Application Access Request
Application Access Request
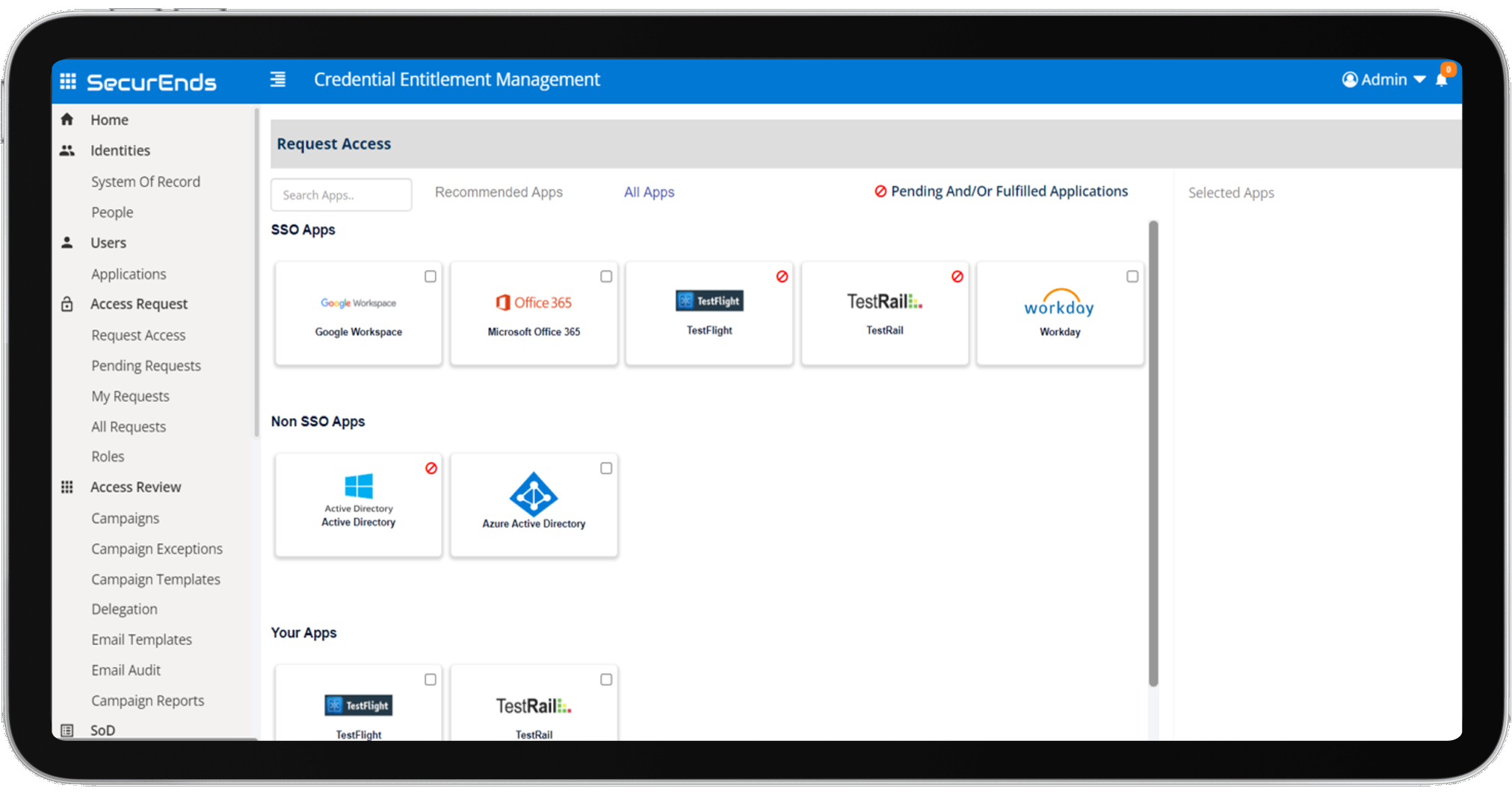
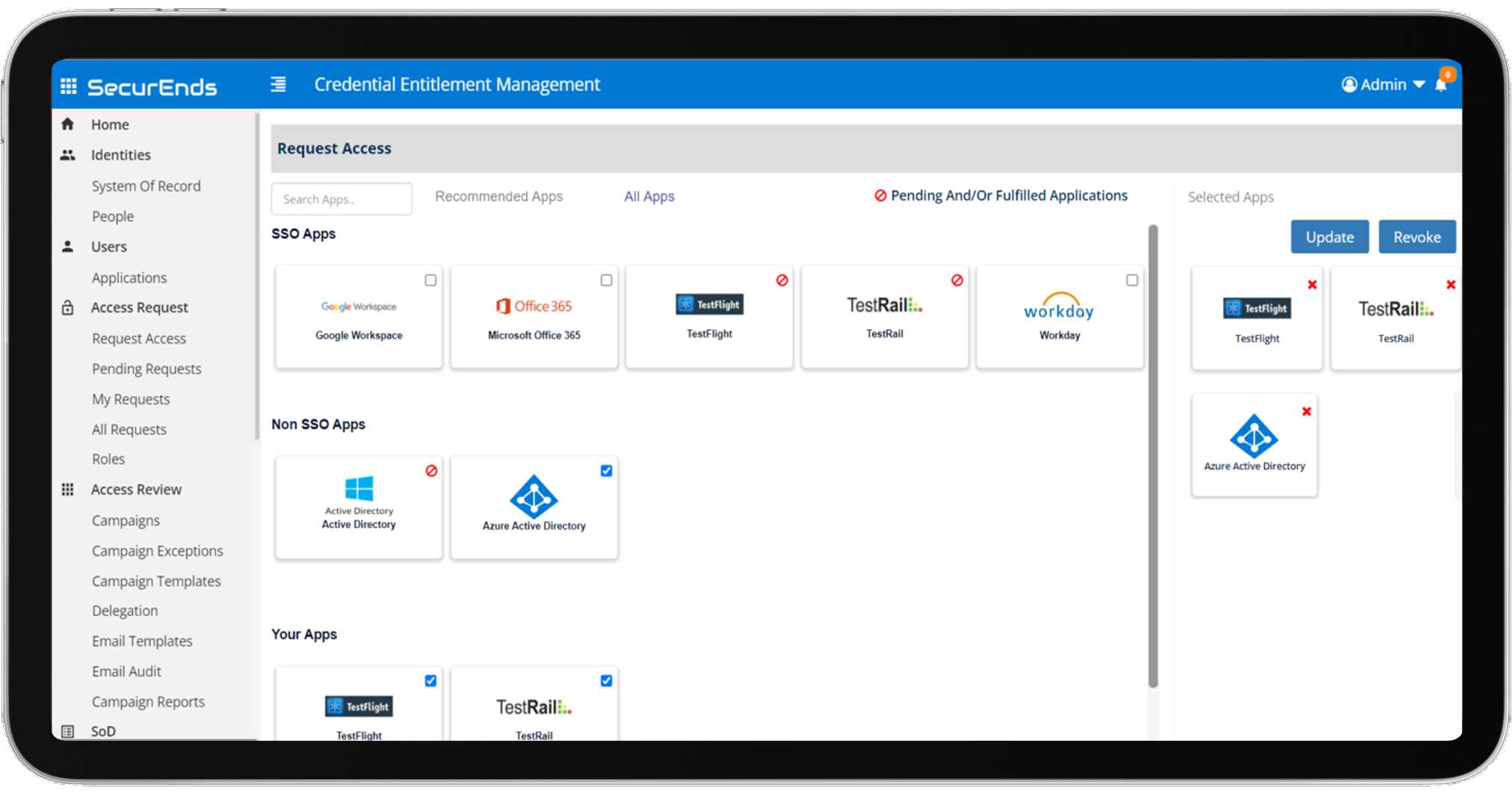
SecurEnds application access request extends birthright provisioning to deliver access request capability for users needing additional access by automating self-request and approval workflow
Streamlining the JML Lifecycle with SecurEnds
In every organization, managing user access is an ongoing challenge as employees and contractors move through the Joiners, Movers, and Leavers (JML) lifecycle. The process begins when a new user is added to the company’s system of record, such as an HR system for employees or Microsoft Azure AD for contractors. Initially, users are granted “birthright” access to basic applications and data based on their role. However, as users progress within the organization or take on new responsibilities, they often need additional access that falls outside their default permissions. This can be a cumbersome process in environments without a centralized solution, resulting in delays and potential security risks.
