Identity Alerts Intelligence
Identity Alerts & Intelligence
Identity governance enforces access life cycle management process.
Identity Governance & Administration
SecurEnds IGA product addresses automating access provisioning and de-provisioning for employees, customers, and partners onboarding and off-boarding. The product manages the identity access management for Microsoft Dynamics, AX, Active Directory, O365, SAP, Google Suite, and Databases. It manages user access permissions for employees, partners, and customers in regards to access approval management. Identity governance enforces access life cycle management processes, such as granting access and periodically reviewing access privileges, and revoking access privileges when a user is terminated. The process enables a centralized system where one can manage user access privileges and entitlements in one central place.
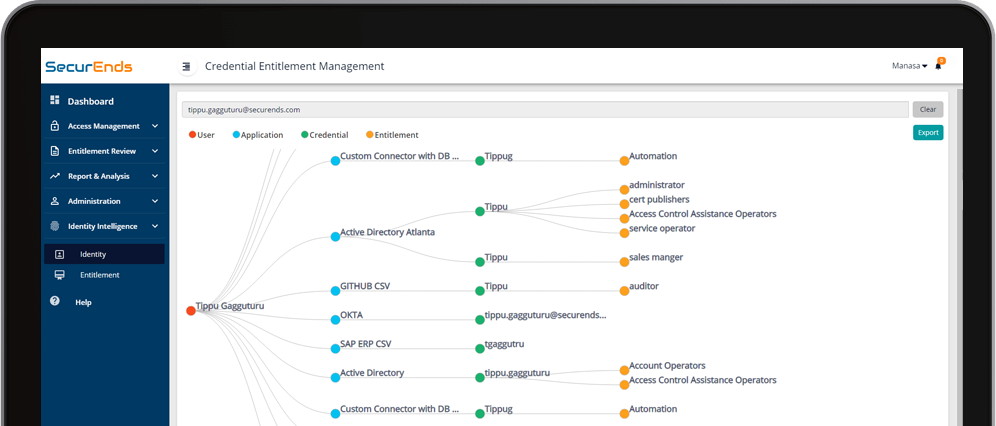
Identity governance for access certification and reducing the risk of excessive access
Companies face a multitude of security compliance regulations and governances. The core of security compliance is access control. It is challenging to manage access control compliances for applications, databases, network devices, and cloud apps. Most companies are affected by regulatory compliance obligations and are subject to industry regulations, such as HIPAA, PCI, Sarbanes-Oxley (SOX) or GDPR.
Companies have extreme difficulties in organizing and executing user access reviews to meet various compliances, such as PCI-DSS, HIPAA, FISMA, and GLBA. SecurEnds SecurIGA is identity governance and access control compliance product that integrates any system in the enterprise with access control workflow by integrating with endpoints such as Active Directory, SharePoint, Office 365, Salesforce, SAP, AWS, Azure, Google Drive, Dropbox, GitHub, Jira, ServiceNow, etc.
This product can be configured to extract user credentials and entitlement details from endpoints both manually and automatically. Additionally, it matches with the HR user data to create IAM users in a centralized repository for managers to review. It provides identity governance to users’ access reviews and provides updates to the user access privileges to complete the access management workflow.
Key features of the product
Disruptive product for Identity and Access Governance for all enterprises
Manage and track access provisioning for new users
Limit users and access points to confidential data
Consolidated view of user access rights
Periodic user access and entitlement review
Eliminate unauthorized or orphaned users
Manage user access de-provisioning
User access certification
Provide evidence of compliance in the audit process
Easy to leverage the product for short term projects including PCI, SOX or HIPAA compliance
Evaluate access controls for potential target companies during M&A
Key product differentiating factors
Our product closes the gap in your enterprise with Identity governance and compliance for systems that are integrated as well as those that are not integrated to Identity Access Management.
Most Identity governance solutions need 18-24 months installation/customization and cost millions of dollars compared to our solution
Our product can be installed and configured in few weeks.
Access Control Compliance product manages the access control compliance for applications, databases, network devices and cloud apps. We offer on-premise and cloud offering of our products. Our products will be configured to provide solution for your organization.
Schedule a Product Demo
Submit your information and a technical representative will schedule a demo.















