User Access Reviews: The Ultimate Guide for Ensuring Security & Compliance
User Access Reviews: The Ultimate Guide for Ensuring Security & Compliance

Ensuring that the right individuals have access to the right resources is crucial. User access reviews (UARs) play a pivotal role in maintaining security, compliance, and overall operational efficiency. But what exactly are user access reviews, and why are they so important? This guide will take you through the essentials of UARs and how implementing them can protect your organization from potential security threats and compliance issues.
What are User Access Reviews?
User access reviews are periodic checks conducted by an organization to ensure that employees, contractors, or partners have appropriate access to systems, data, and other resources. These reviews involve examining the access rights of users, identifying any unauthorized or outdated permissions, and making necessary adjustments.
Why Are User Access Reviews Essential?
- ⭐ Enhancing Security: User access reviews help to identify and revoke unnecessary or outdated access, reducing the risk of unauthorized data access and potential breaches.
- ⭐ Ensuring Compliance: Regulations such as GDPR, HIPAA, and SOX require organizations to regularly review user access to sensitive data. Non-compliance can lead to hefty fines and damage to reputation.
- ⭐ Operational Efficiency: By streamlining access rights, organizations can reduce complexity and improve operational efficiency. This ensures that only authorized personnel have access to critical systems and data.
- ⭐ Mitigating Insider Threats: Insider threats are a growing concern for many organizations. Regular access reviews can help detect unusual access patterns and prevent potential security incidents from within.
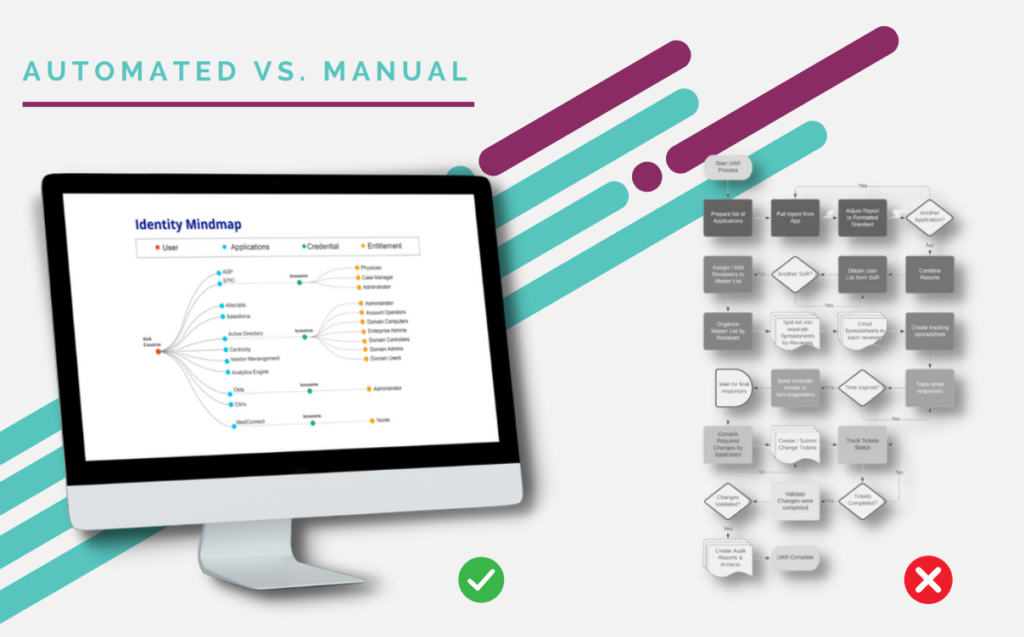
Manual vs. Automated User Access Reviews
Manual user access reviews involve a labor-intensive process where IT administrators or compliance officers manually review each user’s access rights, often using spreadsheets or basic tools. While this approach can work for small organizations, it becomes increasingly inefficient and prone to errors as the company grows, leading to missed access violations and compliance risks.
On the other hand, automated user access reviews leverage advanced software solutions to streamline the process, reducing human error, saving time, and ensuring that reviews are consistent and thorough. Automation not only enhances accuracy but also allows for more frequent reviews, ensuring that access rights are always up-to-date and aligned with the user’s role, thereby strengthening overall security and compliance efforts.
Key Steps in Conducting User Access Reviews
- 1️⃣ Identify Scope: Determine which systems, applications, and data repositories will be included in the review. This may involve critical systems, cloud platforms, or specific departments within your organization.
- 2️⃣ Compile a List of Users and Access Rights: Gather a comprehensive list of users with access to the identified resources. This list should include their roles, permissions, and the duration of their access.