SecurEnds Application Access Request
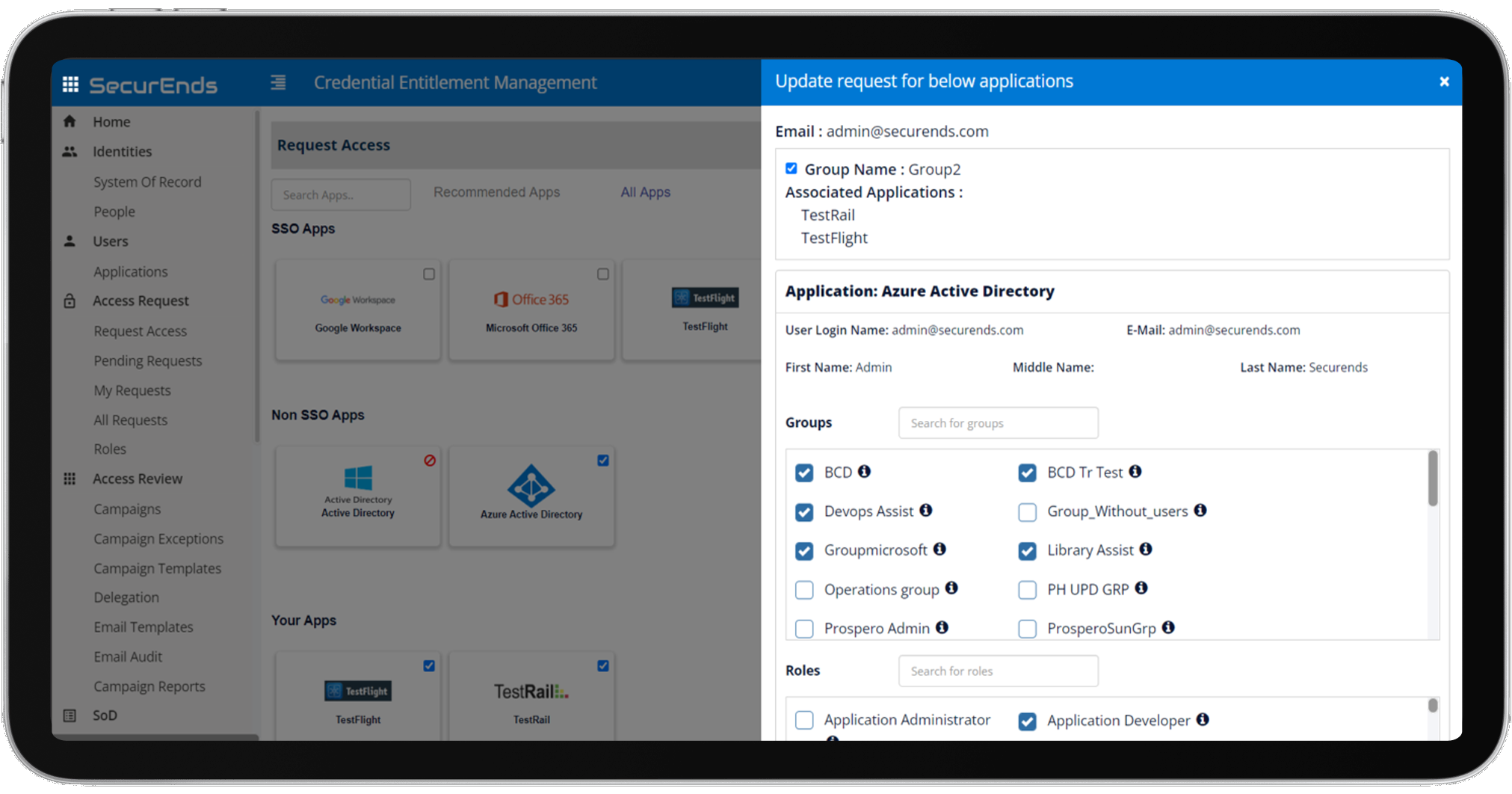
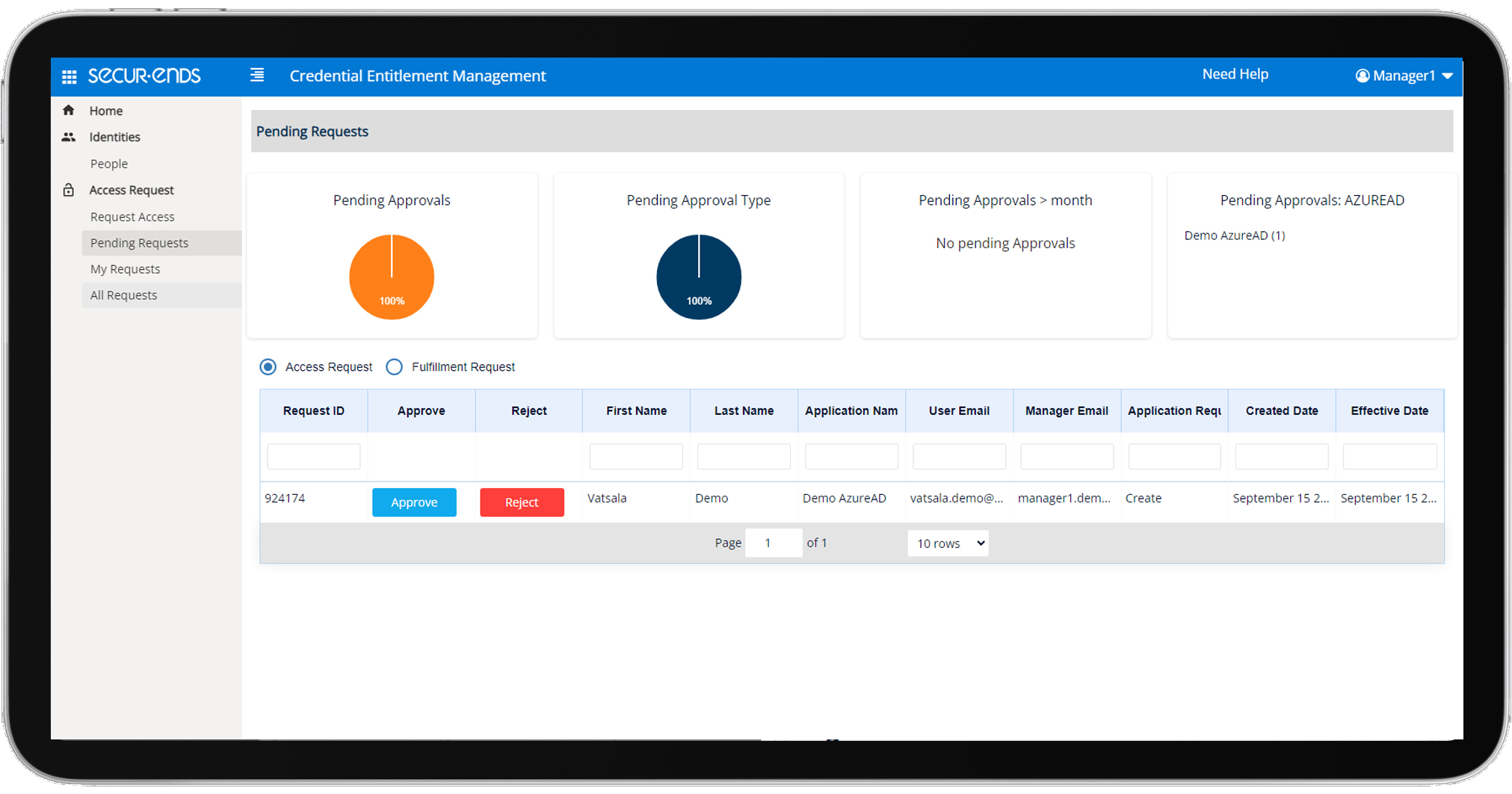
SecurEnds Application Access Request simplifies this by providing a centralized access request management system. This solution enables users to easily request additional access to IT assets, while automating approval workflows to ensure timely provisioning. In highly regulated industries, where compliance and oversight are crucial, SecurEnds ensures that access to critical applications is approved by line managers or application owners. This not only facilitates adherence to the principle of least privileged access but also significantly reduces the risk of unauthorized access, which could otherwise lead to security breaches.
Enhancing Access Governance and Compliance
With SecurEnds Application Access Request, organizations benefit from more than just a streamlined request process. By integrating the solution with Identity Lifecycle Management (ILM), companies can improve productivity and maintain comprehensive auditability across all user access activities. The automated workflows eliminate manual errors and provide real-time tracking, ensuring that all requests, approvals, and access changes are logged for compliance purposes. For organizations subject to stringent regulations, this provides peace of mind knowing that they can demonstrate effective access control and governance during audits, reducing the risk of non-compliance and associated penalties.