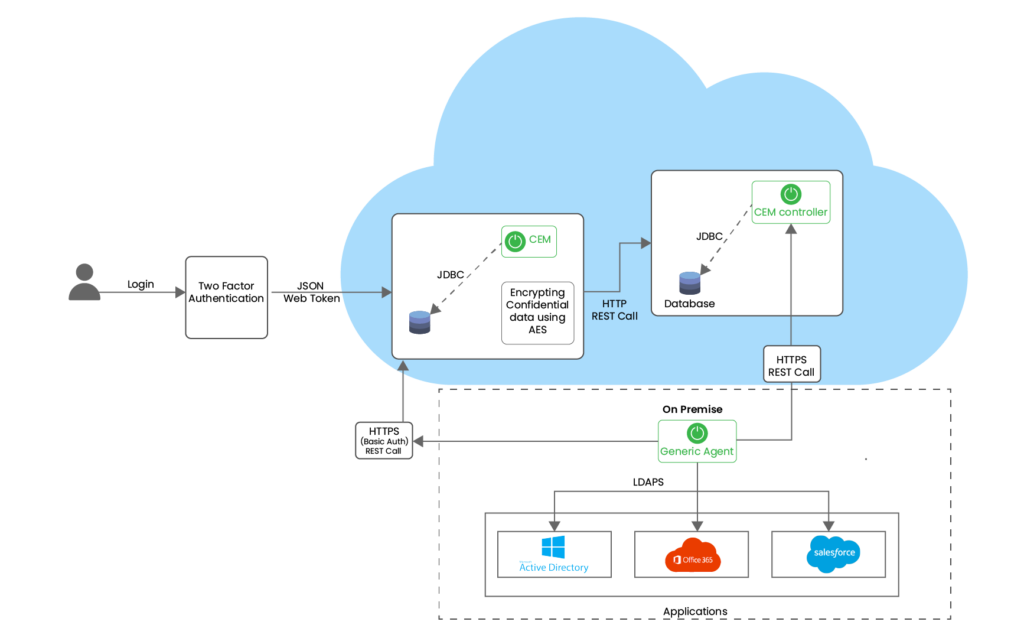
The Data Base Server is deployed on AWS RDS. We have two RDS MySQL instances: CEM and CEM Controller. The CEM Controller is a bridge between CEM Application and Agent(Connectors) for event management and data push management. Amazon RDS encrypted DB instances provide an additional layer of data protection by securing data from unauthorized access to the underlying storage. It handles authentication of access and decryption of data transparently with a minimal impact on performance. Amazon RDS encrypted DB instances use the industry standard AES-256 encryption algorithm. Connection between On Premise and Cloud Instances are secured. Generic Agent Installation is required to connect SecurEnds to an on- premise Application Connector.
Key Components of SecurEnds
- SecurEnds allows administrators to perform typical system administration functions including Onboarding SOR/Applications, Campaign creations and performing User Access Reviews.
- File Uploads, Connectors and Flex Connectors are used to interact with other IT systems.
- Identity governance controls user permissions on resources and provides a clear picture of allowed access and potential security risks.
- SecurEnds gives access to external auditors to view proof of review completion.
- Campaign reports houses all data related to the campaigns.
- Identity Analytics features Identity Mind map, Application Mind Map and Entitlement Mind Map which shows the graphical representation of Identities, Applications, Credentials and Entitlements.