- 3️⃣ Review and Validate Access: Work with department heads, managers, and IT teams to review the access rights of each user. Ensure that access aligns with the user’s current role and responsibilities.
- 5️⃣ Revoke Unnecessary Access: Identify and revoke any unnecessary or outdated access rights. This step is crucial in minimizing security risks and maintaining a least-privilege model.
- 6️⃣ Document and Report: Document the entire review process, including any changes made. Reporting is essential for compliance purposes and future audits.
- 7️⃣ Automate Future Reviews: Consider implementing automated tools to streamline the user access review process. Automated systems can help reduce human error, save time, and ensure consistent reviews.
How to Choose the Right User Access Review Solution
Choosing the right user access review solution requires careful consideration of several key factors. Start by assessing your organization’s size, complexity, and specific compliance requirements to ensure the solution can scale and meet regulatory standards. Look for features like automation, real-time monitoring, and robust reporting capabilities, as these can significantly reduce manual workloads and improve accuracy.
Integration with your existing IT infrastructure is crucial, so opt for a solution that supports seamless integration with your current systems, applications, and identity management tools. User-friendliness and customer support are also important—ensure that the solution is easy to implement and use, and that the vendor offers reliable support to assist with any challenges.
Finally, consider the cost relative to the value it provides, balancing upfront investment with long-term benefits like enhanced security, reduced compliance risks, and operational efficiency.
Best Practices for Effective User Access Reviews
- 👉 Regular Reviews: Conduct user access reviews at least quarterly, or more frequently for high-risk environments.
- 👉 Involve the Right Stakeholders: Include IT, HR, department heads, and compliance officers in the review process to ensure comprehensive oversight.
- 👉 Leverage Technology: Utilize access management and governance tools to automate and simplify the review process.
- 👉 Monitor and Adjust: Continuously monitor access rights and make adjustments as roles and responsibilities change within the organization.
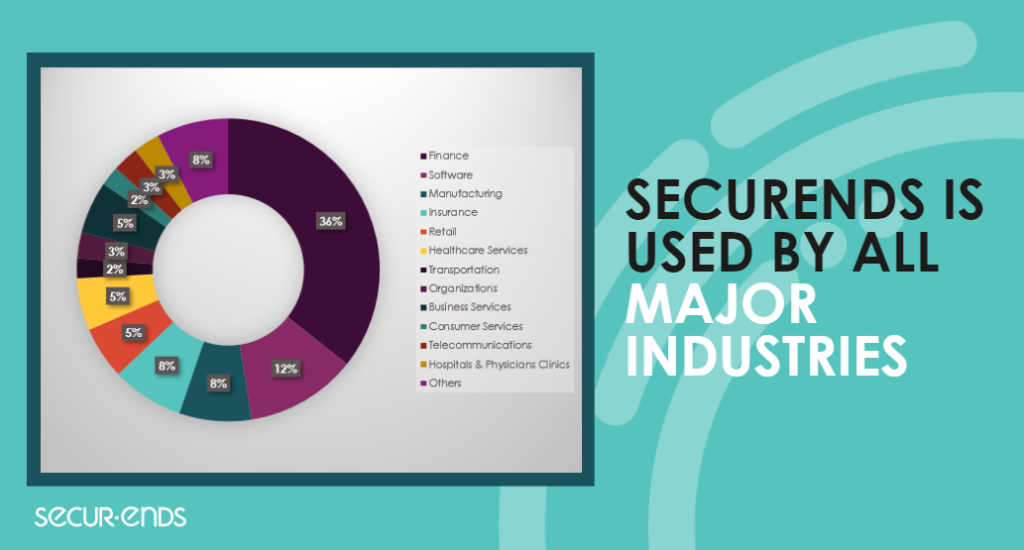
The Role of SecurEnds in User Access Reviews
At SecurEnds, we understand the complexities of managing user access in today’s dynamic IT environments. Our advanced Identity Governance and Administration (IGA) solutions streamline the user access review process, making it easier for organizations to manage access rights, ensure compliance, and enhance security.
With SecurEnds, you can automate user access reviews, generate detailed audit reports, and mitigate risks associated with excessive or inappropriate access. Our platform integrates seamlessly with your existing infrastructure, providing a scalable solution that grows with your organization.
Upgrade Your User Access Review Process
User access reviews are a critical component of any organization’s security and compliance strategy. By regularly reviewing and adjusting user access rights, you can protect sensitive data, comply with regulations, and reduce the risk of security incidents.
Whether you’re a small business or a large enterprise, implementing an effective user access review process is essential for safeguarding your digital assets. Ready to take your user access reviews to the next level? Contact SecurEnds today to learn how our solutions can help you secure your organization and ensure compliance.
✍ Article by Dino Juklo